Cybersecurity in real estate: Complete protection guide for your business
Real estate professionals face nearly $500 million in annual wire fraud losses—yet most firms spend almost nothing on prevention. Discover how to protect your business, clients, and reputation with proven cybersecurity strategies.

Tyler Adams
6 mins
Cybersecurity
Jul 19, 2021
Dec 5, 2025
According to our State of Wire Fraud report, the real estate industry loses nearly $500 million annually to business email compromise attacks (BEC)—yet most firms invest almost nothing in prevention.
Even more alarming, 29% of title companies spend less than $1,000 per year on cybersecurity, and 20% spend nothing at all, despite handling millions in client funds every month.
This isn't just an IT problem. It's a fiduciary responsibility that impacts your professional liability and client trust.
Whether you're running a title company or managing a law closing practice, understanding cybersecurity in real estate is the difference between protecting your business and becoming the next fraud statistic.
Cybersecurity in real estate: Why the industry is under siege now
Cybersecurity in real estate means protecting sensitive financial data, wire transfer information, and personal client details from cybercriminals who exploit vulnerabilities during property transactions.
Real estate transactions are usually complex, with multiple parties involved, so the industry faces unique threats that other industries rarely encounter.
Property records and listings create a publicly available goldmine for fraudsters. For just a few hundred dollars monthly, criminals can subscribe to APIs that provide detailed:
- Transaction information
- Party names
- Closing dates
- Transaction values
These data points give criminals all the insight they need to strike at the right moment. The numbers tell a troubling story.
Transactions averaging $429K, combined with 32% all-cash buyers and consumers who only purchase homes once every fifteen years, create perfect conditions for fraud. Most buyers and sellers lack the experience to spot scams, making them vulnerable to attacks that seasoned professionals might catch.
The industry's historically low IT infrastructure requirements compound these vulnerabilities. While other sectors invested heavily in cybersecurity over the past decade, real estate operated under inconsistent state-by-state regulations.
5 most common cybersecurity threats in real estate
Beyond BEC, real estate professionals face evolving threats that exploit industry-specific vulnerabilities. Each threat shares a common characteristic: they target transaction points where large sums of money change hands.
1. Ransomware attacks
Ransomware attacks begin when criminals gain access to your systems—usually through phishing emails, outdated software, or stolen passwords.
Once inside, they lock your company data and demand payment to unlock it. Title companies and law firms are prime targets because of tight closing deadlines and valuable client information.
The pressure can be intense. When your systems are locked and a $500,000 closing is scheduled for tomorrow, paying the ransom feels like the only option.
Missing a closing deadline can kill a deal, trigger legal claims, and destroy client relationships. Operations grind to a halt, leading to major losses. Worse yet, sometimes the data stays locked even after paying—criminals hardly keep their word.
You can reduce ransomware risk by keeping software updated, backing up data regularly on separate systems, and using security software that catches threats early.
2. Seller impersonation fraud
Seller impersonation fraud is one of the fastest-growing schemes in real estate. Fraudsters pose as property owners to list and sell properties they don't own, pocketing proceeds before anyone realizes the real owner never authorized the sale.
These schemes particularly target vacant land sales, out-of-state transactions, and LLC-owned properties where verification is traditionally harder.
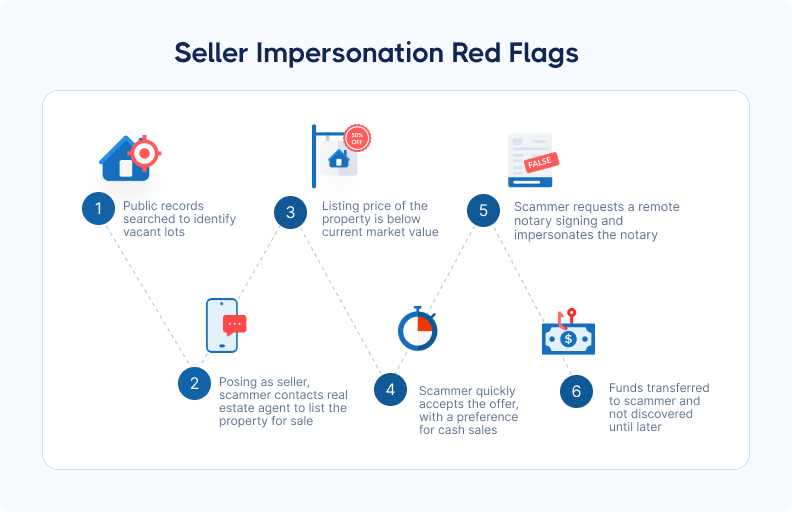
The financial impact can be devastating for all parties involved. Buyers lose their down payments, title companies face liability claims, and rightful property owners must navigate legal battles to reclaim their assets. Starting transactions with advanced identity verification provides the strongest defense against these schemes.

