Wire fraud prevention: 22 best practices for title and law companies in 2026
Real estate wires are still a top target. Here’s how title teams and attorneys fight back.
.png)
Tom Cronkright
10 minutes
Fraud Prevention
Jul 19, 2021
Dec 8, 2025
Key takeaways
- Wire fraud cost businesses $446 million in 2023 through business email compromise schemes. Title companies and law firms face the highest risk during real estate closings when multiple parties exchange sensitive financial information.
- Essential prevention measures include multifactor authentication, never sending wire instructions via email, and implementing documented verification procedures for every wire transfer. These foundational practices apply to all organizations handling wire transfers.
- Title companies and law firms require specialized protocols, including multi-party identity verification, closing-day security systems, and compliance with ALTA or state bar requirements. High-risk transactions demand dual approvals and enhanced verification regardless of relationship history.
A pristine driver's license. A legitimate bank account at a reputable financial institution. Solid paperwork.
Despite safeguards, it still happens that victims lose substantial sums to scammers. In one case, a victim lost $500,000 to a scammer who forged the seller's identity.
In 2023, fraudsters stole $446 million through business email scams in real estate transactions. This information comes from the FBI IC3's Internet Crime Report.
.png)
Whether you're a title company or a law firm handling domestic wire transfers, you must protect yourself.
In this article, we'll share wire fraud prevention best practices for both title agency professionals and attorneys, starting with common wire fraud examples.
22 essential wire fraud prevention best practices
Wire fraud prevention starts with the basics. Before you implement industry-specific protocols, you need a foundation of security measures that protect every transaction. The best prevention strategy combines technology, process, and people working together to create layers of defense.
Here are the essential wire fraud prevention best practices every organization should implement.
Best practice 1: Use multifactor authentication for all financial systems
Require two or more verification methods before authorizing wire transfers. Multifactor authentication combines a password (something you know), a phone or security token (something you have), and a fingerprint or facial recognition (something you are).
Passwords alone aren't enough protection. Set up multifactor authentication on your banking portals, title production software, and email accounts. The extra 30 seconds at login prevent unauthorized access.
Best practice 2: Never send wire instructions via email
Email is easily spoofed and intercepted. Password-protected PDFs don't provide real security.
Use secure portals, encrypted platforms, or specialized phone verification. When you receive wire instructions via email, verify them independently. Use a phone number you researched yourself, not one provided in the email. This prevents fraudsters from intercepting communications.
Best practice 3: Implement verification procedures for every wire transfer
Create documented procedures for every single wire transfer. Your procedures should specify when verification happens. Define what information gets verified. Identify who performs the verification. Write these procedures down. Train every team member on them. Consistent procedures prevent fraud.
Best practice 4: Double-check email addresses character by character
Fraudsters change just one letter in legitimate email addresses. They use "certifid.com" instead of "certifid.com."
Before acting on any wire-related communication, verify sender addresses. Check the full email address, not just the display name. Fraudsters can make display names look identical to trusted contacts.
Best practice 5: Slow down when urgency increases
Pressure to rush is a common fraud tactic. Late Friday afternoon requests deserve extra scrutiny. Last-minute changes to wire instructions require verification.
Demands to process transfers immediately are red flags. Build buffer time into your closing schedules. Legitimate parties will understand the need for proper verification.
Best practice 6: Use a secure network for all financial transactions
Process wire transfers only on secure, encrypted networks. Never use public WiFi for financial transactions. Public networks create opportunities for fraudsters to intercept communications.
Implement VPNs for remote workers. Set up firewalls that alert you to suspicious network activity. Restrict access to financial systems based on IP addresses.
Best practice 7: Implement authentication protocols across all systems
Authentication protocols define who can access what systems. Not everyone needs access to wire transfer capabilities.
Set up role-based access controls. Limit financial system access to specific team members. Require periodic re-authentication. Log all access attempts. Review these logs regularly for suspicious patterns.
Best practice 8: Understand and prevent business email compromise
Business email compromise is a targeted phishing attack. Criminals impersonate trusted parties. These emails use realistic language.
They make wire transfer requests that seem legitimate. Train your team to recognize red flags. Watch for urgent requests, slight changes to email addresses, and requests that bypass normal procedures.
Best practice 9: Educate your entire team on current fraud schemes
Fraudsters evolve their tactics constantly. Monthly fraud prevention training sessions keep everyone alert. Cover real examples of recent fraud attempts in your market.
Discuss the specific tactics fraudsters used. Make training practical, not theoretical. Create a culture where team members question suspicious requests.
Best practice 10: Maintain wire fraud insurance coverage
Insurance provides a financial safety net if fraud occurs. Look for policies offering up to $5 million in coverage per file. Understand what your policy covers. Know what it excludes. Review your coverage annually as your transaction volume grows.
Best practice 11: Raise phishing awareness across your organization
Phishing is the most common entry point for wire fraud. Fraudsters use phishing to steal credentials. They install malware and learn about upcoming transactions.
Conduct regular phishing simulations. Test your team's awareness. Teach specific skills like how to verify sender addresses. Explain why they should never enter credentials on pages reached through email links.
Best practice 12: Strengthen password management practices
Weak passwords give fraudsters easy access. Implement complex password requirements. Require a minimum length and special characters.
Use a password manager. Team members can maintain unique, strong passwords for every system. Never share passwords between team members. Each person needs their own credentials.
Best practice 13: Implement a comprehensive cybersecurity policy
A cybersecurity policy in real estate documents your security procedures. It defines roles and responsibilities. It sets standards for technology use across your organization. Your policy should cover acceptable use of devices. Include password requirements and data handling procedures. Define incident response protocols. Review and update your policy annually.
Prevent wire transfer fraud: 9 specialized best practices for title companies and law firm
Best practice 14: Implement multi-party verification systems
Your transaction involves multiple parties—buyers, sellers, agents, and lenders.
Each represents a potential for wire transfer fraud.
These transactions necessitate secure verification of wire instructions, payoff amounts, and disbursement details to prevent fraud.
.gif)
As a title company, set a process where you verify multiple parties in the system.
In the context of a real estate closing, verifying the buyer's identity confirms their authority to proceed with the purchase.
Likewise, verifying the seller's identity ensures they are the rightful property owner and prevents fraudsters from diverting funds to unauthorized accounts.
To do so, you can use CertifID Match. They’ll have to complete the following steps:

Specifically, identity verification requires involved parties to:
- Scan their government-issued ID to confirm their identity
- Verify their phone number through a secure text code
- Take a selfie
- Answer unique security questions
- Complete device verification to flag any suspicious logins or locations
To securely share and receive wiring instructions, you should establish a process that each of your employees follows.

Best practice 15: Establish closing-day security protocols
Closing day presents peak vulnerability for wire fraud.
It’s because things get hectic, and your employees want to finally close the deal. Especially if it’s late Friday afternoon.
With multiple transactions happening simultaneously and pressure to meet deadlines, fraudsters know exactly when to strike.
A closing-day security system acts as your safety net. For example, you can set specific guidelines that cover each stage of real estate transactions:
Pre-closing
- Verify contact information: Confirm the identities and contact details of all parties. Verify the identities of parties that might be more vulnerable in the whole chain.
- Review wire instructions: Validate wire instructions directly with the sender through CertifID Confirm.
Closing
- Execute wire transfer: Use a dual-verification process where two authorized team members approve the transfer.
- Alternatively, for extra security, use a secure digital payment system
Post-closing
- Confirm Receipt: Verify that funds have reached the correct accounts and notify all stakeholders.
- Document the Transaction: Record all details of the transaction in your title production software for compliance and audit purposes.
.png)
Also, a good practice is to start with pre-closing verification three to five days before the big day. This buffer allows time to resolve any red flags without delaying the closing.
On the closing day itself, implement mandatory wire instruction verification before any transfers occur. The thing is, wire transfers can’t be reversed, so it’s better to apply extra caution.
Follow up with a post-closing confirmation to ensure funds reach their intended destination.
Best practice 16: Protect every transaction
While you may handle both routine residential closings and multi-million-dollar commercial deals, each deserves thorough protection.
Create a verification system that protects all transactions:
- High-stakes transactions—including large amounts, out-of-state parties, or complex commercial deals—receive enhanced verification and manual checks
- All other transactions, including standard residential closings, undergo thorough verification, ensuring every deal is properly secured
Monitor multiple closings through your title production software integrated with CertifID.
See a short video on how, without leaving Softpro, you can make high-stakes transactions secure.
From a centralized software, track verification status, receive alerts for pending tasks, and identify suspicious activities in (almost) real time. Most importantly, follow these security protocols consistently for every transaction, every time.
.png)
Best practice 17: Secure seller proceeds distribution
As a title company, seller proceeds aren't only about sending the final amount to the property seller. It also involves mortgage payoff to the lender and sending settlement fees and commission costs.
Just take a look at how complex the landscape gets.

What you need to do here is make sure:
- You’ve got the right wiring instructions from the seller to send them the net proceeds
- You’ve got the right wiring instructions from the lender to send the mortgage payoff
Let's talk about securing those seller proceeds first.
The safest way to collect wiring instructions is through a secure verification platform.
Your seller gets a link where they can quickly verify the authenticity of their identity by scanning their ID, confirming their phone number, and providing a selfie.
The best part is that the entire process can be completed on a smartphone, making it quick and convenient for everyone involved.
If a fraudster attempts to deceive you, they won't be able to use excuses like "I don't have access to a laptop while traveling," as the mobile-friendly verification process leaves no room for such claims.
This method also beats the old email method, where fraudsters could intercept and change bank details.
Plus, why make your sellers wait for a check to clear when you can give them instant access to their funds through a secure wire? It's about providing that smooth, professional experience they expect.
Now for mortgage payoffs.
You’ve probably spent hours making phone calls with lenders to verify wiring details.
Not only is it a hassle, but there's a catch: even if someone at the lender confirms details over the phone, you could still be on the hook if the money goes to the wrong place.
As Melissa Deml, Chief Operating Officer at TitleSmart, puts it:
"We see those [payoff details] change every time and that knowledge really isn't something that you can teach someone in a quick session or bundle that and install it in someone's brain... That risk assessment really builds up—it's a lot of stress. We're only human, even these people who are the last person to click that button before the funds go off."
Watch Melissa's full story here:
Best practice 18: Follow ALTA’s best practices
Following ALTA's best practices is about building security procedures that actually work day-to-day.
Write down your steps, check them regularly, and keep clear records of your verifications. This protects your business and shows your clients you take their security seriously.
As ALTA CEO Diane Tomb puts it, "Our industry is amazing. They're people who want to get it done. We go to the 11th hour, and we do everything accurately."
She's right—title professionals like you do more than just close deals.
They're now at the forefront of protecting consumers from fraud and ensuring the security of homeownership.
When you build security workflows that follow ALTA's guidelines, you're doing your part to protect homeownership. Good documentation shows everyone you mean business about keeping transactions secure.
Best practice 19: Protect client trust accounts
Law firms, especially in attorney states, face unique challenges with remote transactions.

