How to send sensitive information via email
Email alone can’t protect your most sensitive data. Find practical steps and solutions that keep your business and clients safe from fraud.
.png)
Michelle Artreche
9 minutes
Cybersecurity
Nov 12, 2025
Dec 5, 2025
Clicking send on wire instructions can be nerve-wracking, especially when you immediately wonder if they reached the right person. That moment shows a real risk.
Email is important for business, but it is also the top gateway for breaches and fraud. The FBI reports $16 billion in cybercrime losses in 2024, a 33% increase from the previous year. In this guide, you will learn how to identify sensitive information, understand email risks, and take practical steps to protect your messages and your business.
Types of sensitive information businesses send by email
You can’t protect what you don’t recognize as sensitive. Knowing the types of information that need extra care is the first step in keeping your business and clients safe.
Now that you know what sensitive information is, it’s important to understand the risks of sending it by email. Recognizing these threats is key to protecting your data and preventing costly mistakes.
8 risks of sending sensitive information by email
Email is one of the most common tools in business, but also one of the riskiest ways to share sensitive information.
Even with filters and firewalls, everyday messages can expose you to costly fraud and data loss. Sending sensitive information via email carries risks. Knowing the main risks helps you protect sensitive information before it’s too late.
1. Phishing attacks
Fraudsters impersonate trusted contacts—like executives, vendors, clients, or partners—to trick employees into giving up sensitive information or passwords. Their messages look convincing and use urgency to push people to act fast. CertifID data shows one in four consumers reported receiving suspicious communications during their real estate transactions, with 58% appearing to come from real estate agents.
2. Business email compromise (BEC)
BEC is the most damaging email threat in business today. The FBI reports 21,442 complaints accounting for nearly $2.8 billion in losses.
Fraudsters infiltrate real conversations for weeks before they attack. According to ALTA, in 2022, 17% of title companies sent money to the wrong account because of fraud, and half of them faced fraud more than once. Fraudsters impersonate executives, attorneys, or partners to redirect payments or access confidential data. Watch this video to see how these scams work and what steps you can take to prevent them.
3. Data interception
Unencrypted emails travel through multiple servers before they reach the recipient. This allows fraudsters to intercept them. When someone is monitoring network traffic, especially on public Wi-Fi or unsecured networks, they can capture wire instructions, account numbers, and client data in plain text. These “man-in-the-middle” attacks are invisible to both sender and recipient and often enable future, more sophisticated breaches.
4. Malware and ransomware
Real estate transactions depend on secure digital systems, but one wrong click can put everything at risk. Malicious attachments or links in emails, text messages, or online portals can install software that gives fraudsters access to your systems. Ransomware, a type of malware, a software that steals credentials, monitors activity, or allows remote access. Ransomware locks files until a ransom is paid. In just hours, an infection can spread through networks, halting closings and costing companies hundreds of thousands.
5. Misaddressed emails
Human error is always a risk. Sellers might not remember their account numbers, which leads them to look and write things down at the same time. This practice causes mistakes.
Auto-complete, similar contact names, or a momentary lapse in attention can result in sending confidential data to unintended recipients.
6. Email spoofing and domain impersonation
Fraudsters forge sender addresses to make messages look like they come from trusted sources. For example, an email might appear to be from “Sarah Johnson, Wells Fargo” but it’s actually from sarah.johnson@wel1sfargo-payoffs.com.
Fraudsters register look-alike domains (wellsfargo.com → wel1sfargo.com) and use them across multiple states to make their messages seem more credible. CertifID’s network analysis has uncovered clusters of aliases and domains operating simultaneously across states and, in many cases, linked through shared registrations, similar hosting, or sending patterns — a strong signal of coordinated fraud campaigns.
7. Weak passwords and compromised credentials
Using easy-to-guess or reused passwords make entire inboxes vulnerable. Fraudsters use credential stuffing, taking passwords from one breach and using them to try to access other accounts. Once inside, they can monitor conversations and impersonate the account holder, usually going undetected for weeks.
8. Third-party data retention and storage risks
Email providers store sent messages indefinitely on their servers, increasing the risk if those servers are ever compromised. Cloud-based email adds more possible targets for attacks, extending risk beyond the original message.
While these risks are significant, there are effective ways to reduce them — beginning with stronger authentication, employee training, and using secure communication platforms designed to keep your data safe.

