CEO fraud phishing: protecting your executive identity
Fraudsters impersonate executives to steal millions from title and law firms. Here's how to recognize CEO fraud attacks and build defenses that hold.
Tyler Adams
11 minutes
Scams
Nov 12, 2025
Dec 5, 2025
Business email compromise cost victims $2.77 billion in 2024 across 21,442 reported incidents, making it the second most costly cybercrime after investment fraud, according to the FBI IC3 report. Criminals target executives whose authority moves money.
As a title or law firm CEO, your name is the weapon. Fraudsters impersonate you via email, sending urgent wire requests to your team. Your closer sees your name, your signature, and a real file number. They process the transfer. By the time anyone questions it, hundreds of thousands in client funds are gone and you're facing liability and client lawsuits.
Understanding how CEO fraud phishing works is your first defense. Learn how fraudsters use attack schemes against title companies and law firms and how to protect your business against these.
What is CEO fraud phishing?
CEO fraud phishing is a targeted cyberattack where criminals impersonate C-suite executives to trick employees into authorizing fraudulent transactions, disclosing sensitive data, or bypassing security protocols.
These attacks work through fake emails appearing to come from executive accounts with urgent requests that exploit organizational authority and trust.
Unlike generic phishing emails sent to thousands of targets, CEO phishing emails are personalized attacks timed specifically for your firm. Fraudsters study your operations for weeks before striking.
CEO fraud is a subset of business email compromise (BEC) and includes several tactics:
- Whaling attacks target high-value executives
- Spear phishing uses highly personalized emails with specific recipient details
- Domain spoofing creates fake domains nearly identical to legitimate ones—certif1d.com instead of certifid.com.
This works because employees are trained to act quickly on executive directives, especially during high-pressure situations. When your CEO emails requesting an urgent wire transfer, your team's instinct is to execute, not question.
The 7 most common CEO fraud tactics
Let's examine the specific technical methods fraudsters use to impersonate executives and how each plays out in title and law firm scenarios.
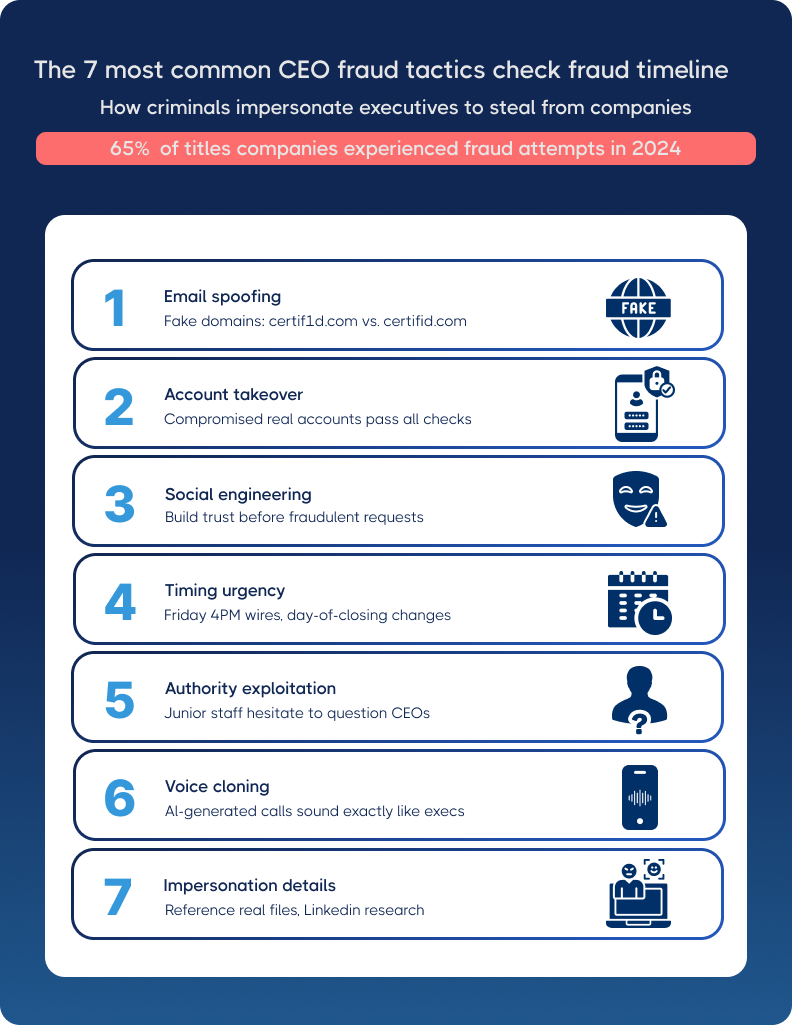
1. Email spoofing and domain variations
Criminals register domains with slight variations—certif1d.com instead of certifid.com, or lawfirm-partners.com instead of lawfirmpartners.com.
