Real estate scams: Common fraud schemes targeting title companies
Wire fraud is growing more sophisticated. Learn how modern verification keeps title companies and their clients safe.

Tyler Adams
8 minutes
Real Estate
Jul 19, 2021
Dec 5, 2025
Title professionals face a frustrating paradox: the very manual steps meant to stop fraud often make it easier for it to happen. On average, teams spend 15 to 20 minutes manually verifying each wire instruction through phone callbacks.
That time adds up fast, especially during busy closing periods. With the pressure to keep deals moving, overworked staff can end up rushing through security checks, creating openings for fraudsters to slip through.
The impact is clear. More than $500 million is lost to real estate wire fraud each year, and 17% of title companies have sent funds to the wrong account because of it. To understand how to prevent these losses, it helps to first look at what today’s real estate scams actually are and how they’ve changed over time.
What is a real estate scam
Real estate scams are fraudulent schemes that target property transactions, and wire fraud is the most costly threat in the industry. These scams have changed over time. What once started as simple email phishing now includes sophisticated AI-powered attacks that can target every stage of a transaction, from the first offer to the final wire transfer.
The real estate fraud ecosystem is complex. Fraudsters take advantage of the many parties involved in a deal—buyers, sellers, agents, lenders, and title companies.
They exploit the large sums of money that change hands in these transactions. These attacks are not random. Modern fraudsters focus on weaknesses in the industry to maximize their chances of success.
Real estate attracts cybercrime because property records are easy to access. Publicly available property records make it easy for fraudsters to gather information. Many firms have traditionally low IT infrastructure and lack strong cybersecurity measures.
With median home prices reaching $422,400, every transaction is a potential target for fraud. It is important to understand the types of scams and how they work to protect clients and their money.
The time trap: why manual verification creates more risk
Title professionals often get stuck in a dangerous cycle. The more transactions they handle manually, the higher their risk of fraud becomes. Take wire verification, for example. Each payoff call can take 15 to 20 minutes, and chasing down buyers, waiting for confirmations, and double-checking instructions can take even longer. Staff describe it as a constant “chase-and-wait” cycle, where one call leads to another, and every minute adds pressure to keep deals moving.
This fast pace takes a toll. Burnout sets in, and overworked teams start taking shortcuts. Red flags can get missed during busy periods, creating gaps that fraudsters are quick to exploit.
One industry professional summed it up: “You spend so much time verifying each wire that by the end of the day, you’re just hoping nothing slips through. There’s no confidence, only urgency.”
The numbers confirm the risk. Companies that experience a single fraud incident see their high-risk transaction rate rise to 6x higher than their peers. Fraudsters are not attacking randomly; they systematically target companies with known vulnerabilities. The more time title professionals spend on manual tasks, the more vulnerable they become. This makes it important to balance efficiency and security in every transaction.
Most common real estate scams targeting title professionals in 2025
Fraudsters are targeting every part of the real estate process, from emails to wire transfers. Here’s a look at the scams title professionals are facing today and how they work.
Email phishing
Email phishing is one of the oldest and most common types of cybercrime, but it continues to evolve. It helps to see how these attacks unfold in practice. The diagram below shows a typical wire fraud scenario and how just one phishing email can start a chain of events that ends with money landing in a fraudster’s account.