3. Data breaches
Data breaches expose far more than basic contact information. Real estate companies hold substantial volumes of sensitive information—personal details of buyers and sellers, financial records, and full transaction histories. The interconnected nature of real estate databases means a single breach can compromise multiple transactions.
When a title company's systems are compromised, fraudsters gain access to closing dates, party names, transaction amounts, and established communication patterns.
The financial cost includes direct losses, reputational damage, and potential legal consequences.
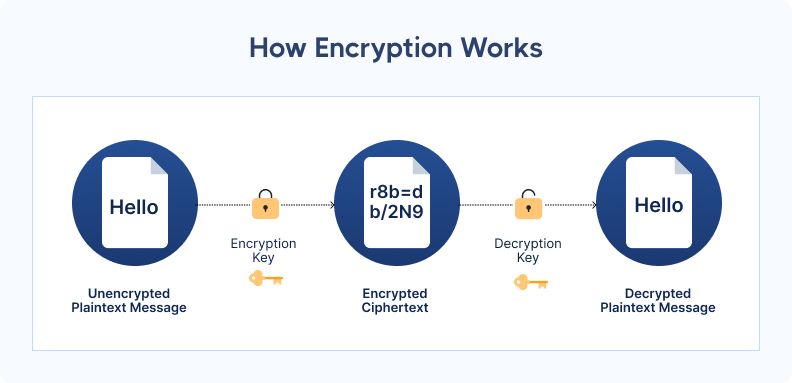
To reduce these risks, proper data encryption and access controls provide critical protection, ensuring that even if unauthorized individuals gain access, they cannot exploit the information.
4. Phishing and social engineering attacks
Phishing and social engineering attacks exploit human trust rather than technical vulnerabilities. Employees receive legitimate-looking emails or messages requesting sensitive information or system access. Attackers study your communication patterns and strike during busy closing periods.
The best defense combines employee training with technical safeguards. Teams need regular education on recognizing phishing attempts, verifying email addresses before clicking links, and reporting suspicious communications. Email filtering solutions and zero-trust policies—requiring verification at every step—provide additional layers of protection against these attacks.
5. AI-powered deepfake attacks
The newest frontier involves AI-powered deepfake attacks that create convincing voice recordings and video calls impersonating trusted parties.
Traditional callback verification methods become less reliable when criminals can clone voices in real time. What sounds like a lender confirming payoff instructions might be a fraudster using voice synthesis technology.
These attacks represent a shift in threat sophistication. Human detection methods are no longer sufficient against current threat levels.
Protection requires technology platforms with access to extensive databases of verified lender information. These eliminate the guesswork and provide instant validation against thousands of known lenders.
Modern systems can verify payoff instructions in under 60 seconds, replacing manual calls and faxes with automated processing that centralises all payoff details in one dashboard.
Best practices for real estate cybersecurity
Protecting your business requires a layered approach that addresses both technology and human factors. No single solution provides complete protection—effective cybersecurity combines multiple defensive strategies.
1. Implement secure communication protocols
Move beyond basic email encryption to establish verified communication channels for all transaction-related correspondence.
Multi-factor authentication should be mandatory for accessing any system containing wire transfer information. Single-factor password protection is insufficient—fraudsters can compromise passwords through phishing or data breaches.
Secure document sharing platforms designed for real estate provide audit trails and access controls that email cannot match. These platforms track who accessed which documents and when.
Beyond secure communication, protection also depends on using wire fraud prevention platforms that analyze multiple risk markers instead of relying on individual security tools. Technology that examines device fingerprinting, geolocation, and cross-references with global government databases provides far stronger verification than manual processes alone.