This is often combined with display name deception, where "John Smith, CEO" appears in your inbox, but the actual address is random@gmail.com.
2. Account takeover
Attackers compromise actual executive email accounts through phishing or credential theft. Fraudulent requests come from legitimate addresses, pass authentication checks, and appear in previous conversation threads.
This is the most dangerous variant because your team has no technical way to distinguish real from fraudulent. The email is real—only the person behind it has changed.
3. Social engineering and rapport building
Social engineering is about fraudsters sending initial "innocent" emails asking about office schedules or upcoming closings to establish trust.
Days later, they make fraudulent requests. They follow up with phone calls using caller ID spoofing to add pressure. This gradual approach builds credibility—by the time the fraudulent request arrives, your team already recognizes the sender.
4. Creating urgency through timing
Friday 4 PM wire requests. Day-of-closing account changes. Phrases like "client is threatening to walk" or "lender deadline in 2 hours" override verification instincts. Time pressure forces rushed decisions when careful verification is needed.
5. Authority exploitation
Scams rely on hierarchical pressure. Junior staff hesitate to question CEO directives, especially when paired with confidentiality demands: "This acquisition is confidential—don't discuss with anyone."
The solution: creating clear protocols where verification is standard practice, not insubordination.
When your firm establishes that all wire instruction changes require verification through a secure system, regardless of who requests them, employees can follow security procedures without feeling they're questioning authority.
6. Voice cloning technology
AI-generated phone calls now sound exactly like your CEO. Watch this video on AI audio spoofing as Tom Cronkright, Co-founder of CertifID, explains how easily a voice memo can be manipulated for nefarious purposes. The technology has eliminated voice recognition as a reliable verification method.
Instead of time-consuming callback verification for every payoff, use secure verification platforms with direct connections to lender databases.
7. Executive impersonation details
Fraudsters study LinkedIn, company announcements, and public records to copy writing styles. They reference real file numbers, property addresses, and current transactions to appear legitimate.
These impersonation tactics parallel those used in seller impersonation fraud. The authentic details eliminate the obvious red flags your team is trained to spot.
How CEO fraud attacks work in detail: the four-phase operation
CEO fraud follows a deliberate playbook designed to exploit your firm's workflow and authority structure.

Phase 1: Research and reconnaissance
Fraudsters study your firm long before sending emails. Public records reveal property transactions and closing announcements. LinkedIn profiles expose organizational charts and employee roles. Digital signatures on recorded documents leak email addresses. They even identify which title production software you use and your typical wire amounts.
This reconnaissance is thorough. A fraudster discovers your firm closed 47 transactions last month, uses SoftPro, and identifies your closing coordinator, Sarah Martinez, by name from email signatures on recorded documents. Armed with these details, the attack becomes personal.
Phase 2: Access or impersonation
Attackers use three methods of escalating sophistication. Domain spoofing registers near-identical domains like yourfirm-partners.com instead of yourfirmpartners.com. Display name deception shows the CEO's name in your inbox but sends from a random Gmail address. The most dangerous variant is account takeover, where the CEO's actual email gets compromised through phishing.
Why is account takeover deadliest? Fraudulent requests come from legitimate addresses, pass all authentication checks, and appear in previous conversation threads. Your team has no technical reason to doubt the email's authenticity.
Phase 3: Timing and psychological manipulation
Attackers engineer the perfect storm by exploiting multiple pressure points simultaneously. Day-of-closing urgency meets Friday afternoon wire deadlines. Threats about clients walking combine with hard lender timelines. Authority demands immediate action while confidentiality prevents verification.