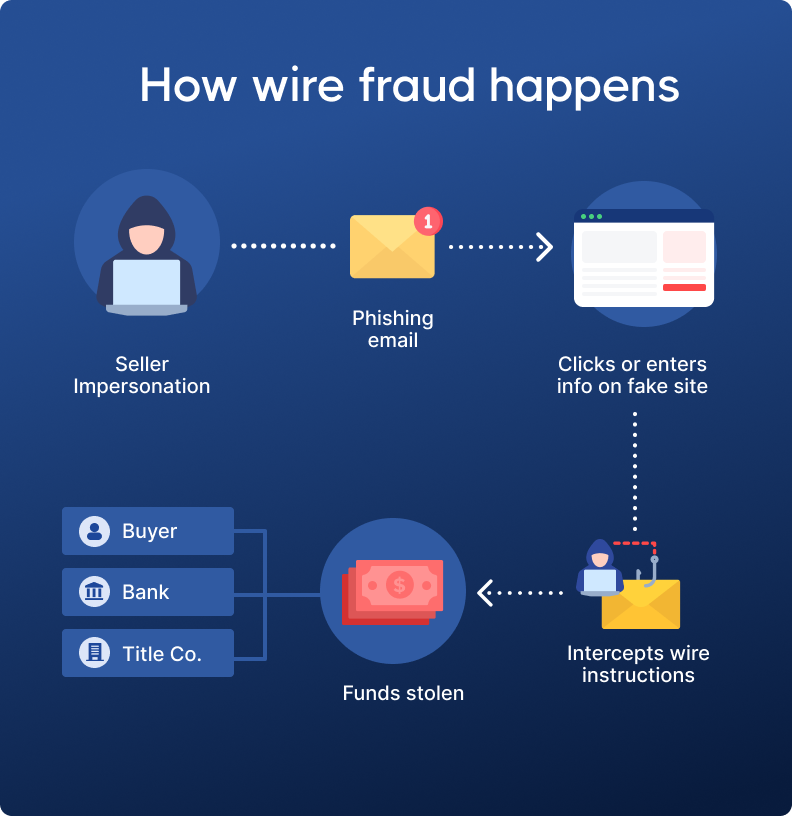
Fraudsters send emails that look like they come from trusted companies and claim there’s a problem with your account. The emails include a link that seems real but goes to a fake login page built to steal your credentials.
Everything looks familiar, from the logo to the layout, but a small detail like a misspelled URL gives it away. If you enter your information, it goes straight to the fraudsters. Some fake sites even redirect you to the real one afterward, so you might not realize you’ve been tricked.
Spear phishing
Spear phishing is more targeted. Fraudsters send emails from a cloned account, copying the name, job title, signature, and email of a trusted source. In real estate, they often pose as a buyer, seller, title agent, or realtor.
The goal is to steal confidential information or redirect funds. Victims may be sent “updated” wire instructions or links to fake websites and log-in portals. Some fraudsters even pressure recipients to make upfront payments.
These emails are hard to spot and can bypass spam filters because they are sent to specific people rather than large groups. They may come from email addresses that have never been used for phishing before.

Warning signs include unexpected requests to change wire instructions, immediate action demands, or emails from unrecognized addresses. Slowing down and confirming authenticity can prevent costly mistakes.
Whaling and business email compromise (BEC)
Whaling and BEC scams target higher-level employees or company executives. Fraudsters impersonate someone in authority and send urgent messages requesting large wire transfers or sensitive information. A common example is an email that looks like it comes from a company owner or CEO, requesting that a controller pay an invoice quickly.
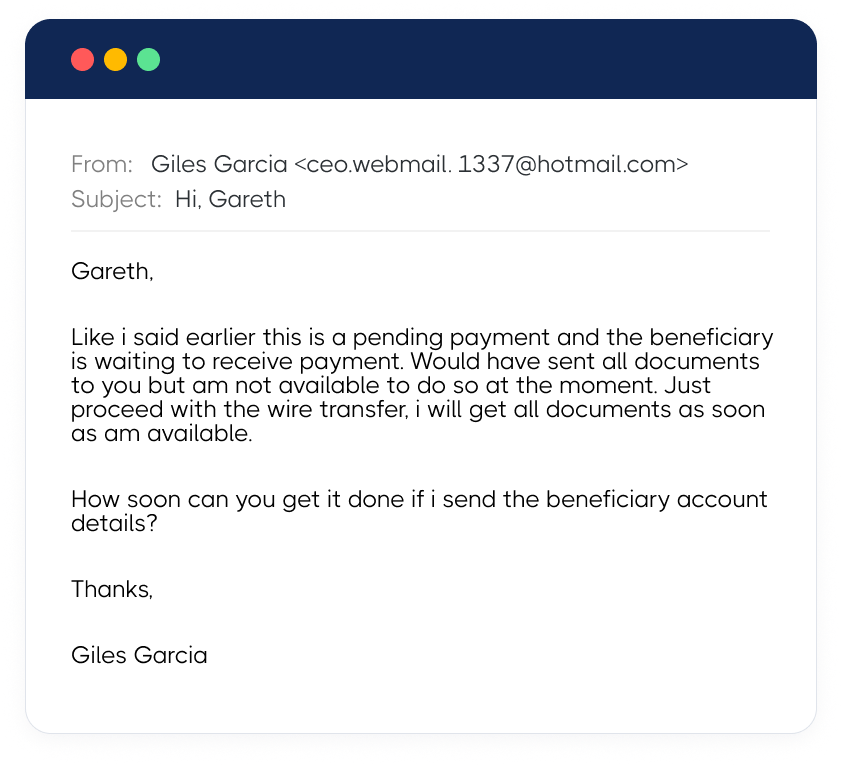
Be cautious of any unexpected email that asks for urgent action from a superior. It could be a whaling attempt.
