Customer identity verification: How to do it right in business transactions
Whether you’re closing a legal deal, managing a property transaction, or transferring large sums between accounts, verifying who you’re doing business with is critical.

Luis Palomares
5 minutes
Fraud Prevention
Jul 23, 2024
Jul 8, 2025
High-value transactions demand more than a driver’s license and a phone call. Whether you’re closing a legal deal, managing a property transaction, or transferring large sums between accounts, verifying who you’re doing business with is critical.
But many businesses still rely on outdated ID checks or gut instinct.
These methods might feel familiar, but they leave dangerous gaps—especially as fraudsters become more sophisticated with AI-powered impersonation and document forgery.
Organizations across industries are rethinking their approach to customer identity verification. And in high-stakes sectors like real estate and law, the risks of getting it wrong are particularly high.
What is customer identity verification?
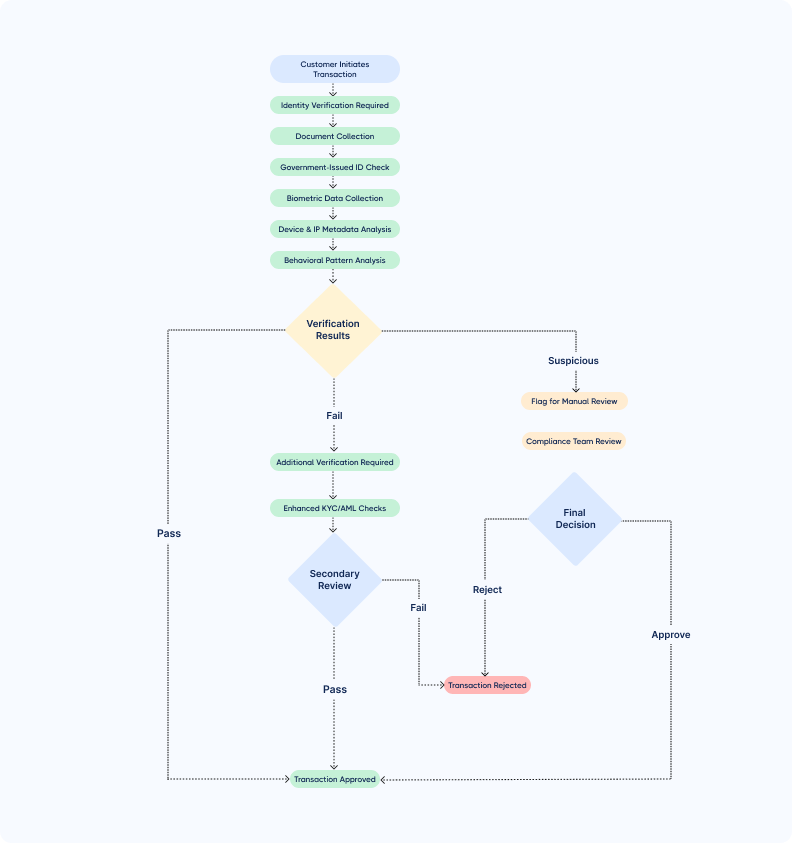
Customer identity verification is the process of confirming a customer’s identity to prevent fraud, ensure compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations, and protect financial transactions. It’s critical in business transactions, especially those involving wire transfers or legal documentation.
Verification typically includes checking government-issued IDs, collecting biometric data, capturing device and IP metadata, and scanning behavioral signals for anomalies.
Here’s an example of how customer identity verification could look like in a workflow.
Why identity verification is business-critical in 2025
According to Federal Trade Commission (FTC) statistics from 2025, Americans lost a record $12.5 billion to fraud in 2024, up 25% from the previous year.
This dramatic surge shows fraud is accelerating at an unprecedented pace, making identity verification more crucial than ever for businesses.
Fraudsters are getting increasingly creative with their methods.
Take the Hong Kong employee who fell victim to a $25 million deepfake scam in 2023, where fraudsters used AI to create fake video calls with what appeared to be the company's CFO and other staff members.
Deepfake-enabled fraud and identity theft have already caused more than $200 million in losses in 2025, demonstrating how quickly criminals adapt to new technologies.