Security gets especially important when attorneys like you are dealing with more tangled cases.
Take out-of-state LLCs with complex ownership structures. For example, where one LLC is owned by an LLC in another state.
Such cases require extra scrutiny because, as a lawyer, you’re responsible for sending money to the right people. To manage this, you should put in place matter-specific protocols and implement dual control measures for high-risk transfers.
For example, this could be how you review transactions:
.png)
Best practice 20: Maintain attorney-client privilege
Law firms like yours face a bit of a different challenge compared to title companies.
They must balance security with strict confidential information protection. While protecting transactions from fraud, they must also ensure every security measure maintains attorney-client privilege.
Here, everything is centered around accessing customers’ sensitive information after authorization. Every verification step, every security check, and every communication must happen within this protected space.
When your company implements fraud prevention tools, it needs systems that:
- Protect confidential communications while verifying identities
- Secure document sharing without exposing privileged information
- Create audit trails that respect client confidentiality
- Allow secure third-party access when necessary
For example, a combination of title production software and a secure tool that lets you verify wiring instructions and payoff details.
Besides, your communication has to happen through secure channels.
Take a look at the model that will let you understand layers of protection for the closing transactions.

Best practice 21: Follow bar association requirements
State bars across the country are intensifying their focus on wire fraud prevention.
And they have good reasons.
The threats are evolving beyond simple email account compromises to sophisticated identity theft.
What does this mean for your practice?
Your verification process must be thorough and well-documented from the moment you open a file until the final disbursement.
Take a real scenario: An Alabama LLC owned by a Utah LLC wants to buy a vacant lot in your county. The property purchase came from an unsolicited offer, and they're not coming to closing. Red flags like these require extra verification steps.
Modern identity verification makes this process simple:
- Send a verification request via text or email
- Remote parties scan their government-issued ID and take a selfie
- Get instant validation status
Your documentation should show you verified the complex ownership structure, validated identities, and payment instructions, and maintained a clear audit trail.
Remember: Your state bar's requirements are ultimately to protect your reputation and customers’ money.
Best practice 22: Secure matter transactions and partner oversight
Think of it as a risk-based security system, like having different levels of security clearance.
Not every transaction needs top-level security, but you need clear rules about who can approve what.
For example, earnest money deposits might need only basic verification, while large closing funds demand enhanced security measures and partner review.
Create clear authorization matrices defining who can approve different transaction types and amounts.
Another example, especially when setting priorities:
Local family home sale ($300,000)
- Sellers are long-time residents
- Buyers are local with a conventional loan
- In-person closing planned → Standard verification process, staff can handle
Commercial building purchase ($2.5M)
- Buyer is a foreign investment group
- Multiple LLCs involved
- Remote closing requested → Requires partner oversight, enhanced security
For example, your office and your paralegal team are handling a $2.5M commercial deal.
Your system automatically flags it for high-risk protocol, requiring:
- Partner review and approval
- Identity verification of all parties before opening the file
- Documented ownership structure validation
- Secure wire instruction collection
- Two-person approval for final wire transfer
The goal is to have clear, automated protocols that scale up security based on risk factors.
Here’s how you could approach the authorization levels:

3 real-world wire fraud examples and practical prevention measures
"Nothing about this one seemed out of the ordinary," says Mike Musto, who lost $600,000 to fraudsters who changed just one letter in his closing team's email addresses.
Though Mike recovered his funds after weeks of working with banks and law enforcement, many victims aren't so fortunate.
Let's examine the most common wire fraud scams to help you stay vigilant and protect your business.
- Business email compromise (BEC) fraud
BEC is a targeted phishing attack (part of social engineering scams) where criminals impersonate trusted parties.
These emails often make wire transfer requests or use realistic language to avoid detection. Unlike mass phishing, BEC is tailored for the receiving party.
And this poses a big threat to firms handling sensitive financial transactions. Because as a professional, you’re often liable for the fraudulent transfer if your account is compromised.
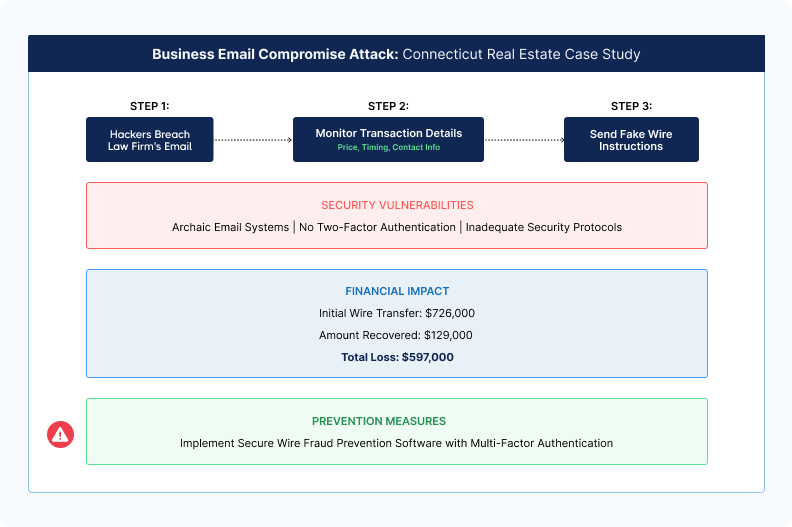
In 2024, a Connecticut homebuyer, Richard Bates, lost $597,000 after receiving a fraudulent email with fake wire instructions.
The hackers had accessed sensitive transaction details by breaching the law firm's emails involved in the transaction.
Bates, believing the email to be legitimate, wired the funds, of which only $129,000 was recovered.
- Seller impersonation scam
Seller impersonation is a scam where fraudsters impersonate the owner of a vacant or rarely monitored property to sell it fraudulently and steal the proceeds.
Using forged documents and fake identities, they list the property below market value for quick sales, often insisting on remote closings to evade detection.
Watch as Tom Cronkright, our executive chairman of CertifID, explains the ins and outs of seller impersonation fraud.
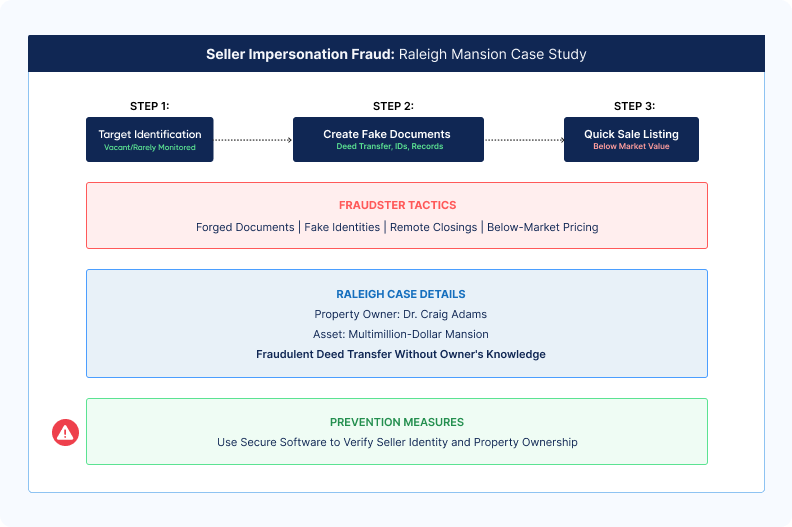
In Raleigh, North Carolina, dentist Craig Adams discovered that his multimillion-dollar mansion's deed had been fraudulently transferred.
The scammer listed the property for sale without his consent, disappearing with the proceeds before the fraud was detected.
- Mortgage payoff fraud
A growing scam where fraudsters impersonate mortgage lenders to divert payoff funds during real estate transactions.
Using phishing or hacking, they intercept and alter payoff instructions, pressuring title companies and/or law practices with urgent requests.
According to our 2024 State of Wire Fraud report, this accounted for 47% of all real estate wire fraud losses in 2022.
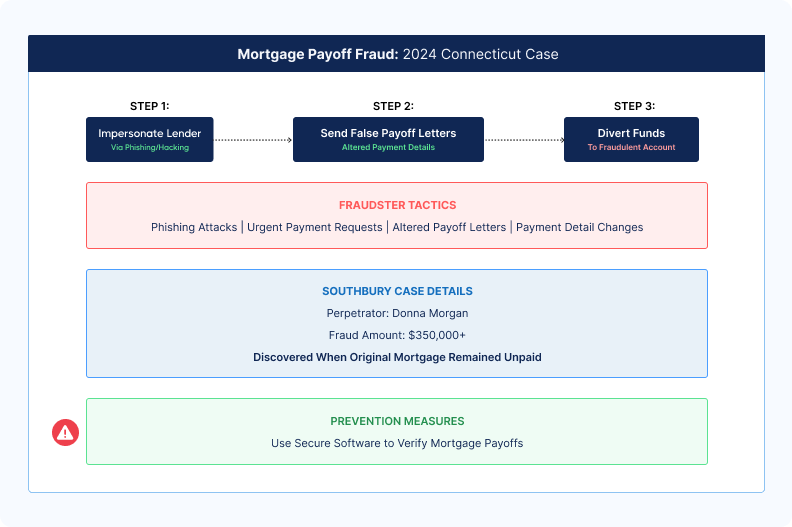
In 2024, Donna Morgan was charged in a Southbury, Connecticut, mortgage payoff scam that defrauded over $350,000. Morgan sent falsified payoff letters to a real estate attorney, altering the payee information to divert funds into her account.
The fraud was uncovered after the seller reported that their mortgage remained unpaid, leading to her arrest.
Now that you're familiar with the common types of wire fraud scams, let's explore how to prevent them and protect your business.
How to prevent wire fraud: Implement these best practices and stay fraud-free
With these strategies, your organization will be protected from wire fraud, which will benefit you and safeguard your customers' personal data.
While title companies and attorneys have specific best practices, there's one prevention tip that applies to both: consistent team training.
Regular training sessions should focus on:
- Identifying transaction-specific red flags
- Practicing multi-party coordination
- Testing phishing awareness
Document all procedures so team members have a clear reference when questions arise.
To add an extra layer of security to your title production software and verify high-risk transactions, request a CertifID demo.