Here's what this looks like in practice: An email arrives at 3:47 PM Friday requesting a $485,000 wire by 4:30 PM. "The seller is threatening to walk if we don't close today. Process this immediately and don't call."
Phase 4: Execution
The fraudulent request varies by target. Wire transfer fraud redirects closing funds or payoffs. Payroll diversion changes executive direct deposit details. Invoice fraud updates vendor payment accounts. Data thieves request W-2 information or client lists.
Why does this work? Authentic details from reconnaissance combine with artificial urgency, executive authority, and inconvenient timing. Employees override their verification instincts. The scale is staggering—according to the CertifID's State of Wire Fraud 2025 report, 65% of title companies experienced at least one high-risk transaction identified as suspected fraud.
Who fraudsters target in your firm and why
CEO fraud attacks systematically target roles with access to money or data rather than attacking randomly.
These attacks aren't limited to finance and operations divisions. At CertifID, our marketing team regularly receives CEO fraud attempts like:
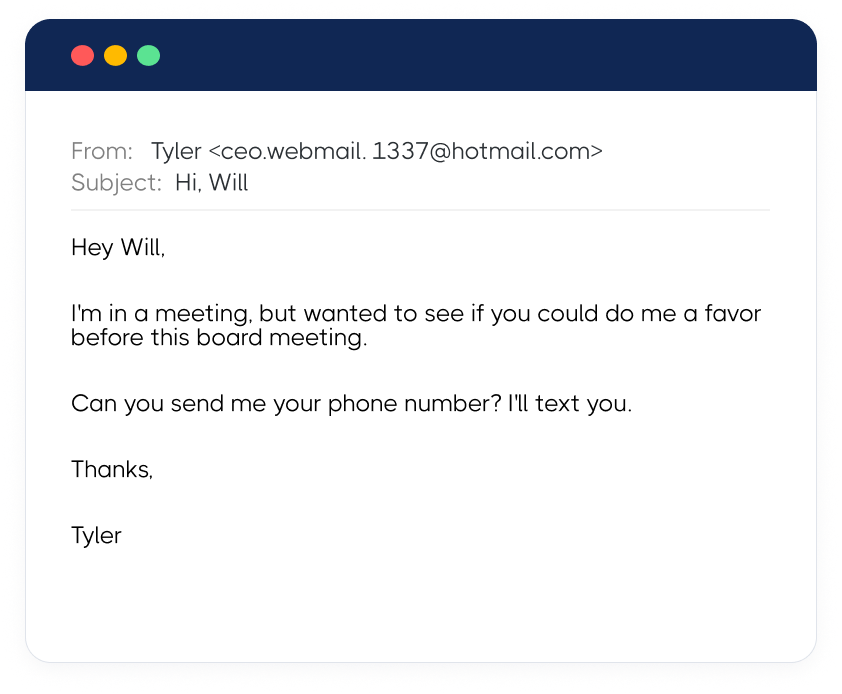
The email address was wrong. There are multiple red flags—but you can see how someone could get caught off guard, especially when fraudsters change the display name to your CEO’s name so it appears correct at first glance.
Warning signs: how to recognize CEO fraud attempts
Email sender anomalies
Domain misspellings like certifiid.com instead of certifid.com. Display names that match the CEO but actual addresses that are external. Emails are sent from personal Gmail accounts while the CEO always uses the company email. Hover over sender names to reveal actual email addresses.
Content and language red flags
Unusual grammar or vocabulary. Generic greetings when the CEO always uses names. Excessive urgency without prior context. Requests to bypass normal protocols. Secrecy demands. At the same time, fraudsters increasingly use AI to improve email quality, making this less reliable.
Transaction warning signs
Wire instructions that differ from those in your title production system. Last-minute updated account details. New vendors without standard onboarding. Payoff instructions via email instead of verified lender portals.
Timing and context red flags
Requests arriving when the CEO is known to be unavailable. Day-of-closing urgency for issues never flagged before. Friday 4 PM wires when verification staff are leaving.
The gut check rule
If something feels wrong even without being able to explain why, pause and verify. Legitimate urgency can wait 5 minutes for confirmation.