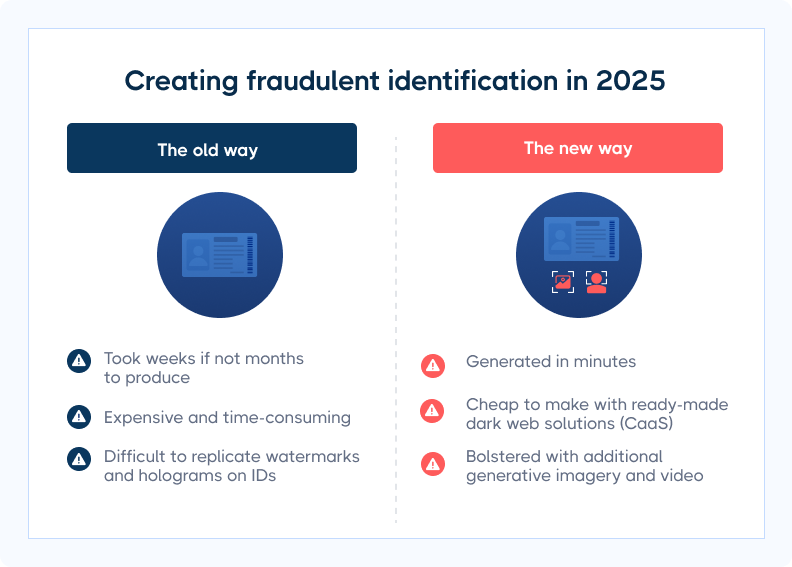
These days, it’s a matter of minutes (not hours or days) to create fraudulent identities and trick customers. That’s why businesses must put systems in place to protect all transactions.
How safe is ID verification?
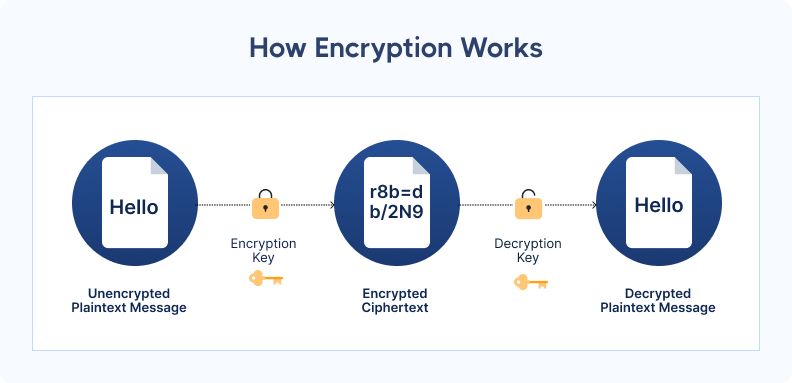
Most ID verification software uses encryption algorithms to protect your clients’ sensitive data.
When implemented effectively, these algorithms safeguard customer information from the time it’s uploaded to when it’s deleted.
Encryption works as a lock and key; only an authorized party who holds the key can access the data. If information is intercepted by fraudsters, it’s incomprehensible and unusable.
Breaking the key is nearly impossible due to the large amount of time and processing power needed.
Another layer of safety comes from ID verification providers being required to comply with regulatory standards. These standards aim to secure personal data and prevent fraud.
Mandatory compliance makes sure software providers meet baseline safeguards for data and identity protection.
How identity verification protects your transaction—and your business
Not every business handles identity verification the same way.
Some run a quick ID check. Others embed verification into the core of their workflow. Ultimately, the difference is cultural.
If you want to protect your clients, close deals securely, and reduce liability exposure, you can’t treat ID verification as a checkbox. You need to think of it as a layered defense system—one that keeps fraud out and builds trust.
Here’s why customer identity verification is key for your business:
- Prevents impersonation and fraud attempts: By verifying clients upfront—before money is requested or released—you stop impersonation scams at the door. This is especially critical in high-risk closings involving remote parties, LLCs, or vacant land.
- Reduces liability in high-value transactions: If fraud occurs and your firm didn’t follow proper ID protocols, you could be on the hook. Digital verification tools create a verifiable audit trail, helping you demonstrate due diligence and protect your business from legal action.
- Safeguards your clients’ sensitive information: Modern tools encrypt data in transit and at rest. With such tools, information is stored temporarily and automatically deleted, reducing your exposure to data privacy risks and keeping clients reassured.
- Strengthens your reputation with clients and partners: Secure verification sends a clear signal: you take your client’s protection seriously. This builds trust with clients, partners, and any third parties who may need to validate your processes.