2. Establish identity verification systems
Digital identity verification must go beyond visual inspection of driver's licenses. Effective verification cross-references multiple databases, including AAMVA and DMV records, while analyzing device behavior and location data to detect anomalies.
High-risk scenarios demand verification at the very start of the transaction. Out-of-state parties, vacant land sales, and LLC transactions require additional scrutiny. A seller who refuses video verification or won't provide a selfie with their government ID should raise a red flag.
This isn’t a theoretical risk—77% of real estate professionals saw an increase in seller impersonation last year. Companies using advanced verification systems catch fraud attempts before they progress.
3. Implement transaction protection measures
Wire instruction verification should take place through secure platforms that encrypt every step of the wire process. These systems let you send, collect, and confirm wire instructions through channels criminals cannot intercept.
They validate recipient identity and banking information in under 60 seconds before any funds move. Instead of asking clients for voided checks or accepting wire details through unsecured emails, you request bank information through a secure platform. The technology analyzes device data, location information, and behavioral patterns to flag suspicious activity before transfers occur.
Insurance-backed verification combines secure verification protocols with wire fraud insurance coverage, providing financial protection only when due diligence procedures are followed.
Fraud prevention works best at scale. When one title company flags a fraudulent account, that information protects the entire network—creating defensive capabilities that isolated firms working alone could never achieve.
4. Train teams and create security protocols
As fraud attacks surge, staff training must be non-negotiable and ongoing. Regular fraud simulation exercises provide the most effective training.
Run realistic scenarios where employees practice:
- Responding to suspicious emails
- Unexpected wire instruction changes
- Urgent requests during busy closing periods
These hands-on drills reveal gaps far better than passive courses. When staff experience a simulated phishing attack, they recognize real ones immediately.
Training is only half the equation; teams also need a clear plan for when incidents occur. Establish incident response workflows that account for the time-sensitive nature of fraud recovery. Quick action within 24 hours improves outcomes.
Every employee should know exactly who to contact and what steps to take if they suspect wire fraud. Confusion costs time you can't afford to lose.
Compliance and risk management for real estate professionals
State and federal regulations affecting title companies and attorneys continue evolving as cybersecurity threats intensify. Professional liability now extends beyond traditional title issues to include cybersecurity negligence, with courts holding professionals accountable for failing to implement reasonable security measures.
Our data shows that while 28% of title companies reported having customers send funds to wrong accounts due to fraud, existing insurance often provides no protection.
Cybersecurity in real estate: stay on top of fraud attempts
From our research, 65% of protected transactions reveal attempted fraud, and first-time buyers are three times more likely to be victimized than experienced buyers. With AI-powered threats scaling faster than manual defenses can respond, prevention is no longer optional.
Consumers are taking notice: 79% say they would pay a premium for security-focused firms, making cybersecurity both a liability protection and a competitive advantage. Request a demo to see how technology-backed verification protects your transactions before fraud strikes.
.png)
FAQ
What is the biggest cybersecurity risk in real estate transactions?
Business email compromise represents the biggest cybersecurity risk, accounting for nearly $500 million in annual losses across the real estate industry. BEC attacks exploit the communication-heavy nature of real estate transactions, with fraudsters impersonating real estate agents (58% of cases), title companies (41%), and even loan officers (34%) to redirect funds.
How can title companies prevent business email compromise?
Title companies prevent BEC through layered defense strategies rather than single solutions. Start with two-factor authentication on all email accounts and implement secure communication channels for wire instructions.
Deploy technology platforms that analyze 150+ risk markers—including device fingerprinting, geolocation analysis, and database cross-referencing—rather than relying solely on manual verification methods.
What should closing attorneys look for in cybersecurity solutions?
Closing attorneys need solutions offering integration with existing workflows, insurance backing, and selective scalability. Prioritize solutions built specifically for law firms rather than generic business security tools that don't address industry-specific threats.
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
According to our State of Wire Fraud report, the real estate industry loses nearly $500 million annually to business email compromise attacks (BEC)—yet most firms invest almost nothing in prevention.
Even more alarming, 29% of title companies spend less than $1,000 per year on cybersecurity, and 20% spend nothing at all, despite handling millions in client funds every month.