In real estate, attackers hack into a title company owner’s account to trick employees into wiring funds. These emails are convincing and personal, often bypassing spam filters entirely.
Vishing
Vishing, or voice phishing, happens over the phone. Fraudsters call or leave voicemails pretending to be from a trusted organization, such as a title company, bank, or attorney’s office.
They often use real details from transactions to sound convincing and claim they are trying to prevent fraud. They aim to trick victims into following fake wire instructions or sharing sensitive information.
Social engineering
Social engineering ties everything together. It’s the manipulation behind every scam. Fraudsters combine stolen data, cloned emails, and spoofed calls to create pressure and urgency.
They make their messages sound routine and their requests sound reasonable. Slowing down, verifying details independently, and using secure communication tools are the best ways to stop these tactics from working. Beyond phishing and spoofed emails, identity-based scams are now becoming some of the hardest to detect.
Seller impersonation and identity fraud
Seller impersonation has become one of the toughest scams in the real estate market to catch. Fraudsters target vacant properties and out-of-state transactions where it’s harder to confirm a seller’s identity through traditional methods. Using stolen personal information and AI-generated documents, they build convincing fake personas that look legitimate at every step.
These scams aren’t small losses either. According to the State of Wire Fraud report, the average seller incurs fraud costs of about $172,000. Advanced tools like device analysis can help identify suspicious activities and stop the scams that manual verification would completely miss.
Warning signs that manual processes miss (but technology catches)
Manual verifications have limits, especially as fraudsters become more skilled. Callbacks, for example, can only go so far. A title professional might know the lender’s name and standard payoff instructions, but that alone won’t reveal subtle changes a fraudster has introduced.
Watch just how caller ID spoofing complicates things even more:
A fraudster can appear to be a trusted lender or agent during the call, and even if the real lender is on the line, they might confirm payoff information that has been manipulated elsewhere in the transaction.
High-pressure situations make it even harder to trust human verification. When teams are juggling multiple closings at once, it’s easy to overlook small inconsistencies. Fraudsters count on this.
They create urgency, claiming a wire must go through immediately or a deal will fall apart. They follow up multiple times, leaving several voicemails or sending emails that seem routine but carry hidden instructions. Even well-trained staff can feel rushed, second-guess themselves, or skip verification steps entirely.
Modern fraud detection technology addresses these gaps. It can flag anomalies across multiple data points that humans can’t track in real time, like inconsistencies in device fingerprints, unusual IP addresses, or deviations from historical wire patterns.
These tools identify risks before funds are moved, which reduces the need for stressful and error-prone manual processes. By combining technology with human judgment, title professionals can spot threats earlier and better protect clients and transactions. Knowing what these warning signs look like is only half the battle. The next step is building the right defenses so your team can catch fraud before it starts.
How to protect your company from real estate scams: moving beyond manual verification
Protecting your business, clients, and reputation from real estate scams requires more than reactive measures. Successful title companies stay ahead of fraud by combining education, secure processes, and strong cybersecurity practices. These are the key steps you can take to reduce risk and keep transactions safe.