- Speeds up your workflow and reduces friction: No more chasing callbacks or manually inspecting IDs. Automated verification reduces delays and speeds up processes—especially helpful when working with busy clients or coordinating with out-of-state parties.
The most effective types of identity verification
Fraudsters don’t just rely on one tactic—and neither should you.
No single identity check can catch every threat. That’s why the most effective verification systems layer methods like document checks, biometrics, and device data to detect fraud faster—before any money moves.
For example, even if a fake ID passes visual inspection, facial recognition or device tracking might flag the user as high-risk—before any money moves.
Here are the core identity verification methods you should consider:
- Document verification: Scans and authenticates both sides of a government-issued ID. Helps confirm identity and detect tampering, forgeries, or expired documents—especially important when dealing with remote sellers or high-dollar closings.
- Biometric verification: Uses facial recognition to match the person in the selfie with the person on the ID. Liveness detection prevents bad actors from using printed photos, masks, or stolen images.
- Device and location authentication: Looks beyond the user to assess the context of each session—IP address, geolocation, device fingerprint, and known fraud markers like burner phones or anonymized browsers. This stops fraud attempts that mimic real people.
- Knowledge-based authentication (KBA): Asks personal history questions (like past addresses or mortgage lenders). It’s not foolproof on its own, but it adds an extra layer when other methods aren’t enough.
- Multi-factor authentication (MFA): Combines something the client knows (like a code sent to their phone) with something they are (like biometrics) or have (a trusted device). This extra step can block unauthorized access—even if someone compromises an email or phone number.
Industry spotlight: Customer identity verification in real estate and law
In legal transactions and real estate, identity verification ensures that:
- Sellers are authorized to transfer property titles and receive funds.
- Buyers are legitimate and sending verified funds, including earnest money and closing balances.
- Other parties (e.g., attorneys, agents, notaries) are who they claim to be and authorized to act in the transaction.
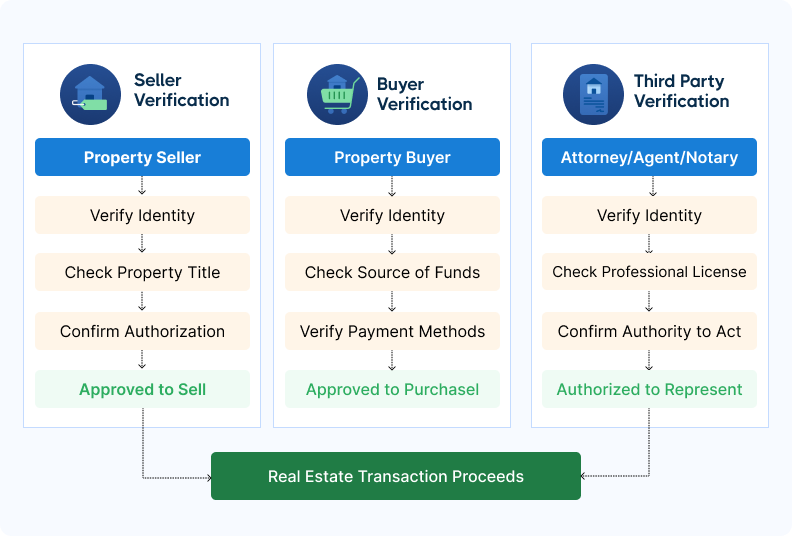
Customer identity check workflow: How CertifID Match protects every party
Fraud prevention isn’t just the title company’s job anymore.
In real estate closings, multiple parties—from real estate agents (REAs) to closing attorneys—touch the transaction before any money moves. CertifID Match turns identity verification into a shared, secure checkpoint.
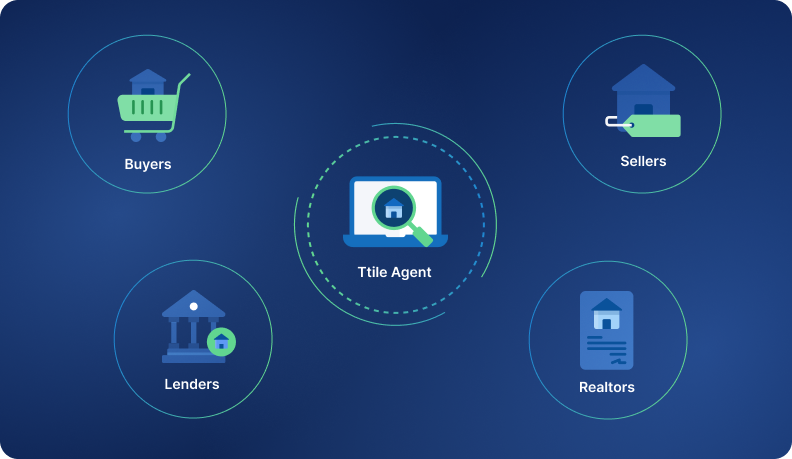
It’s built to work across your ecosystem—but keeps title and escrow teams in control of results, records, and risk decisions. Here’s how it works.