Real example
Email received Tuesday 4:15 PM: "Sarah—need you to wire $340,000 for the Martinez closing to updated account below. Seller's attorney just notified us their bank changed. File #2024-1847. Must close by 5 PM today, or we lose the deal. I'm in meetings—process immediately. –John"
Red flags: (1) Request bypasses standard verification, (2) Last-minute account change never mentioned in prior communications, (3) Artificial urgency for routine closing, (4) Sender address is john.smith@yourfirm-llc.com instead of yourfirmllc.com.
How to protect your firm: building fraud-resistant operations
Effective defense against CEO fraud requires five integrated layers that work together. Each layer addresses a different vulnerability fraudsters exploit.
Layer 1: Executive email security
Your CEO's email account is fraudsters' primary target. Mandate multi-factor authentication on all executive accounts.
Implement email authentication protocols (DMARC, SPF, and DKIM) to prevent domain spoofing. Register common misspellings of your firm name before fraudsters do. Limit who can see executive calendars, since attackers time their strikes when CEOs are traveling or having busy periods.
Layer 2: Verification protocols
Any change to wire instructions, whether closing disbursements, payoff accounts, or vendor payments, must be verified through a secure closing wire verification system before processing.
Policy example: "Any update to previously established banking details requires verification through the CertifID platform. No exceptions, regardless of urgency or who requests the change. This includes requests that appear to come from executives, lenders, or long-time vendors."
Layer 3: Technology controls
Deploy these technical safeguards:
- Implement advanced email filtering that flags CEO impersonation attempts beyond basic spam detection
- Enable automatic external email banners warning staff when messages originate outside your domain
- Configure fraud monitoring settings within your title production software to flag instruction changes
- Implement banking portal controls requiring separate credentials for initiating versus approving wires
- Adopt secure verification platforms that authenticate party identities and enable account-to-account transfers, eliminating traditional wire fraud risk entirely
Layer 4: Team training and culture
Conduct quarterly fraud scenario training using real examples from your market. Run simulated phishing tests to identify who needs additional coaching. Explicitly tell staff they're expected to verify any suspicious request regardless of who sent it.
Celebrate employees who catch fraud attempts in monthly team meetings. Make vigilance part of performance expectations, not questioning authority.
Layer 5: Scaling for high-volume operations
For firms processing 30-50+ closings monthly, standardize protocols across all locations through centralized systems. Automate verification within your existing title production workflow. Make verification the default for every transaction without exception.
Layer 6: Turn security into a competitive advantage
Market your fraud prevention protocols to clients as a closing safeguard. Educate referral partners on your security commitment. Provide executives with fraud monitoring dashboards. Lead by example when executives follow verification protocols in team communications.
Layer 7: Continuous improvement
Conduct monthly transaction audits to identify gaps. Analyze fraud attempt patterns when suspicious emails arrive. Track metrics, including suspicious emails reported and verification compliance rates.
The reality check: You will be targeted. The question isn't whether fraudsters will try—it's whether your defenses will hold when they do.
If a CEO fraud attack succeeds: immediate response protocol

First hour after CEO fraud
Halt all outgoing wires across all offices immediately. Contact the bank to freeze or recall the fraudulent transfer. Success depends on speed since most transfers complete within 24 hours. Preserve evidence by forwarding emails with full headers and documenting the timeline.
First 24 hours after CEO fraud
File an FBI IC3 report at ic3.gov. Notify the underwriter and E&O insurance carrier. Inform affected clients transparently. Begin investigation to determine if email accounts were breached. Learn from successful recovery cases to understand what works.
First week after CEO fraud
Implement immediate protocol changes. Communicate security improvements to referral partners. Review all pending transactions. The FBI's Recovery Asset Team had 66% success freezing BEC funds in 2024, but only when victims reported immediately. Hours matter.
CEO fraud: Your executive identity is critical infrastructure
Your authority enables high-volume operations. It also represents the single point of failure fraudsters can exploit.
The criminals aren't stopping. They're studying your firm right now, waiting for the perfect moment to impersonate you. The firms winning in 2025 have built layered defenses that protect their reputation and their clients.
Your executive identity is your firm's most valuable asset and its greatest vulnerability. Request a demo to see how CertifID stops CEO fraud.

FAQ
How is CEO fraud different from regular phishing?