How to send sensitive information via email: 10 best practices
Protecting sensitive information via email requires multiple layers working together. No single solution is enough on its own.
1. Establish clear email security policies
Experiencing just one high-risk transaction can increase a company’s exposure sixfold compared with peer companies, according to CertifID’s State of Wire Fraud data.
Clear, consistent policies help prevent fraud from escalating. They should cover what not to send by email, approved methods to share different types of sensitive data, and set rules for handling financial records, client files, and other confidential documents.
Policies should also cover regulatory requirements like GLBA for financial information, HIPAA for health records, or industry-specific standards. Make sure policies are easy to access and require all employees to review and acknowledge them annually.
2. Require strong passwords and enable multi-factor authentication (MFA)
Passwords should be at least 12 characters and combine uppercase, lowercase, numbers, and symbols.
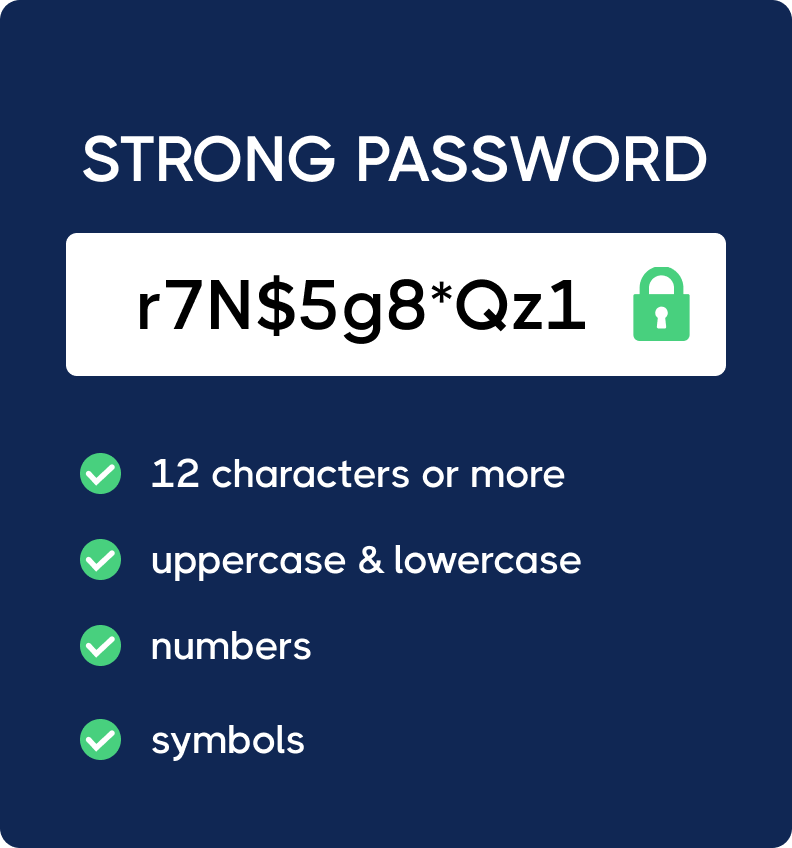
Password managers like LastPass, 1Password, or Dashlane help employees create and store strong, unique passwords for every account, so they don’t have to reuse them or remember dozens of complex passwords. Adding multi-factor authentication (MFA) provides an extra layer of security, which is critical for anyone managing financial transactions.
3. Encrypt emails and attachments
End-to-end encryption ensures that only intended recipients can access sensitive information. Use secure portals that require recipients to authenticate before viewing documents. Tools like Microsoft 365 Message Encryption and password-protected PDFs or encrypted ZIP files protect data both in transit and at rest.
Have your IT team configure these tools and set up Data Loss Prevention (DLP) rules that detect sensitive keywords like “confidential,” “wire instructions,” or “account number” and automatically trigger encryption. Always test encryption on both desktop and mobile devices to ensure a seamless recipient experience.
4. Double-check all recipients before sending
Remember to check email addresses against approved contact lists and disable auto-complete features. Use “pause before sending” checks for messages that include sensitive data. Even experienced professionals can make mistakes when manually entering account information. Using a secure identity verification platform for a second check adds important safety.
5. Provide continuous security awareness training
Quarterly phishing simulations help identify vulnerabilities. Train staff to recognize BEC patterns, urgent information requests, and last-minute changes to payment instructions.
CertifID data shows 45% of fraudulent emails appear to come from title or settlement agents, 41% from loan officers, and 34% from attorneys. Use real-world examples and update training to address emerging threats, including AI-generated impersonations.
6. Update and patch all email systems regularly
Work with your IT team or service provider to establish automatic patching schedules for email servers, clients, and integrated systems. Subscribe to vendor security alerts and prioritize critical updates. Plan updates during low-activity periods and have fallback plans ready. Outdated software creates weaknesses that attackers exploit, so regular patching is necessary.
7. Use DMARC, DKIM, and SPF email authentication
Coordinate with your IT team or service provider to implement DMARC, DKIM, and SPF authentication. DMARC prevents spoofing of your domain, DKIM signs emails for verification, and SPF designates authorized mail servers.
Have your provider monitor authentication reports to spot any spoofing attempts early. These safety measures protect outgoing communications and verify incoming messages, strengthening overall email trust.
8. Limit email use for high-risk data transmission
Identify transactions and data types that require extra protection. Wire instructions, Social Security numbers, and bank account details should be shared through secure portals, not standard email.
In fact, CertifID data shows 65% of customers had at least one high-risk transaction flagged as suspected fraud, highlighting the importance of secure communication.