Step 1: The real estate agent (REAs) spots early warning signs
Real estate agents are typically the first to engage with buyers or sellers. When something feels off—like vague ownership history, urgency to close, or remote communication—REAs can alert the title team early in the process.
In these cases, the title team can generate a CertifID Match link and send it to the seller via the real estate agent, allowing for secure identity verification before the purchase agreement is signed.
Step 2: The title team initiates formal verification
Once the deal is in motion, the title or escrow team formally initiates the ID verification process using CertifID Match. The client’s name, email, or phone number is entered into the platform, and a secure, branded link is sent directly to the client.
This keeps the title team in control of the process and the recordkeeping.
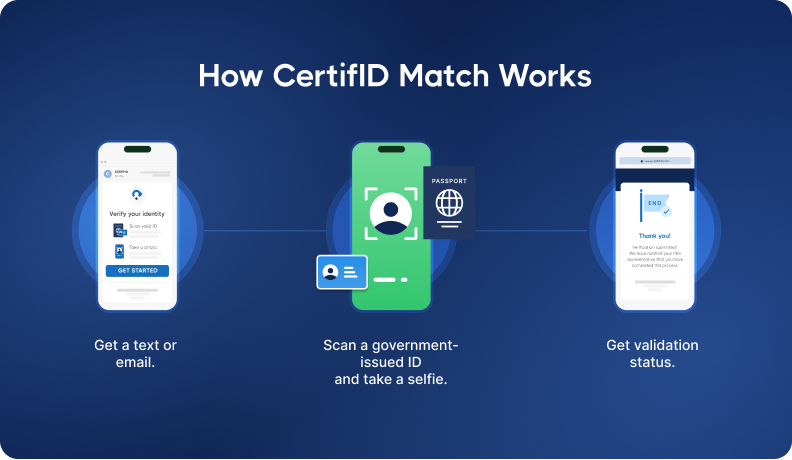
Step 3: The client completes the mobile-friendly flow
The client receives the verification request and completes the steps using their phone:
- Upload the front and back of a government-issued ID
- Take a real-time selfie for biometric validation
- Allow device and IP-level analysis
There’s no app to download, no password to remember—just a fast, user-friendly experience.
Step 4: CertifID runs real-time fraud analysis
CertifID Match runs multiple checks to assess risk across several dimensions:
- ID authenticity
- Biometric match (selfie vs. ID)
- IP address and geolocation
- Device fingerprinting and history
- Known fraud patterns (e.g., reused scam numbers)
If any indicators suggest potential fraud, the system flags the transaction immediately.
Step 5: The title team receives a verified result—or a red flag
Whether the result is approved or concerning, the title or escrow team receives it in their CertifID dashboard. Each action is timestamped and logged for future reference.
Why this collaborative workflow works:
- Title agent stays in control: Real estate agents help surface suspicious activity earlier, but the title team always owns the decision, the tools, and the audit trail.
- Clients get a seamless experience: Mobile-first verification takes just a few minutes, without additional downloads or account setup.
- Fraud is flagged before it reaches funding: Risk indicators are checked at the point of verification, not after the transaction is already moving.
- The entire process is recorded: Every step is logged and accessible, providing confidence during audits, insurance claims, or legal disputes.
Secure closing solutions for title, legal, and real estate professionals
Whether you’re a title agent reviewing documents, an attorney advising clients, or a real estate agent managing listings, your role is critical.
You help protect some of the most valuable transactions people will ever make. That protection starts with verifying identities early, securely, and without slowing down the deal.
CertifID Match makes that possible. It fits into your workflow, supports collaboration between teams, and delivers results in real time—so you can move forward with confidence.
Ready to secure every closing?

FAQ
Director of Product
Luis brings over a decade of design and product leadership experience to the team. Before joining CertifID, Luis co-founded InHouse, a real estate marketing, and data platform. Today, he combines his passion for thoughtful design and his experience in real estate to help create a future safe from wire fraud.