Educate clients early and often
One of the best ways to prevent fraud is to bring clients into the conversation. Provide resources and guidance on spotting phishing emails and suspicious transactions.
Teach clients how to verify communications, documents, and transaction instructions. Encourage them to ask questions and flag anything that seems unusual. Sharing real-life examples of scams, warning signs, and practical tips helps clients stay alert and reduces the chance of costly mistakes.
Offer secure payment instruction options
Sensitive financial information should never travel through insecure channels like email or text. Tools like CertifID provide end-to-end encryption for safely sharing account information.
They also allow independent verification of all parties’ identities and bank routing details before any transfer takes place. In the rare event that fraud does occur, users have access to fraud recovery services, helping mitigate losses and protect their reputation.
Practice strong cybersecurity hygiene
Even the most cautious teams can fall victim to fraud if basic security practices are not followed. Enforce strong password policies and require two-factor authentication on all key systems.
Train employees to spot suspicious activity, including phishing emails or unexpected requests for sensitive information. Always verify the identity of every party involved before sharing financial information or authorizing transactions. Consistently following these habits reduces risk and better prepares your organization for new tactics fraudsters may try.
Watch these strategies in action and learn more ways to stay ahead of new fraud schemes:
Integration benefits for title production software
Modern fraud prevention tools integrate with title production software like SoftPro, ResWare, RamQuest, and Settlor, eliminating double data entry and making workflows more efficient.
With CertifID, title professionals can verify payoff instructions in real time, including ordering payoffs instantly without risky or time-consuming callbacks.
Users get up to $5M direct insurance coverage per file and maintain full audit trails to meet regulatory compliance. By creating clear documentation that manual processes can’t, integrated technology speeds up transactions and gives title professionals protection and peace of mind.
What to do if you suspect fraud: recovery steps for title professionals
The moment you suspect fraud, time becomes your most valuable asset. The first step is to stop all wire transfers immediately to prevent any funds from leaving your accounts until everything is verified.
Next, document everything, including emails, phone calls, transaction notes, and any unusual communication. Then, reach out to your insurance providers and fraud recovery specialists. Acting quickly can make all the difference.
Recovery statistics show just how important speed is. According to the 2025 State of Wire Fraud, when fraud is detected early, 73% of consumers are able to recover their funds. But if they wait too long, 27% lose most or all of their funds. For title professionals, this underlines the need to have fraud recovery contacts ready before an incident occurs.
It’s important to contact your E&O carrier and title insurance providers right away. These partners offer guidance, coordinate recovery efforts, and help protect you from liability. They also make sure you have the necessary documentation for regulatory compliance and claims processing.
Fraud incidents test more than finances. Reputation and client trust are on the line. How you respond is often more important than the event itself. Being open, acting fast, and having professional recovery support increase the chances of recovering funds and reassure clients that their transaction was handled carefully. With the right protocols and partnerships in place, title professionals can manage incidents confidently and protect their business and clients.
Real estate scams: breaking free from the manual verification trap
Manual verification may seem safe, but it actually increases the risk of fraud and puts a strain on operations. Spending hours on phone callbacks and payoff confirmations creates opportunities for errors, burnout, and security gaps.
Modernizing your verification process is no longer optional. It protects your business, clients, and reputation. The real question isn’t whether your title company can afford to adopt these tools, but whether you can afford the ongoing risks and potential losses from sticking with an outdated manual process.

FAQ
How can title companies verify payoff instructions without phone callbacks?
Title professionals can use automated verification tools to confirm payoff amounts and routing information in real time. These tools reduce the need for time-consuming phone calls while maintaining security and accuracy.
What should I do if a payoff amount changes last minute?
Always follow verification protocols immediately. Modern systems can flag any changes in amounts and require confirmation before funds are transferred, helping prevent costly mistakes.
How can small title companies afford fraud prevention technology?
Fraud prevention is an investment that typically costs far less than the losses from wire scams. Scalable solutions with flexible pricing make advanced protection accessible for companies of all sizes, ensuring smaller teams can operate securely without overextending budgets.
What is the liability exposure for title companies that experience a scam?