This isn't just an IT problem. It's a fiduciary responsibility that impacts your professional liability and client trust.
Whether you're running a title company or managing a law closing practice, understanding cybersecurity in real estate is the difference between protecting your business and becoming the next fraud statistic.
Cybersecurity in real estate: Why the industry is under siege now
Cybersecurity in real estate means protecting sensitive financial data, wire transfer information, and personal client details from cybercriminals who exploit vulnerabilities during property transactions.
Real estate transactions are usually complex, with multiple parties involved, so the industry faces unique threats that other industries rarely encounter.

Property records and listings create a publicly available goldmine for fraudsters. For just a few hundred dollars monthly, criminals can subscribe to APIs that provide detailed:
- Transaction information
- Party names
- Closing dates
- Transaction values
These data points give criminals all the insight they need to strike at the right moment. The numbers tell a troubling story.
Transactions averaging $429K, combined with 32% all-cash buyers and consumers who only purchase homes once every fifteen years, create perfect conditions for fraud. Most buyers and sellers lack the experience to spot scams, making them vulnerable to attacks that seasoned professionals might catch.
The industry's historically low IT infrastructure requirements compound these vulnerabilities. While other sectors invested heavily in cybersecurity over the past decade, real estate operated under inconsistent state-by-state regulations.
5 most common cybersecurity threats in real estate
Beyond BEC, real estate professionals face evolving threats that exploit industry-specific vulnerabilities. Each threat shares a common characteristic: they target transaction points where large sums of money change hands.
1. Ransomware attacks
Ransomware attacks begin when criminals gain access to your systems—usually through phishing emails, outdated software, or stolen passwords.
Once inside, they lock your company data and demand payment to unlock it. Title companies and law firms are prime targets because of tight closing deadlines and valuable client information.
The pressure can be intense. When your systems are locked and a $500,000 closing is scheduled for tomorrow, paying the ransom feels like the only option.
Missing a closing deadline can kill a deal, trigger legal claims, and destroy client relationships. Operations grind to a halt, leading to major losses. Worse yet, sometimes the data stays locked even after paying—criminals hardly keep their word.
You can reduce ransomware risk by keeping software updated, backing up data regularly on separate systems, and using security software that catches threats early.
2. Seller impersonation fraud
Seller impersonation fraud is one of the fastest-growing schemes in real estate. Fraudsters pose as property owners to list and sell properties they don't own, pocketing proceeds before anyone realizes the real owner never authorized the sale.
These schemes particularly target vacant land sales, out-of-state transactions, and LLC-owned properties where verification is traditionally harder.

The financial impact can be devastating for all parties involved. Buyers lose their down payments, title companies face liability claims, and rightful property owners must navigate legal battles to reclaim their assets. Starting transactions with advanced identity verification provides the strongest defense against these schemes.

3. Data breaches
Data breaches expose far more than basic contact information. Real estate companies hold substantial volumes of sensitive information—personal details of buyers and sellers, financial records, and full transaction histories. The interconnected nature of real estate databases means a single breach can compromise multiple transactions.
When a title company's systems are compromised, fraudsters gain access to closing dates, party names, transaction amounts, and established communication patterns.
The financial cost includes direct losses, reputational damage, and potential legal consequences.
To reduce these risks, proper data encryption and access controls provide critical protection, ensuring that even if unauthorized individuals gain access, they cannot exploit the information.

4. Phishing and social engineering attacks
Phishing and social engineering attacks exploit human trust rather than technical vulnerabilities. Employees receive legitimate-looking emails or messages requesting sensitive information or system access. Attackers study your communication patterns and strike during busy closing periods.
The best defense combines employee training with technical safeguards. Teams need regular education on recognizing phishing attempts, verifying email addresses before clicking links, and reporting suspicious communications. Email filtering solutions and zero-trust policies—requiring verification at every step—provide additional layers of protection against these attacks.
5. AI-powered deepfake attacks
The newest frontier involves AI-powered deepfake attacks that create convincing voice recordings and video calls impersonating trusted parties.
Traditional callback verification methods become less reliable when criminals can clone voices in real time. What sounds like a lender confirming payoff instructions might be a fraudster using voice synthesis technology.