High-value transactions demand more than a driver’s license and a phone call. Whether you’re closing a legal deal, managing a property transaction, or transferring large sums between accounts, verifying who you’re doing business with is critical.
But many businesses still rely on outdated ID checks or gut instinct.
These methods might feel familiar, but they leave dangerous gaps—especially as fraudsters become more sophisticated with AI-powered impersonation and document forgery.
Organizations across industries are rethinking their approach to customer identity verification. And in high-stakes sectors like real estate and law, the risks of getting it wrong are particularly high.
What is customer identity verification?
Customer identity verification is the process of confirming a customer’s identity to prevent fraud, ensure compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations, and protect financial transactions. It’s critical in business transactions, especially those involving wire transfers or legal documentation.
Verification typically includes checking government-issued IDs, collecting biometric data, capturing device and IP metadata, and scanning behavioral signals for anomalies.
Here’s an example of how customer identity verification could look like in a workflow.

Why identity verification is business-critical in 2025
According to Federal Trade Commission (FTC) statistics from 2025, Americans lost a record $12.5 billion to fraud in 2024, up 25% from the previous year.
This dramatic surge shows fraud is accelerating at an unprecedented pace, making identity verification more crucial than ever for businesses.
Fraudsters are getting increasingly creative with their methods.
Take the Hong Kong employee who fell victim to a $25 million deepfake scam in 2023, where fraudsters used AI to create fake video calls with what appeared to be the company's CFO and other staff members.
Deepfake-enabled fraud and identity theft have already caused more than $200 million in losses in 2025, demonstrating how quickly criminals adapt to new technologies.
These days, it’s a matter of minutes (not hours or days) to create fraudulent identities and trick customers. That’s why businesses must put systems in place to protect all transactions.

How safe is ID verification?
Most ID verification software uses encryption algorithms to protect your clients’ sensitive data.
When implemented effectively, these algorithms safeguard customer information from the time it’s uploaded to when it’s deleted.
Encryption works as a lock and key; only an authorized party who holds the key can access the data. If information is intercepted by fraudsters, it’s incomprehensible and unusable.
Breaking the key is nearly impossible due to the large amount of time and processing power needed.

Another layer of safety comes from ID verification providers being required to comply with regulatory standards. These standards aim to secure personal data and prevent fraud.
Mandatory compliance makes sure software providers meet baseline safeguards for data and identity protection.
How identity verification protects your transaction—and your business
Not every business handles identity verification the same way.
Some run a quick ID check. Others embed verification into the core of their workflow. Ultimately, the difference is cultural.
If you want to protect your clients, close deals securely, and reduce liability exposure, you can’t treat ID verification as a checkbox. You need to think of it as a layered defense system—one that keeps fraud out and builds trust.
Here’s why customer identity verification is key for your business:
- Prevents impersonation and fraud attempts: By verifying clients upfront—before money is requested or released—you stop impersonation scams at the door. This is especially critical in high-risk closings involving remote parties, LLCs, or vacant land.
- Reduces liability in high-value transactions: If fraud occurs and your firm didn’t follow proper ID protocols, you could be on the hook. Digital verification tools create a verifiable audit trail, helping you demonstrate due diligence and protect your business from legal action.
- Safeguards your clients’ sensitive information: Modern tools encrypt data in transit and at rest. With such tools, information is stored temporarily and automatically deleted, reducing your exposure to data privacy risks and keeping clients reassured.
- Strengthens your reputation with clients and partners: Secure verification sends a clear signal: you take your client’s protection seriously. This builds trust with clients, partners, and any third parties who may need to validate your processes.
- Speeds up your workflow and reduces friction: No more chasing callbacks or manually inspecting IDs. Automated verification reduces delays and speeds up processes—especially helpful when working with busy clients or coordinating with out-of-state parties.
The most effective types of identity verification
Fraudsters don’t just rely on one tactic—and neither should you.
No single identity check can catch every threat. That’s why the most effective verification systems layer methods like document checks, biometrics, and device data to detect fraud faster—before any money moves.
For example, even if a fake ID passes visual inspection, facial recognition or device tracking might flag the user as high-risk—before any money moves.