E&O insurance can help reduce financial risk, but reputational damage and lost client trust can have long-term effects. Using clear verification processes and modern fraud prevention tools creates audit trails and evidence that protect the business and its clients.
What are typical real estate scams beyond wire fraud?
Real estate fraud takes many forms beyond wire transfers.
- Foreclosure relief scams prey on struggling homeowners by charging upfront fees for services that never materialize, often leaving victims in worse financial situations
- Loan-flipping scams convince homeowners—particularly seniors with significant equity—to refinance repeatedly, draining their equity through excessive fees and unfavorable terms
- Fake buyer scams use unsolicited texts or emails to collect personal information or trick sellers into wiring funds to fraudulent accounts. Home inspection scams involve criminals posing as licensed inspectors who rush through inspections or intentionally hide serious property issues, leaving buyers with costly surprises after closing.
- Rental scams advertise fake properties or use bait-and-switch tactics to collect deposits and personal information from prospective tenants
- Title and deed scams are particularly dangerous, as criminals use stolen personal information to forge documents and illegally transfer property ownership. Once they control the title, they can take out loans against the property or attempt to sell it without the owner's knowledge.
As a title professional, you play a critical role in protecting clients from these threats. Educating clients about the full spectrum of real estate fraud helps build trust and positions your company as a security-focused partner.
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Title professionals face a frustrating paradox: the very manual steps meant to stop fraud often make it easier for it to happen. On average, teams spend 15 to 20 minutes manually verifying each wire instruction through phone callbacks.
That time adds up fast, especially during busy closing periods. With the pressure to keep deals moving, overworked staff can end up rushing through security checks, creating openings for fraudsters to slip through.
The impact is clear. More than $500 million is lost to real estate wire fraud each year, and 17% of title companies have sent funds to the wrong account because of it. To understand how to prevent these losses, it helps to first look at what today’s real estate scams actually are and how they’ve changed over time.
What is a real estate scam
Real estate scams are fraudulent schemes that target property transactions, and wire fraud is the most costly threat in the industry. These scams have changed over time. What once started as simple email phishing now includes sophisticated AI-powered attacks that can target every stage of a transaction, from the first offer to the final wire transfer.
The real estate fraud ecosystem is complex. Fraudsters take advantage of the many parties involved in a deal—buyers, sellers, agents, lenders, and title companies.
They exploit the large sums of money that change hands in these transactions. These attacks are not random. Modern fraudsters focus on weaknesses in the industry to maximize their chances of success.
Real estate attracts cybercrime because property records are easy to access. Publicly available property records make it easy for fraudsters to gather information. Many firms have traditionally low IT infrastructure and lack strong cybersecurity measures.
With median home prices reaching $422,400, every transaction is a potential target for fraud. It is important to understand the types of scams and how they work to protect clients and their money.
The time trap: why manual verification creates more risk
Title professionals often get stuck in a dangerous cycle. The more transactions they handle manually, the higher their risk of fraud becomes. Take wire verification, for example. Each payoff call can take 15 to 20 minutes, and chasing down buyers, waiting for confirmations, and double-checking instructions can take even longer. Staff describe it as a constant “chase-and-wait” cycle, where one call leads to another, and every minute adds pressure to keep deals moving.
This fast pace takes a toll. Burnout sets in, and overworked teams start taking shortcuts. Red flags can get missed during busy periods, creating gaps that fraudsters are quick to exploit.
One industry professional summed it up: “You spend so much time verifying each wire that by the end of the day, you’re just hoping nothing slips through. There’s no confidence, only urgency.”
The numbers confirm the risk. Companies that experience a single fraud incident see their high-risk transaction rate rise to 6x higher than their peers. Fraudsters are not attacking randomly; they systematically target companies with known vulnerabilities. The more time title professionals spend on manual tasks, the more vulnerable they become. This makes it important to balance efficiency and security in every transaction.
Most common real estate scams targeting title professionals in 2025
Fraudsters are targeting every part of the real estate process, from emails to wire transfers. Here’s a look at the scams title professionals are facing today and how they work.