Regular phishing casts a wide net with generic scams. CEO fraud is targeted, researched, and personalized—fraudsters study your firm specifically and impersonate your executives to exploit authority and trust. They reference real transactions, use authentic communication patterns, and time attacks for maximum success.
Can small title companies be targeted?
Yes, absolutely. Fraudsters target firms of all sizes. Smaller firms processing 20-30 closings monthly may lack dedicated security staff, making them easier targets despite lower transaction volumes. The public nature of real estate transactions means criminals can identify targets regardless of firm size.
What if the email really is from my CEO's account?
Account takeover is the most dangerous variant. If the legitimate account is compromised, verify all financial requests via phone at a known number, even if the email address appears correct. Never use contact information provided in the suspicious email. Check with IT to scan for inbox rules, forwarding settings, or other signs of compromise.
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Business email compromise cost victims $2.77 billion in 2024 across 21,442 reported incidents, making it the second most costly cybercrime after investment fraud, according to the FBI IC3 report. Criminals target executives whose authority moves money.
As a title or law firm CEO, your name is the weapon. Fraudsters impersonate you via email, sending urgent wire requests to your team. Your closer sees your name, your signature, and a real file number. They process the transfer. By the time anyone questions it, hundreds of thousands in client funds are gone and you're facing liability and client lawsuits.
Understanding how CEO fraud phishing works is your first defense. Learn how fraudsters use attack schemes against title companies and law firms and how to protect your business against these.
What is CEO fraud phishing?
CEO fraud phishing is a targeted cyberattack where criminals impersonate C-suite executives to trick employees into authorizing fraudulent transactions, disclosing sensitive data, or bypassing security protocols.
These attacks work through fake emails appearing to come from executive accounts with urgent requests that exploit organizational authority and trust.
Unlike generic phishing emails sent to thousands of targets, CEO phishing emails are personalized attacks timed specifically for your firm. Fraudsters study your operations for weeks before striking.
CEO fraud is a subset of business email compromise (BEC) and includes several tactics:
- Whaling attacks target high-value executives
- Spear phishing uses highly personalized emails with specific recipient details
- Domain spoofing creates fake domains nearly identical to legitimate ones—certif1d.com instead of certifid.com.
This works because employees are trained to act quickly on executive directives, especially during high-pressure situations. When your CEO emails requesting an urgent wire transfer, your team's instinct is to execute, not question.
The 7 most common CEO fraud tactics
Let's examine the specific technical methods fraudsters use to impersonate executives and how each plays out in title and law firm scenarios.

1. Email spoofing and domain variations
Criminals register domains with slight variations—certif1d.com instead of certifid.com, or lawfirm-partners.com instead of lawfirmpartners.com.
This is often combined with display name deception, where "John Smith, CEO" appears in your inbox, but the actual address is random@gmail.com.
2. Account takeover
Attackers compromise actual executive email accounts through phishing or credential theft. Fraudulent requests come from legitimate addresses, pass authentication checks, and appear in previous conversation threads.
This is the most dangerous variant because your team has no technical way to distinguish real from fraudulent. The email is real—only the person behind it has changed.
3. Social engineering and rapport building
Social engineering is about fraudsters sending initial "innocent" emails asking about office schedules or upcoming closings to establish trust.
Days later, they make fraudulent requests. They follow up with phone calls using caller ID spoofing to add pressure. This gradual approach builds credibility—by the time the fraudulent request arrives, your team already recognizes the sender.
4. Creating urgency through timing
Friday 4 PM wire requests. Day-of-closing account changes. Phrases like "client is threatening to walk" or "lender deadline in 2 hours" override verification instincts. Time pressure forces rushed decisions when careful verification is needed.
5. Authority exploitation
Scams rely on hierarchical pressure. Junior staff hesitate to question CEO directives, especially when paired with confidentiality demands: "This acquisition is confidential—don't discuss with anyone."
The solution: creating clear protocols where verification is standard practice, not insubordination.
When your firm establishes that all wire instruction changes require verification through a secure system, regardless of who requests them, employees can follow security procedures without feeling they're questioning authority.
6. Voice cloning technology
AI-generated phone calls now sound exactly like your CEO. Watch this video on AI audio spoofing as Tom Cronkright, Co-founder of CertifID, explains how easily a voice memo can be manipulated for nefarious purposes. The technology has eliminated voice recognition as a reliable verification method.