9. Monitor, log, and audit email communications
Use email monitoring and security tools to track outgoing sensitive data and flag unusual activity, like emails sent outside of normal business hours or to unfamiliar domains.
These tools can detect suspicious verification requests or patterns commonly seen in fraud hotspots, even when attackers try to hide their location with VPNs. Keep detailed email logs to ensure compliance and help detect threats early.
10. Develop and practice incident response plans
Create detailed procedures for dealing with email security breaches. Assign specific roles to the IT, legal, compliance, and executive teams. Document what needs to be communicated and maintain connections with cybersecurity forensics firms.
CertifID’s Fraud Recovery Services, in partnership with the U.S. Secret Service, helps recover lost funds and track fraud patterns, but it’s better to prevent issues before they happen. Practice response scenarios each year through tabletop exercises.
Even with strong email security, there’s a limit to how safe email can be, especially when money is involved.
Why email wasn't built for money transfers
Email was never designed for secure financial transactions. It was meant for convenience and communication. Traditional email security cannot confirm the identity of the recipient, check their device's safety, or detect new threats in transactions.
Title companies and law firms need purpose-built solutions designed for secure financial exchanges, rather than relying on risky email workarounds. That’s where solutions like CertifID come in, designed specifically for the challenges of secure financial communication.
CertifID: Purpose-built fraud prevention for title operations
Unlike standard email systems, CertifID was purpose-built for real estate transactions. It verifies identities, secures wire instructions, and ensures funds are safely sent and received throughout the process.
CertifID Match verifies identities of parties in the transaction
CertifID Match verifies the identity of each party using nearly 150 risk markers such as device location, IP address, VPN usage, and behavior patterns. This process helps prevent fraud before it reaches your team and ensures you are communicating with the right person every time.