FAQ
When should I verify identities during the closing process?
Verify identities when you open the file, not at closing. By the time closing day arrives, you're under time pressure and less likely to push back on questionable documentation.
Early verification gives you time to dig deeper, request additional documents, and contact property owners through independently verified channels without derailing the closing timeline.
Can I send wire instructions via email if they're in a password-protected PDF?
No. Email is easily spoofed, compromised, and intercepted, regardless of how you format the attachment.
Business email compromise schemes specifically target wire instructions sent via email. Use secure portals and callbacks via trusted partners exclusively. When clients send wire instructions via email anyway, treat them as automatically suspicious and require callback verification.
What makes a transaction high-risk for wire fraud?
All-cash deals, out-of-state sellers, properties with recent ownership changes, and transactions involving powers of attorney carry elevated risk. Also watch for rushed closings, last-minute wire instruction changes, sellers who avoid phone calls, and situations where communication happens exclusively through email.
These scenarios deserve additional verification layers, including knowledge-based authentication and enhanced identity checks.
What should I do if I receive last-minute updated wire instructions?
Treat any wire instruction changes as suspicious, especially those arriving via email. Stop the process immediately and verify through a different communication channel using contact information you independently confirmed earlier.
Call the party directly using a phone number you researched yourself, not one provided in the update message. Never process same-day wire instruction changes without multiple-channel verification.
What are some red flags that title companies and law firms should watch for?
Common red flags include last-minute changes to wiring instructions, pressure to send funds quickly, requests coming late on a Friday or near a holiday, remote parties who refuse video or identity verification, and properties that are vacant, out-of-state, or priced below market value.
Complex ownership structures, such as layered LLCs in multiple states, unsolicited offers on vacant land, and requests for remote closings, also call for extra verification. Staff should treat these situations as high risk and follow enhanced verification protocols before sending any funds.
Co-founder & Executive Chairman
Tom Cronkright is the Executive Chairman of CertifID, a technology platform designed to safeguard electronic payments from fraud. He co-founded the company in response to a wire fraud he experienced and the rising instances of real estate wire fraud. He also serves as the CEO of Sun Title, a leading title agency in Michigan. Tom is a licensed attorney, real estate broker, title insurance producer and nationally recognized expert on cybersecurity and wire fraud.
Key takeaways
- Wire fraud cost businesses $446 million in 2023 through business email compromise schemes. Title companies and law firms face the highest risk during real estate closings when multiple parties exchange sensitive financial information.
- Essential prevention measures include multifactor authentication, never sending wire instructions via email, and implementing documented verification procedures for every wire transfer. These foundational practices apply to all organizations handling wire transfers.
- Title companies and law firms require specialized protocols, including multi-party identity verification, closing-day security systems, and compliance with ALTA or state bar requirements. High-risk transactions demand dual approvals and enhanced verification regardless of relationship history.
A pristine driver's license. A legitimate bank account at a reputable financial institution. Solid paperwork.
Despite safeguards, it still happens that victims lose substantial sums to scammers. In one case, a victim lost $500,000 to a scammer who forged the seller's identity.
In 2023, fraudsters stole $446 million through business email scams in real estate transactions. This information comes from the FBI IC3's Internet Crime Report.
.png)
Whether you're a title company or a law firm handling domestic wire transfers, you must protect yourself.
In this article, we'll share wire fraud prevention best practices for both title agency professionals and attorneys, starting with common wire fraud examples.
22 essential wire fraud prevention best practices
Wire fraud prevention starts with the basics. Before you implement industry-specific protocols, you need a foundation of security measures that protect every transaction. The best prevention strategy combines technology, process, and people working together to create layers of defense.
Here are the essential wire fraud prevention best practices every organization should implement.
Best practice 1: Use multifactor authentication for all financial systems
Require two or more verification methods before authorizing wire transfers. Multifactor authentication combines a password (something you know), a phone or security token (something you have), and a fingerprint or facial recognition (something you are).
Passwords alone aren't enough protection. Set up multifactor authentication on your banking portals, title production software, and email accounts. The extra 30 seconds at login prevent unauthorized access.
Best practice 2: Never send wire instructions via email