Email phishing
Email phishing is one of the oldest and most common types of cybercrime, but it continues to evolve. It helps to see how these attacks unfold in practice. The diagram below shows a typical wire fraud scenario and how just one phishing email can start a chain of events that ends with money landing in a fraudster’s account.

Fraudsters send emails that look like they come from trusted companies and claim there’s a problem with your account. The emails include a link that seems real but goes to a fake login page built to steal your credentials.
Everything looks familiar, from the logo to the layout, but a small detail like a misspelled URL gives it away. If you enter your information, it goes straight to the fraudsters. Some fake sites even redirect you to the real one afterward, so you might not realize you’ve been tricked.
Spear phishing
Spear phishing is more targeted. Fraudsters send emails from a cloned account, copying the name, job title, signature, and email of a trusted source. In real estate, they often pose as a buyer, seller, title agent, or realtor.
The goal is to steal confidential information or redirect funds. Victims may be sent “updated” wire instructions or links to fake websites and log-in portals. Some fraudsters even pressure recipients to make upfront payments.
These emails are hard to spot and can bypass spam filters because they are sent to specific people rather than large groups. They may come from email addresses that have never been used for phishing before.

Warning signs include unexpected requests to change wire instructions, immediate action demands, or emails from unrecognized addresses. Slowing down and confirming authenticity can prevent costly mistakes.
Whaling and business email compromise (BEC)
Whaling and BEC scams target higher-level employees or company executives. Fraudsters impersonate someone in authority and send urgent messages requesting large wire transfers or sensitive information. A common example is an email that looks like it comes from a company owner or CEO, requesting that a controller pay an invoice quickly.

Be cautious of any unexpected email that asks for urgent action from a superior. It could be a whaling attempt.
In real estate, attackers hack into a title company owner’s account to trick employees into wiring funds. These emails are convincing and personal, often bypassing spam filters entirely.
Vishing
Vishing, or voice phishing, happens over the phone. Fraudsters call or leave voicemails pretending to be from a trusted organization, such as a title company, bank, or attorney’s office.
They often use real details from transactions to sound convincing and claim they are trying to prevent fraud. They aim to trick victims into following fake wire instructions or sharing sensitive information.
Social engineering
Social engineering ties everything together. It’s the manipulation behind every scam. Fraudsters combine stolen data, cloned emails, and spoofed calls to create pressure and urgency.
They make their messages sound routine and their requests sound reasonable. Slowing down, verifying details independently, and using secure communication tools are the best ways to stop these tactics from working. Beyond phishing and spoofed emails, identity-based scams are now becoming some of the hardest to detect.
Seller impersonation and identity fraud
Seller impersonation has become one of the toughest scams in the real estate market to catch. Fraudsters target vacant properties and out-of-state transactions where it’s harder to confirm a seller’s identity through traditional methods. Using stolen personal information and AI-generated documents, they build convincing fake personas that look legitimate at every step.
These scams aren’t small losses either. According to the State of Wire Fraud report, the average seller incurs fraud costs of about $172,000. Advanced tools like device analysis can help identify suspicious activities and stop the scams that manual verification would completely miss.
Warning signs that manual processes miss (but technology catches)
Manual verifications have limits, especially as fraudsters become more skilled. Callbacks, for example, can only go so far. A title professional might know the lender’s name and standard payoff instructions, but that alone won’t reveal subtle changes a fraudster has introduced.
Watch just how caller ID spoofing complicates things even more:
A fraudster can appear to be a trusted lender or agent during the call, and even if the real lender is on the line, they might confirm payoff information that has been manipulated elsewhere in the transaction.
High-pressure situations make it even harder to trust human verification. When teams are juggling multiple closings at once, it’s easy to overlook small inconsistencies. Fraudsters count on this.
They create urgency, claiming a wire must go through immediately or a deal will fall apart. They follow up multiple times, leaving several voicemails or sending emails that seem routine but carry hidden instructions. Even well-trained staff can feel rushed, second-guess themselves, or skip verification steps entirely.
Modern fraud detection technology addresses these gaps. It can flag anomalies across multiple data points that humans can’t track in real time, like inconsistencies in device fingerprints, unusual IP addresses, or deviations from historical wire patterns.