Payoff Protect and Payoff ordering: Almost instant verification of payoff instructions
Payoff Ordering and Payoff Protect streamline the whole mortgage payoff process — from automated ordering with 100% delivery rate for residential payoffs to instant verification that flags invalid account details.
Together, they verify lender instructions across millions of transactions with a 97% success rate, recognizing account number patterns for over 10,000 lenders and identifying fraudulent details before they cause problems.

Send, Request and Collect of wiring instructions
Send, Request, and Collect allows you to securely share and receive wiring instructions. Each transaction is protected with up to $5 million in coverage, ensuring funds are safely directed every time.
In 2024 alone, CertifID protected hundreds of thousands of transactions and prevented over a billion in potential fraud losses. Recipients access secure links through email or text, keeping closings simple and safe.

With the right technology in place, you can move beyond risky email exchanges and protect every transaction from fraud.
Send sensitive information with confidence
Standard email protections help, but they’re not enough when money is on the line. CertifID’s platform closes the gaps fraudsters exploit and streamlines your transaction process. Request a demo to see how secure, efficient communication can protect every dollar you move.

FAQ
Content Marketer
Michelle has spent her career in B2B SaaS startups leading content marketing, strategy, and social media efforts that help teams grow and audiences stay informed. At CertifID, she applies that expertise to help title and real estate professionals understand fraud risks and stay ahead of emerging threats.
Clicking send on wire instructions can be nerve-wracking, especially when you immediately wonder if they reached the right person. That moment shows a real risk.
Email is important for business, but it is also the top gateway for breaches and fraud. The FBI reports $16 billion in cybercrime losses in 2024, a 33% increase from the previous year. In this guide, you will learn how to identify sensitive information, understand email risks, and take practical steps to protect your messages and your business.
Types of sensitive information businesses send by email
You can’t protect what you don’t recognize as sensitive. Knowing the types of information that need extra care is the first step in keeping your business and clients safe.
Now that you know what sensitive information is, it’s important to understand the risks of sending it by email. Recognizing these threats is key to protecting your data and preventing costly mistakes.
8 risks of sending sensitive information by email
Email is one of the most common tools in business, but also one of the riskiest ways to share sensitive information.
Even with filters and firewalls, everyday messages can expose you to costly fraud and data loss. Sending sensitive information via email carries risks. Knowing the main risks helps you protect sensitive information before it’s too late.
1. Phishing attacks
Fraudsters impersonate trusted contacts—like executives, vendors, clients, or partners—to trick employees into giving up sensitive information or passwords. Their messages look convincing and use urgency to push people to act fast. CertifID data shows one in four consumers reported receiving suspicious communications during their real estate transactions, with 58% appearing to come from real estate agents.
2. Business email compromise (BEC)
BEC is the most damaging email threat in business today. The FBI reports 21,442 complaints accounting for nearly $2.8 billion in losses.
Fraudsters infiltrate real conversations for weeks before they attack. According to ALTA, in 2022, 17% of title companies sent money to the wrong account because of fraud, and half of them faced fraud more than once. Fraudsters impersonate executives, attorneys, or partners to redirect payments or access confidential data. Watch this video to see how these scams work and what steps you can take to prevent them.
3. Data interception
Unencrypted emails travel through multiple servers before they reach the recipient. This allows fraudsters to intercept them. When someone is monitoring network traffic, especially on public Wi-Fi or unsecured networks, they can capture wire instructions, account numbers, and client data in plain text. These “man-in-the-middle” attacks are invisible to both sender and recipient and often enable future, more sophisticated breaches.
4. Malware and ransomware
Real estate transactions depend on secure digital systems, but one wrong click can put everything at risk. Malicious attachments or links in emails, text messages, or online portals can install software that gives fraudsters access to your systems. Ransomware, a type of malware, a software that steals credentials, monitors activity, or allows remote access. Ransomware locks files until a ransom is paid. In just hours, an infection can spread through networks, halting closings and costing companies hundreds of thousands.
5. Misaddressed emails
Human error is always a risk. Sellers might not remember their account numbers, which leads them to look and write things down at the same time. This practice causes mistakes.
Auto-complete, similar contact names, or a momentary lapse in attention can result in sending confidential data to unintended recipients.
6. Email spoofing and domain impersonation
Fraudsters forge sender addresses to make messages look like they come from trusted sources. For example, an email might appear to be from “Sarah Johnson, Wells Fargo” but it’s actually from sarah.johnson@wel1sfargo-payoffs.com.
Fraudsters register look-alike domains (wellsfargo.com → wel1sfargo.com) and use them across multiple states to make their messages seem more credible. CertifID’s network analysis has uncovered clusters of aliases and domains operating simultaneously across states and, in many cases, linked through shared registrations, similar hosting, or sending patterns — a strong signal of coordinated fraud campaigns.
7. Weak passwords and compromised credentials
Using easy-to-guess or reused passwords make entire inboxes vulnerable. Fraudsters use credential stuffing, taking passwords from one breach and using them to try to access other accounts. Once inside, they can monitor conversations and impersonate the account holder, usually going undetected for weeks.
8. Third-party data retention and storage risks
Email providers store sent messages indefinitely on their servers, increasing the risk if those servers are ever compromised. Cloud-based email adds more possible targets for attacks, extending risk beyond the original message.
While these risks are significant, there are effective ways to reduce them — beginning with stronger authentication, employee training, and using secure communication platforms designed to keep your data safe.