Email is easily spoofed and intercepted. Password-protected PDFs don't provide real security.
Use secure portals, encrypted platforms, or specialized phone verification. When you receive wire instructions via email, verify them independently. Use a phone number you researched yourself, not one provided in the email. This prevents fraudsters from intercepting communications.
Best practice 3: Implement verification procedures for every wire transfer
Create documented procedures for every single wire transfer. Your procedures should specify when verification happens. Define what information gets verified. Identify who performs the verification. Write these procedures down. Train every team member on them. Consistent procedures prevent fraud.
Best practice 4: Double-check email addresses character by character
Fraudsters change just one letter in legitimate email addresses. They use "certifid.com" instead of "certifid.com."
Before acting on any wire-related communication, verify sender addresses. Check the full email address, not just the display name. Fraudsters can make display names look identical to trusted contacts.
Best practice 5: Slow down when urgency increases
Pressure to rush is a common fraud tactic. Late Friday afternoon requests deserve extra scrutiny. Last-minute changes to wire instructions require verification.
Demands to process transfers immediately are red flags. Build buffer time into your closing schedules. Legitimate parties will understand the need for proper verification.
Best practice 6: Use a secure network for all financial transactions
Process wire transfers only on secure, encrypted networks. Never use public WiFi for financial transactions. Public networks create opportunities for fraudsters to intercept communications.
Implement VPNs for remote workers. Set up firewalls that alert you to suspicious network activity. Restrict access to financial systems based on IP addresses.
Best practice 7: Implement authentication protocols across all systems
Authentication protocols define who can access what systems. Not everyone needs access to wire transfer capabilities.
Set up role-based access controls. Limit financial system access to specific team members. Require periodic re-authentication. Log all access attempts. Review these logs regularly for suspicious patterns.
Best practice 8: Understand and prevent business email compromise
Business email compromise is a targeted phishing attack. Criminals impersonate trusted parties. These emails use realistic language.
They make wire transfer requests that seem legitimate. Train your team to recognize red flags. Watch for urgent requests, slight changes to email addresses, and requests that bypass normal procedures.
Best practice 9: Educate your entire team on current fraud schemes
Fraudsters evolve their tactics constantly. Monthly fraud prevention training sessions keep everyone alert. Cover real examples of recent fraud attempts in your market.
Discuss the specific tactics fraudsters used. Make training practical, not theoretical. Create a culture where team members question suspicious requests.
Best practice 10: Maintain wire fraud insurance coverage
Insurance provides a financial safety net if fraud occurs. Look for policies offering up to $5 million in coverage per file. Understand what your policy covers. Know what it excludes. Review your coverage annually as your transaction volume grows.
Best practice 11: Raise phishing awareness across your organization
Phishing is the most common entry point for wire fraud. Fraudsters use phishing to steal credentials. They install malware and learn about upcoming transactions.
Conduct regular phishing simulations. Test your team's awareness. Teach specific skills like how to verify sender addresses. Explain why they should never enter credentials on pages reached through email links.
Best practice 12: Strengthen password management practices
Weak passwords give fraudsters easy access. Implement complex password requirements. Require a minimum length and special characters.
Use a password manager. Team members can maintain unique, strong passwords for every system. Never share passwords between team members. Each person needs their own credentials.
Best practice 13: Implement a comprehensive cybersecurity policy
A cybersecurity policy in real estate documents your security procedures. It defines roles and responsibilities. It sets standards for technology use across your organization. Your policy should cover acceptable use of devices. Include password requirements and data handling procedures. Define incident response protocols. Review and update your policy annually.
Prevent wire transfer fraud: 9 specialized best practices for title companies and law firm
Best practice 14: Implement multi-party verification systems
Your transaction involves multiple parties—buyers, sellers, agents, and lenders.
Each represents a potential for wire transfer fraud.
These transactions necessitate secure verification of wire instructions, payoff amounts, and disbursement details to prevent fraud.
.gif)
As a title company, set a process where you verify multiple parties in the system.
In the context of a real estate closing, verifying the buyer's identity confirms their authority to proceed with the purchase.
Likewise, verifying the seller's identity ensures they are the rightful property owner and prevents fraudsters from diverting funds to unauthorized accounts.
To do so, you can use CertifID Match. They’ll have to complete the following steps:

Specifically, identity verification requires involved parties to:
- Scan their government-issued ID to confirm their identity
- Verify their phone number through a secure text code
- Take a selfie
- Answer unique security questions
- Complete device verification to flag any suspicious logins or locations
To securely share and receive wiring instructions, you should establish a process that each of your employees follows.

Best practice 15: Establish closing-day security protocols
Closing day presents peak vulnerability for wire fraud.
It’s because things get hectic, and your employees want to finally close the deal. Especially if it’s late Friday afternoon.
With multiple transactions happening simultaneously and pressure to meet deadlines, fraudsters know exactly when to strike.
A closing-day security system acts as your safety net. For example, you can set specific guidelines that cover each stage of real estate transactions:
Pre-closing
- Verify contact information: Confirm the identities and contact details of all parties. Verify the identities of parties that might be more vulnerable in the whole chain.
- Review wire instructions: Validate wire instructions directly with the sender through CertifID Confirm.
Closing
- Execute wire transfer: Use a dual-verification process where two authorized team members approve the transfer.
- Alternatively, for extra security, use a secure digital payment system
Post-closing
- Confirm Receipt: Verify that funds have reached the correct accounts and notify all stakeholders.
- Document the Transaction: Record all details of the transaction in your title production software for compliance and audit purposes.
.png)
Also, a good practice is to start with pre-closing verification three to five days before the big day. This buffer allows time to resolve any red flags without delaying the closing.
On the closing day itself, implement mandatory wire instruction verification before any transfers occur. The thing is, wire transfers can’t be reversed, so it’s better to apply extra caution.
Follow up with a post-closing confirmation to ensure funds reach their intended destination.
Best practice 16: Protect every transaction
While you may handle both routine residential closings and multi-million-dollar commercial deals, each deserves thorough protection.
Create a verification system that protects all transactions:
- High-stakes transactions—including large amounts, out-of-state parties, or complex commercial deals—receive enhanced verification and manual checks
- All other transactions, including standard residential closings, undergo thorough verification, ensuring every deal is properly secured
Monitor multiple closings through your title production software integrated with CertifID.
See a short video on how, without leaving Softpro, you can make high-stakes transactions secure.
From a centralized software, track verification status, receive alerts for pending tasks, and identify suspicious activities in (almost) real time. Most importantly, follow these security protocols consistently for every transaction, every time.
.png)
Best practice 17: Secure seller proceeds distribution
As a title company, seller proceeds aren't only about sending the final amount to the property seller. It also involves mortgage payoff to the lender and sending settlement fees and commission costs.
Just take a look at how complex the landscape gets.

What you need to do here is make sure:
- You’ve got the right wiring instructions from the seller to send them the net proceeds
- You’ve got the right wiring instructions from the lender to send the mortgage payoff
Let's talk about securing those seller proceeds first.
The safest way to collect wiring instructions is through a secure verification platform.
Your seller gets a link where they can quickly verify the authenticity of their identity by scanning their ID, confirming their phone number, and providing a selfie.
The best part is that the entire process can be completed on a smartphone, making it quick and convenient for everyone involved.
If a fraudster attempts to deceive you, they won't be able to use excuses like "I don't have access to a laptop while traveling," as the mobile-friendly verification process leaves no room for such claims.
This method also beats the old email method, where fraudsters could intercept and change bank details.
Plus, why make your sellers wait for a check to clear when you can give them instant access to their funds through a secure wire? It's about providing that smooth, professional experience they expect.
Now for mortgage payoffs.
You’ve probably spent hours making phone calls with lenders to verify wiring details.
Not only is it a hassle, but there's a catch: even if someone at the lender confirms details over the phone, you could still be on the hook if the money goes to the wrong place.
As Melissa Deml, Chief Operating Officer at TitleSmart, puts it:
"We see those [payoff details] change every time and that knowledge really isn't something that you can teach someone in a quick session or bundle that and install it in someone's brain... That risk assessment really builds up—it's a lot of stress. We're only human, even these people who are the last person to click that button before the funds go off."
Watch Melissa's full story here:
Best practice 18: Follow ALTA’s best practices
Following ALTA's best practices is about building security procedures that actually work day-to-day.
Write down your steps, check them regularly, and keep clear records of your verifications. This protects your business and shows your clients you take their security seriously.
As ALTA CEO Diane Tomb puts it, "Our industry is amazing. They're people who want to get it done. We go to the 11th hour, and we do everything accurately."
She's right—title professionals like you do more than just close deals.
They're now at the forefront of protecting consumers from fraud and ensuring the security of homeownership.
When you build security workflows that follow ALTA's guidelines, you're doing your part to protect homeownership. Good documentation shows everyone you mean business about keeping transactions secure.
Best practice 19: Protect client trust accounts
Law firms, especially in attorney states, face unique challenges with remote transactions.

Security gets especially important when attorneys like you are dealing with more tangled cases.
Take out-of-state LLCs with complex ownership structures. For example, where one LLC is owned by an LLC in another state.
Such cases require extra scrutiny because, as a lawyer, you’re responsible for sending money to the right people. To manage this, you should put in place matter-specific protocols and implement dual control measures for high-risk transfers.
For example, this could be how you review transactions:
.png)
Best practice 20: Maintain attorney-client privilege
Law firms like yours face a bit of a different challenge compared to title companies.
They must balance security with strict confidential information protection. While protecting transactions from fraud, they must also ensure every security measure maintains attorney-client privilege.
Here, everything is centered around accessing customers’ sensitive information after authorization. Every verification step, every security check, and every communication must happen within this protected space.
When your company implements fraud prevention tools, it needs systems that:
- Protect confidential communications while verifying identities
- Secure document sharing without exposing privileged information
- Create audit trails that respect client confidentiality
- Allow secure third-party access when necessary
For example, a combination of title production software and a secure tool that lets you verify wiring instructions and payoff details.
Besides, your communication has to happen through secure channels.
Take a look at the model that will let you understand layers of protection for the closing transactions.