These attacks represent a shift in threat sophistication. Human detection methods are no longer sufficient against current threat levels.
Protection requires technology platforms with access to extensive databases of verified lender information. These eliminate the guesswork and provide instant validation against thousands of known lenders.
Modern systems can verify payoff instructions in under 60 seconds, replacing manual calls and faxes with automated processing that centralises all payoff details in one dashboard.
Best practices for real estate cybersecurity
Protecting your business requires a layered approach that addresses both technology and human factors. No single solution provides complete protection—effective cybersecurity combines multiple defensive strategies.
1. Implement secure communication protocols
Move beyond basic email encryption to establish verified communication channels for all transaction-related correspondence.
Multi-factor authentication should be mandatory for accessing any system containing wire transfer information. Single-factor password protection is insufficient—fraudsters can compromise passwords through phishing or data breaches.
Secure document sharing platforms designed for real estate provide audit trails and access controls that email cannot match. These platforms track who accessed which documents and when.
Beyond secure communication, protection also depends on using wire fraud prevention platforms that analyze multiple risk markers instead of relying on individual security tools. Technology that examines device fingerprinting, geolocation, and cross-references with global government databases provides far stronger verification than manual processes alone.
2. Establish identity verification systems
Digital identity verification must go beyond visual inspection of driver's licenses. Effective verification cross-references multiple databases, including AAMVA and DMV records, while analyzing device behavior and location data to detect anomalies.
High-risk scenarios demand verification at the very start of the transaction. Out-of-state parties, vacant land sales, and LLC transactions require additional scrutiny. A seller who refuses video verification or won't provide a selfie with their government ID should raise a red flag.
This isn’t a theoretical risk—77% of real estate professionals saw an increase in seller impersonation last year. Companies using advanced verification systems catch fraud attempts before they progress.
3. Implement transaction protection measures
Wire instruction verification should take place through secure platforms that encrypt every step of the wire process. These systems let you send, collect, and confirm wire instructions through channels criminals cannot intercept.
They validate recipient identity and banking information in under 60 seconds before any funds move. Instead of asking clients for voided checks or accepting wire details through unsecured emails, you request bank information through a secure platform. The technology analyzes device data, location information, and behavioral patterns to flag suspicious activity before transfers occur.
Insurance-backed verification combines secure verification protocols with wire fraud insurance coverage, providing financial protection only when due diligence procedures are followed.
Fraud prevention works best at scale. When one title company flags a fraudulent account, that information protects the entire network—creating defensive capabilities that isolated firms working alone could never achieve.
4. Train teams and create security protocols
As fraud attacks surge, staff training must be non-negotiable and ongoing. Regular fraud simulation exercises provide the most effective training.
Run realistic scenarios where employees practice:
- Responding to suspicious emails
- Unexpected wire instruction changes
- Urgent requests during busy closing periods
These hands-on drills reveal gaps far better than passive courses. When staff experience a simulated phishing attack, they recognize real ones immediately.
Training is only half the equation; teams also need a clear plan for when incidents occur. Establish incident response workflows that account for the time-sensitive nature of fraud recovery. Quick action within 24 hours improves outcomes.
Every employee should know exactly who to contact and what steps to take if they suspect wire fraud. Confusion costs time you can't afford to lose.
Compliance and risk management for real estate professionals
State and federal regulations affecting title companies and attorneys continue evolving as cybersecurity threats intensify. Professional liability now extends beyond traditional title issues to include cybersecurity negligence, with courts holding professionals accountable for failing to implement reasonable security measures.
Our data shows that while 28% of title companies reported having customers send funds to wrong accounts due to fraud, existing insurance often provides no protection.
Cybersecurity in real estate: stay on top of fraud attempts
From our research, 65% of protected transactions reveal attempted fraud, and first-time buyers are three times more likely to be victimized than experienced buyers. With AI-powered threats scaling faster than manual defenses can respond, prevention is no longer optional.
Consumers are taking notice: 79% say they would pay a premium for security-focused firms, making cybersecurity both a liability protection and a competitive advantage. Request a demo to see how technology-backed verification protects your transactions before fraud strikes.
.png)
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Sign up for The Wire to join the conversation.