Here are the core identity verification methods you should consider:
- Document verification: Scans and authenticates both sides of a government-issued ID. Helps confirm identity and detect tampering, forgeries, or expired documents—especially important when dealing with remote sellers or high-dollar closings.
- Biometric verification: Uses facial recognition to match the person in the selfie with the person on the ID. Liveness detection prevents bad actors from using printed photos, masks, or stolen images.
- Device and location authentication: Looks beyond the user to assess the context of each session—IP address, geolocation, device fingerprint, and known fraud markers like burner phones or anonymized browsers. This stops fraud attempts that mimic real people.
- Knowledge-based authentication (KBA): Asks personal history questions (like past addresses or mortgage lenders). It’s not foolproof on its own, but it adds an extra layer when other methods aren’t enough.
- Multi-factor authentication (MFA): Combines something the client knows (like a code sent to their phone) with something they are (like biometrics) or have (a trusted device). This extra step can block unauthorized access—even if someone compromises an email or phone number.
Industry spotlight: Customer identity verification in real estate and law
In legal transactions and real estate, identity verification ensures that:
- Sellers are authorized to transfer property titles and receive funds.
- Buyers are legitimate and sending verified funds, including earnest money and closing balances.
- Other parties (e.g., attorneys, agents, notaries) are who they claim to be and authorized to act in the transaction.

Customer identity check workflow: How CertifID Match protects every party
Fraud prevention isn’t just the title company’s job anymore.
In real estate closings, multiple parties—from real estate agents (REAs) to closing attorneys—touch the transaction before any money moves. CertifID Match turns identity verification into a shared, secure checkpoint.

It’s built to work across your ecosystem—but keeps title and escrow teams in control of results, records, and risk decisions. Here’s how it works.
Step 1: The real estate agent (REAs) spots early warning signs
Real estate agents are typically the first to engage with buyers or sellers. When something feels off—like vague ownership history, urgency to close, or remote communication—REAs can alert the title team early in the process.
In these cases, the title team can generate a CertifID Match link and send it to the seller via the real estate agent, allowing for secure identity verification before the purchase agreement is signed.
Step 2: The title team initiates formal verification
Once the deal is in motion, the title or escrow team formally initiates the ID verification process using CertifID Match. The client’s name, email, or phone number is entered into the platform, and a secure, branded link is sent directly to the client.
This keeps the title team in control of the process and the recordkeeping.
Step 3: The client completes the mobile-friendly flow
The client receives the verification request and completes the steps using their phone:
- Upload the front and back of a government-issued ID
- Take a real-time selfie for biometric validation
- Allow device and IP-level analysis
There’s no app to download, no password to remember—just a fast, user-friendly experience.
Step 4: CertifID runs real-time fraud analysis
CertifID Match runs multiple checks to assess risk across several dimensions:
- ID authenticity
- Biometric match (selfie vs. ID)
- IP address and geolocation
- Device fingerprinting and history
- Known fraud patterns (e.g., reused scam numbers)
If any indicators suggest potential fraud, the system flags the transaction immediately.
Step 5: The title team receives a verified result—or a red flag
Whether the result is approved or concerning, the title or escrow team receives it in their CertifID dashboard. Each action is timestamped and logged for future reference.

Why this collaborative workflow works:
- Title agent stays in control: Real estate agents help surface suspicious activity earlier, but the title team always owns the decision, the tools, and the audit trail.
- Clients get a seamless experience: Mobile-first verification takes just a few minutes, without additional downloads or account setup.
- Fraud is flagged before it reaches funding: Risk indicators are checked at the point of verification, not after the transaction is already moving.
- The entire process is recorded: Every step is logged and accessible, providing confidence during audits, insurance claims, or legal disputes.
Secure closing solutions for title, legal, and real estate professionals
Whether you’re a title agent reviewing documents, an attorney advising clients, or a real estate agent managing listings, your role is critical.
You help protect some of the most valuable transactions people will ever make. That protection starts with verifying identities early, securely, and without slowing down the deal.
CertifID Match makes that possible. It fits into your workflow, supports collaboration between teams, and delivers results in real time—so you can move forward with confidence.
Ready to secure every closing?

Director of Product
Luis brings over a decade of design and product leadership experience to the team. Before joining CertifID, Luis co-founded InHouse, a real estate marketing, and data platform. Today, he combines his passion for thoughtful design and his experience in real estate to help create a future safe from wire fraud.
Sign up for The Wire to join the conversation.



.png)
.png)