These tools identify risks before funds are moved, which reduces the need for stressful and error-prone manual processes. By combining technology with human judgment, title professionals can spot threats earlier and better protect clients and transactions. Knowing what these warning signs look like is only half the battle. The next step is building the right defenses so your team can catch fraud before it starts.
How to protect your company from real estate scams: moving beyond manual verification
Protecting your business, clients, and reputation from real estate scams requires more than reactive measures. Successful title companies stay ahead of fraud by combining education, secure processes, and strong cybersecurity practices. These are the key steps you can take to reduce risk and keep transactions safe.
Educate clients early and often
One of the best ways to prevent fraud is to bring clients into the conversation. Provide resources and guidance on spotting phishing emails and suspicious transactions.
Teach clients how to verify communications, documents, and transaction instructions. Encourage them to ask questions and flag anything that seems unusual. Sharing real-life examples of scams, warning signs, and practical tips helps clients stay alert and reduces the chance of costly mistakes.
Offer secure payment instruction options
Sensitive financial information should never travel through insecure channels like email or text. Tools like CertifID provide end-to-end encryption for safely sharing account information.
They also allow independent verification of all parties’ identities and bank routing details before any transfer takes place. In the rare event that fraud does occur, users have access to fraud recovery services, helping mitigate losses and protect their reputation.
Practice strong cybersecurity hygiene
Even the most cautious teams can fall victim to fraud if basic security practices are not followed. Enforce strong password policies and require two-factor authentication on all key systems.
Train employees to spot suspicious activity, including phishing emails or unexpected requests for sensitive information. Always verify the identity of every party involved before sharing financial information or authorizing transactions. Consistently following these habits reduces risk and better prepares your organization for new tactics fraudsters may try.
Watch these strategies in action and learn more ways to stay ahead of new fraud schemes:
Integration benefits for title production software
Modern fraud prevention tools integrate with title production software like SoftPro, ResWare, RamQuest, and Settlor, eliminating double data entry and making workflows more efficient.
With CertifID, title professionals can verify payoff instructions in real time, including ordering payoffs instantly without risky or time-consuming callbacks.
Users get up to $5M direct insurance coverage per file and maintain full audit trails to meet regulatory compliance. By creating clear documentation that manual processes can’t, integrated technology speeds up transactions and gives title professionals protection and peace of mind.
What to do if you suspect fraud: recovery steps for title professionals
The moment you suspect fraud, time becomes your most valuable asset. The first step is to stop all wire transfers immediately to prevent any funds from leaving your accounts until everything is verified.
Next, document everything, including emails, phone calls, transaction notes, and any unusual communication. Then, reach out to your insurance providers and fraud recovery specialists. Acting quickly can make all the difference.
Recovery statistics show just how important speed is. According to the 2025 State of Wire Fraud, when fraud is detected early, 73% of consumers are able to recover their funds. But if they wait too long, 27% lose most or all of their funds. For title professionals, this underlines the need to have fraud recovery contacts ready before an incident occurs.
It’s important to contact your E&O carrier and title insurance providers right away. These partners offer guidance, coordinate recovery efforts, and help protect you from liability. They also make sure you have the necessary documentation for regulatory compliance and claims processing.
Fraud incidents test more than finances. Reputation and client trust are on the line. How you respond is often more important than the event itself. Being open, acting fast, and having professional recovery support increase the chances of recovering funds and reassure clients that their transaction was handled carefully. With the right protocols and partnerships in place, title professionals can manage incidents confidently and protect their business and clients.
Real estate scams: breaking free from the manual verification trap
Manual verification may seem safe, but it actually increases the risk of fraud and puts a strain on operations. Spending hours on phone callbacks and payoff confirmations creates opportunities for errors, burnout, and security gaps.
Modernizing your verification process is no longer optional. It protects your business, clients, and reputation. The real question isn’t whether your title company can afford to adopt these tools, but whether you can afford the ongoing risks and potential losses from sticking with an outdated manual process.

Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Sign up for The Wire to join the conversation.