Best practice 21: Follow bar association requirements
State bars across the country are intensifying their focus on wire fraud prevention.
And they have good reasons.
The threats are evolving beyond simple email account compromises to sophisticated identity theft.
What does this mean for your practice?
Your verification process must be thorough and well-documented from the moment you open a file until the final disbursement.
Take a real scenario: An Alabama LLC owned by a Utah LLC wants to buy a vacant lot in your county. The property purchase came from an unsolicited offer, and they're not coming to closing. Red flags like these require extra verification steps.
Modern identity verification makes this process simple:
- Send a verification request via text or email
- Remote parties scan their government-issued ID and take a selfie
- Get instant validation status
Your documentation should show you verified the complex ownership structure, validated identities, and payment instructions, and maintained a clear audit trail.
Remember: Your state bar's requirements are ultimately to protect your reputation and customers’ money.
Best practice 22: Secure matter transactions and partner oversight
Think of it as a risk-based security system, like having different levels of security clearance.
Not every transaction needs top-level security, but you need clear rules about who can approve what.
For example, earnest money deposits might need only basic verification, while large closing funds demand enhanced security measures and partner review.
Create clear authorization matrices defining who can approve different transaction types and amounts.
Another example, especially when setting priorities:
Local family home sale ($300,000)
- Sellers are long-time residents
- Buyers are local with a conventional loan
- In-person closing planned → Standard verification process, staff can handle
Commercial building purchase ($2.5M)
- Buyer is a foreign investment group
- Multiple LLCs involved
- Remote closing requested → Requires partner oversight, enhanced security
For example, your office and your paralegal team are handling a $2.5M commercial deal.
Your system automatically flags it for high-risk protocol, requiring:
- Partner review and approval
- Identity verification of all parties before opening the file
- Documented ownership structure validation
- Secure wire instruction collection
- Two-person approval for final wire transfer
The goal is to have clear, automated protocols that scale up security based on risk factors.
Here’s how you could approach the authorization levels:

3 real-world wire fraud examples and practical prevention measures
"Nothing about this one seemed out of the ordinary," says Mike Musto, who lost $600,000 to fraudsters who changed just one letter in his closing team's email addresses.
Though Mike recovered his funds after weeks of working with banks and law enforcement, many victims aren't so fortunate.
Let's examine the most common wire fraud scams to help you stay vigilant and protect your business.
- Business email compromise (BEC) fraud
BEC is a targeted phishing attack (part of social engineering scams) where criminals impersonate trusted parties.
These emails often make wire transfer requests or use realistic language to avoid detection. Unlike mass phishing, BEC is tailored for the receiving party.
And this poses a big threat to firms handling sensitive financial transactions. Because as a professional, you’re often liable for the fraudulent transfer if your account is compromised.
In 2024, a Connecticut homebuyer, Richard Bates, lost $597,000 after receiving a fraudulent email with fake wire instructions.
The hackers had accessed sensitive transaction details by breaching the law firm's emails involved in the transaction.
Bates, believing the email to be legitimate, wired the funds, of which only $129,000 was recovered.

- Seller impersonation scam
Seller impersonation is a scam where fraudsters impersonate the owner of a vacant or rarely monitored property to sell it fraudulently and steal the proceeds.
Using forged documents and fake identities, they list the property below market value for quick sales, often insisting on remote closings to evade detection.
Watch as Tom Cronkright, our executive chairman of CertifID, explains the ins and outs of seller impersonation fraud.
In Raleigh, North Carolina, dentist Craig Adams discovered that his multimillion-dollar mansion's deed had been fraudulently transferred.
The scammer listed the property for sale without his consent, disappearing with the proceeds before the fraud was detected.

- Mortgage payoff fraud
A growing scam where fraudsters impersonate mortgage lenders to divert payoff funds during real estate transactions.
Using phishing or hacking, they intercept and alter payoff instructions, pressuring title companies and/or law practices with urgent requests.
According to our 2024 State of Wire Fraud report, this accounted for 47% of all real estate wire fraud losses in 2022.
In 2024, Donna Morgan was charged in a Southbury, Connecticut, mortgage payoff scam that defrauded over $350,000. Morgan sent falsified payoff letters to a real estate attorney, altering the payee information to divert funds into her account.
The fraud was uncovered after the seller reported that their mortgage remained unpaid, leading to her arrest.

Now that you're familiar with the common types of wire fraud scams, let's explore how to prevent them and protect your business.
How to prevent wire fraud: Implement these best practices and stay fraud-free
With these strategies, your organization will be protected from wire fraud, which will benefit you and safeguard your customers' personal data.
While title companies and attorneys have specific best practices, there's one prevention tip that applies to both: consistent team training.
Regular training sessions should focus on:
- Identifying transaction-specific red flags
- Practicing multi-party coordination
- Testing phishing awareness
Document all procedures so team members have a clear reference when questions arise.
To add an extra layer of security to your title production software and verify high-risk transactions, request a CertifID demo.

Co-founder & Executive Chairman
Tom Cronkright is the Executive Chairman of CertifID, a technology platform designed to safeguard electronic payments from fraud. He co-founded the company in response to a wire fraud he experienced and the rising instances of real estate wire fraud. He also serves as the CEO of Sun Title, a leading title agency in Michigan. Tom is a licensed attorney, real estate broker, title insurance producer and nationally recognized expert on cybersecurity and wire fraud.
Sign up for The Wire to join the conversation.




.png)