How to send sensitive information via email: 10 best practices
Protecting sensitive information via email requires multiple layers working together. No single solution is enough on its own.
1. Establish clear email security policies
Experiencing just one high-risk transaction can increase a company’s exposure sixfold compared with peer companies, according to CertifID’s State of Wire Fraud data.
Clear, consistent policies help prevent fraud from escalating. They should cover what not to send by email, approved methods to share different types of sensitive data, and set rules for handling financial records, client files, and other confidential documents.
Policies should also cover regulatory requirements like GLBA for financial information, HIPAA for health records, or industry-specific standards. Make sure policies are easy to access and require all employees to review and acknowledge them annually.
2. Require strong passwords and enable multi-factor authentication (MFA)
Passwords should be at least 12 characters and combine uppercase, lowercase, numbers, and symbols.

Password managers like LastPass, 1Password, or Dashlane help employees create and store strong, unique passwords for every account, so they don’t have to reuse them or remember dozens of complex passwords. Adding multi-factor authentication (MFA) provides an extra layer of security, which is critical for anyone managing financial transactions.
3. Encrypt emails and attachments
End-to-end encryption ensures that only intended recipients can access sensitive information. Use secure portals that require recipients to authenticate before viewing documents. Tools like Microsoft 365 Message Encryption and password-protected PDFs or encrypted ZIP files protect data both in transit and at rest.
Have your IT team configure these tools and set up Data Loss Prevention (DLP) rules that detect sensitive keywords like “confidential,” “wire instructions,” or “account number” and automatically trigger encryption. Always test encryption on both desktop and mobile devices to ensure a seamless recipient experience.
4. Double-check all recipients before sending
Remember to check email addresses against approved contact lists and disable auto-complete features. Use “pause before sending” checks for messages that include sensitive data. Even experienced professionals can make mistakes when manually entering account information. Using a secure identity verification platform for a second check adds important safety.
5. Provide continuous security awareness training
Quarterly phishing simulations help identify vulnerabilities. Train staff to recognize BEC patterns, urgent information requests, and last-minute changes to payment instructions.
CertifID data shows 45% of fraudulent emails appear to come from title or settlement agents, 41% from loan officers, and 34% from attorneys. Use real-world examples and update training to address emerging threats, including AI-generated impersonations.
6. Update and patch all email systems regularly
Work with your IT team or service provider to establish automatic patching schedules for email servers, clients, and integrated systems. Subscribe to vendor security alerts and prioritize critical updates. Plan updates during low-activity periods and have fallback plans ready. Outdated software creates weaknesses that attackers exploit, so regular patching is necessary.
7. Use DMARC, DKIM, and SPF email authentication
Coordinate with your IT team or service provider to implement DMARC, DKIM, and SPF authentication. DMARC prevents spoofing of your domain, DKIM signs emails for verification, and SPF designates authorized mail servers.
Have your provider monitor authentication reports to spot any spoofing attempts early. These safety measures protect outgoing communications and verify incoming messages, strengthening overall email trust.
8. Limit email use for high-risk data transmission
Identify transactions and data types that require extra protection. Wire instructions, Social Security numbers, and bank account details should be shared through secure portals, not standard email.
In fact, CertifID data shows 65% of customers had at least one high-risk transaction flagged as suspected fraud, highlighting the importance of secure communication.