Instead of time-consuming callback verification for every payoff, use secure verification platforms with direct connections to lender databases.
7. Executive impersonation details
Fraudsters study LinkedIn, company announcements, and public records to copy writing styles. They reference real file numbers, property addresses, and current transactions to appear legitimate.
These impersonation tactics parallel those used in seller impersonation fraud. The authentic details eliminate the obvious red flags your team is trained to spot.
How CEO fraud attacks work in detail: the four-phase operation
CEO fraud follows a deliberate playbook designed to exploit your firm's workflow and authority structure.

Phase 1: Research and reconnaissance
Fraudsters study your firm long before sending emails. Public records reveal property transactions and closing announcements. LinkedIn profiles expose organizational charts and employee roles. Digital signatures on recorded documents leak email addresses. They even identify which title production software you use and your typical wire amounts.
This reconnaissance is thorough. A fraudster discovers your firm closed 47 transactions last month, uses SoftPro, and identifies your closing coordinator, Sarah Martinez, by name from email signatures on recorded documents. Armed with these details, the attack becomes personal.
Phase 2: Access or impersonation
Attackers use three methods of escalating sophistication. Domain spoofing registers near-identical domains like yourfirm-partners.com instead of yourfirmpartners.com. Display name deception shows the CEO's name in your inbox but sends from a random Gmail address. The most dangerous variant is account takeover, where the CEO's actual email gets compromised through phishing.
Why is account takeover deadliest? Fraudulent requests come from legitimate addresses, pass all authentication checks, and appear in previous conversation threads. Your team has no technical reason to doubt the email's authenticity.
Phase 3: Timing and psychological manipulation
Attackers engineer the perfect storm by exploiting multiple pressure points simultaneously. Day-of-closing urgency meets Friday afternoon wire deadlines. Threats about clients walking combine with hard lender timelines. Authority demands immediate action while confidentiality prevents verification.
Here's what this looks like in practice: An email arrives at 3:47 PM Friday requesting a $485,000 wire by 4:30 PM. "The seller is threatening to walk if we don't close today. Process this immediately and don't call."
Phase 4: Execution
The fraudulent request varies by target. Wire transfer fraud redirects closing funds or payoffs. Payroll diversion changes executive direct deposit details. Invoice fraud updates vendor payment accounts. Data thieves request W-2 information or client lists.
Why does this work? Authentic details from reconnaissance combine with artificial urgency, executive authority, and inconvenient timing. Employees override their verification instincts. The scale is staggering—according to the CertifID's State of Wire Fraud 2025 report, 65% of title companies experienced at least one high-risk transaction identified as suspected fraud.
Who fraudsters target in your firm and why
CEO fraud attacks systematically target roles with access to money or data rather than attacking randomly.
These attacks aren't limited to finance and operations divisions. At CertifID, our marketing team regularly receives CEO fraud attempts like:

The email address was wrong. There are multiple red flags—but you can see how someone could get caught off guard, especially when fraudsters change the display name to your CEO’s name so it appears correct at first glance.
Warning signs: how to recognize CEO fraud attempts
Email sender anomalies
Domain misspellings like certifiid.com instead of certifid.com. Display names that match the CEO but actual addresses that are external. Emails are sent from personal Gmail accounts while the CEO always uses the company email. Hover over sender names to reveal actual email addresses.
Content and language red flags
Unusual grammar or vocabulary. Generic greetings when the CEO always uses names. Excessive urgency without prior context. Requests to bypass normal protocols. Secrecy demands. At the same time, fraudsters increasingly use AI to improve email quality, making this less reliable.
Transaction warning signs
Wire instructions that differ from those in your title production system. Last-minute updated account details. New vendors without standard onboarding. Payoff instructions via email instead of verified lender portals.
Timing and context red flags
Requests arriving when the CEO is known to be unavailable. Day-of-closing urgency for issues never flagged before. Friday 4 PM wires when verification staff are leaving.
The gut check rule
If something feels wrong even without being able to explain why, pause and verify. Legitimate urgency can wait 5 minutes for confirmation.