9. Monitor, log, and audit email communications
Use email monitoring and security tools to track outgoing sensitive data and flag unusual activity, like emails sent outside of normal business hours or to unfamiliar domains.
These tools can detect suspicious verification requests or patterns commonly seen in fraud hotspots, even when attackers try to hide their location with VPNs. Keep detailed email logs to ensure compliance and help detect threats early.
10. Develop and practice incident response plans
Create detailed procedures for dealing with email security breaches. Assign specific roles to the IT, legal, compliance, and executive teams. Document what needs to be communicated and maintain connections with cybersecurity forensics firms.
CertifID’s Fraud Recovery Services, in partnership with the U.S. Secret Service, helps recover lost funds and track fraud patterns, but it’s better to prevent issues before they happen. Practice response scenarios each year through tabletop exercises.
Even with strong email security, there’s a limit to how safe email can be, especially when money is involved.
Why email wasn't built for money transfers
Email was never designed for secure financial transactions. It was meant for convenience and communication. Traditional email security cannot confirm the identity of the recipient, check their device's safety, or detect new threats in transactions.
Title companies and law firms need purpose-built solutions designed for secure financial exchanges, rather than relying on risky email workarounds. That’s where solutions like CertifID come in, designed specifically for the challenges of secure financial communication.
CertifID: Purpose-built fraud prevention for title operations
Unlike standard email systems, CertifID was purpose-built for real estate transactions. It verifies identities, secures wire instructions, and ensures funds are safely sent and received throughout the process.
CertifID Match verifies identities of parties in the transaction
CertifID Match verifies the identity of each party using nearly 150 risk markers such as device location, IP address, VPN usage, and behavior patterns. This process helps prevent fraud before it reaches your team and ensures you are communicating with the right person every time.

Payoff Protect and Payoff ordering: Almost instant verification of payoff instructions
Payoff Ordering and Payoff Protect streamline the whole mortgage payoff process — from automated ordering with 100% delivery rate for residential payoffs to instant verification that flags invalid account details.
Together, they verify lender instructions across millions of transactions with a 97% success rate, recognizing account number patterns for over 10,000 lenders and identifying fraudulent details before they cause problems.

Send, Request and Collect of wiring instructions
Send, Request, and Collect allows you to securely share and receive wiring instructions. Each transaction is protected with up to $5 million in coverage, ensuring funds are safely directed every time.
In 2024 alone, CertifID protected hundreds of thousands of transactions and prevented over a billion in potential fraud losses. Recipients access secure links through email or text, keeping closings simple and safe.

With the right technology in place, you can move beyond risky email exchanges and protect every transaction from fraud.
Send sensitive information with confidence
Standard email protections help, but they’re not enough when money is on the line. CertifID’s platform closes the gaps fraudsters exploit and streamlines your transaction process. Request a demo to see how secure, efficient communication can protect every dollar you move.

Content Marketer
Michelle has spent her career in B2B SaaS startups leading content marketing, strategy, and social media efforts that help teams grow and audiences stay informed. At CertifID, she applies that expertise to help title and real estate professionals understand fraud risks and stay ahead of emerging threats.
Sign up for The Wire to join the conversation.





.png)