Real example
Email received Tuesday 4:15 PM: "Sarah—need you to wire $340,000 for the Martinez closing to updated account below. Seller's attorney just notified us their bank changed. File #2024-1847. Must close by 5 PM today, or we lose the deal. I'm in meetings—process immediately. –John"
Red flags: (1) Request bypasses standard verification, (2) Last-minute account change never mentioned in prior communications, (3) Artificial urgency for routine closing, (4) Sender address is john.smith@yourfirm-llc.com instead of yourfirmllc.com.
How to protect your firm: building fraud-resistant operations
Effective defense against CEO fraud requires five integrated layers that work together. Each layer addresses a different vulnerability fraudsters exploit.
Layer 1: Executive email security
Your CEO's email account is fraudsters' primary target. Mandate multi-factor authentication on all executive accounts.
Implement email authentication protocols (DMARC, SPF, and DKIM) to prevent domain spoofing. Register common misspellings of your firm name before fraudsters do. Limit who can see executive calendars, since attackers time their strikes when CEOs are traveling or having busy periods.
Layer 2: Verification protocols
Any change to wire instructions, whether closing disbursements, payoff accounts, or vendor payments, must be verified through a secure closing wire verification system before processing.
Policy example: "Any update to previously established banking details requires verification through the CertifID platform. No exceptions, regardless of urgency or who requests the change. This includes requests that appear to come from executives, lenders, or long-time vendors."
Layer 3: Technology controls
Deploy these technical safeguards:
- Implement advanced email filtering that flags CEO impersonation attempts beyond basic spam detection
- Enable automatic external email banners warning staff when messages originate outside your domain
- Configure fraud monitoring settings within your title production software to flag instruction changes
- Implement banking portal controls requiring separate credentials for initiating versus approving wires
- Adopt secure verification platforms that authenticate party identities and enable account-to-account transfers, eliminating traditional wire fraud risk entirely
Layer 4: Team training and culture
Conduct quarterly fraud scenario training using real examples from your market. Run simulated phishing tests to identify who needs additional coaching. Explicitly tell staff they're expected to verify any suspicious request regardless of who sent it.
Celebrate employees who catch fraud attempts in monthly team meetings. Make vigilance part of performance expectations, not questioning authority.
Layer 5: Scaling for high-volume operations
For firms processing 30-50+ closings monthly, standardize protocols across all locations through centralized systems. Automate verification within your existing title production workflow. Make verification the default for every transaction without exception.
Layer 6: Turn security into a competitive advantage
Market your fraud prevention protocols to clients as a closing safeguard. Educate referral partners on your security commitment. Provide executives with fraud monitoring dashboards. Lead by example when executives follow verification protocols in team communications.
Layer 7: Continuous improvement
Conduct monthly transaction audits to identify gaps. Analyze fraud attempt patterns when suspicious emails arrive. Track metrics, including suspicious emails reported and verification compliance rates.
The reality check: You will be targeted. The question isn't whether fraudsters will try—it's whether your defenses will hold when they do.
If a CEO fraud attack succeeds: immediate response protocol

First hour after CEO fraud
Halt all outgoing wires across all offices immediately. Contact the bank to freeze or recall the fraudulent transfer. Success depends on speed since most transfers complete within 24 hours. Preserve evidence by forwarding emails with full headers and documenting the timeline.
First 24 hours after CEO fraud
File an FBI IC3 report at ic3.gov. Notify the underwriter and E&O insurance carrier. Inform affected clients transparently. Begin investigation to determine if email accounts were breached. Learn from successful recovery cases to understand what works.
First week after CEO fraud
Implement immediate protocol changes. Communicate security improvements to referral partners. Review all pending transactions. The FBI's Recovery Asset Team had 66% success freezing BEC funds in 2024, but only when victims reported immediately. Hours matter.
CEO fraud: Your executive identity is critical infrastructure
Your authority enables high-volume operations. It also represents the single point of failure fraudsters can exploit.
The criminals aren't stopping. They're studying your firm right now, waiting for the perfect moment to impersonate you. The firms winning in 2025 have built layered defenses that protect their reputation and their clients.
Your executive identity is your firm's most valuable asset and its greatest vulnerability. Request a demo to see how CertifID stops CEO fraud.

Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Sign up for The Wire to join the conversation.





.png)



