Best Cybersecurity Solutions for Title Companies: 2025 Complete Guide
Build a security stack that stops wire fraud without slowing operations—read your practical guide to the tools that protect billions in transactions monthly.

Matt Kilmartin
12 minutes
Cybersecurity
Nov 3, 2021
Oct 13, 2025
Title companies have become a prime hunting ground for cybercriminals. And the bigger the business, the bigger the target.
An ALTA survey found that 73% of title companies handling over 250 closings a month saw a spike in attacks, nearly double the rate of smaller firms.
Here's the CEO dilemma: you can't afford to slow down operations, but you can't afford to be the next fraud victim either.
This guide cuts through the complexity to show you practical cybersecurity solutions that balance protection with operational efficiency. We'll cover the best security platforms and practices designed for real estate transactions, plus show you which solution handles which threat.
Why do title companies need specialized cybersecurity?
There are several reasons title companies need to invest in specialized cybersecurity. We divide these into three main categories that make them especially vulnerable targets.
Real estate environment: high-stakes, multi-party transactions

High-value targets make you attractive to fraudsters. With average house prices hitting $510,300, criminals get big gains from successful attacks.
Your complex transaction web means access to multiple parties' financial data in single transactions, creating numerous attack vectors for exploitation.
Time pressure vulnerabilities compound the risk. Tight closing deadlines create pressure to bypass security protocols when "urgent" requests arrive. Extended attack windows during 30-60 day closing processes give fraudsters opportunities for email thread hijacking.
Also, exploiting public information makes targeting easier. Fraudsters use publicly available property records for seller identity theft and deploy communication impersonation through realtor and lender spoofing via domain manipulation.
Business survival: protection against financial loss
Catastrophic loss can cripple your title company.
According to our data, average losses hit $68,413 for buyer fraud, $172,080 for seller fraud, and $275,927 for mortgage payoff fraud per incident.
And the worst part: even with losses this high, insurance coverage gaps leave you exposed—many cyber policies exclude social engineering losses exactly when you need protection most.

Reputation and client trust also hang in the balance. A single fraud incident can destroy decades of relationship building and put your firm's future at risk.
Regulatory compliance and industry standards: expanding requirements
Federal rules such as GLBA mandate financial privacy protections, with new wire fraud reporting requirements adding further complexity.
At the same time, industry standards like ALTA Best Practices now embed cybersecurity as part of the expected standard of care. Meeting that standard is not optional: professional liability depends on it, and firms that fall short face both regulatory penalties and malpractice claims.
6 best practices for title companies
Several practices form the foundation of effective cybersecurity for title companies, addressing vulnerabilities that fraudsters exploit in real estate transactions. The following six should be at the top of every firm’s list:
1. Organize regular employee training
Real estate scenario training using industry-specific examples works best.
An attorney shared with us: “We've had several newsletters from Investors Title talking about seller identity fraud and it just scared us"—this targeted education shows real consequences.
Another good idea is to share quarterly fraud case studies featuring actual Business Email Compromise (BEC) attempts targeting your region or similar firms.
If you want to get even more practical, organize a role-playing exercise where staff practice handling "urgent" wire change requests and suspicious seller communications. Train your team to slow down and verify when pressure mounts during closing deadlines.
2. Use strong authentication
Implement a layered multi-factor authentication (MFA) approach with SMS (or another method) for general access and authenticator apps for email systems. Create title-specific implementation with separate authentication levels for processors, closers, and executives based on transaction authority.
Check authentication requirements across all your offices to ensure consistency. Implement device trust management by registering and monitoring all devices accessing client financial data.
3. Implement real estate fraud protection tool
Instead of running through manual verification callbacks that take 15-20 minutes each and leave liability on your team, verify payoff instructions automatically via secure platform
Automated verification systems like CertifID validate payoff instructions against extensive lender databases with up to 97% instant verification rates. The platform provides device analysis to detect overseas access attempts and compromised devices before fraud occurs.
Choose solutions that include device analysis and insurance-backed protection of up to $5M per file.
4. Keep software up to date
Prioritize patching for title production software such as SoftPro, RamQuest, Resware, and Qualia, given their access to sensitive transaction data. Use automated patch management to deploy updates during non-closing hours to avoid workflow disruption.
Apply security updates for email systems such as Exchange and Office 365 within 24 hours of release, again using automated patching outside business hours to avoid interruptions.
5. Restrict data access
Implement granular role permissions based on specific job functions.
In large operations with 250+ monthly closings, limit access so processors see different data than closers. Multi-office firms should implement geographic restrictions with location-based access controls.
Use session management with automatic 15-minute timeouts for financial systems and instant locking when staff step away. Run quarterly access audits to confirm who has access to what, especially after staff changes.
Authentication and user-management tools can streamline these controls, providing the building blocks without requiring your team to design security from scratch.
6. Develop and test an incident response plan
Establish a 15-minute response protocol with immediate wire recall procedures and account freezing contacts ready to act. Prepare communication templates with notifications for clients, underwriters, and regulators before you need them.
Run monthly tabletop exercises to keep your team prepared. Build recovery partnerships with specialists such as CertifID’s Fraud Recovery Services, which works with the Secret Service—a collaboration that has recovered over $100 million to date.
With the practices defined, the next step is the tools that make them work in real operations.
6 categories of best cybersecurity solutions for title companies
1. Real estate fraud protection solutions

Best cybersecurity solution for title companies:
CertifID—Real-time verification of wire details, payoffs and identity verification for escrow and closing transactions.
Prevents wire fraud losses by securely verifying identities and wiring instructions with direct insurance backing up to $5 million per file. The platform’s newest addition is a safe way to send digital payments, focused on earnest money deposits.
Why it's best: Purpose-built for real estate workflows with verified partnerships across major title production software systems. Our platform eliminates manual callback processes and provides first-party insurance coverage that protects your firm from liability.
Key features:
- Send, collect and request wiring instructions
- Verify business legitimacy before sending funds
- Payoff verification against comprehensive lender databases
- Identity verification using DMV databases and biometric matching
- Device fingerprinting to detect overseas access attempts
- Direct insurance coverage up to $5 million per file
- Fraud recovery services with documented Secret Service partnership
Integrations: SoftPro, AtClose, Settlor, RamQuest
2. Email security platforms
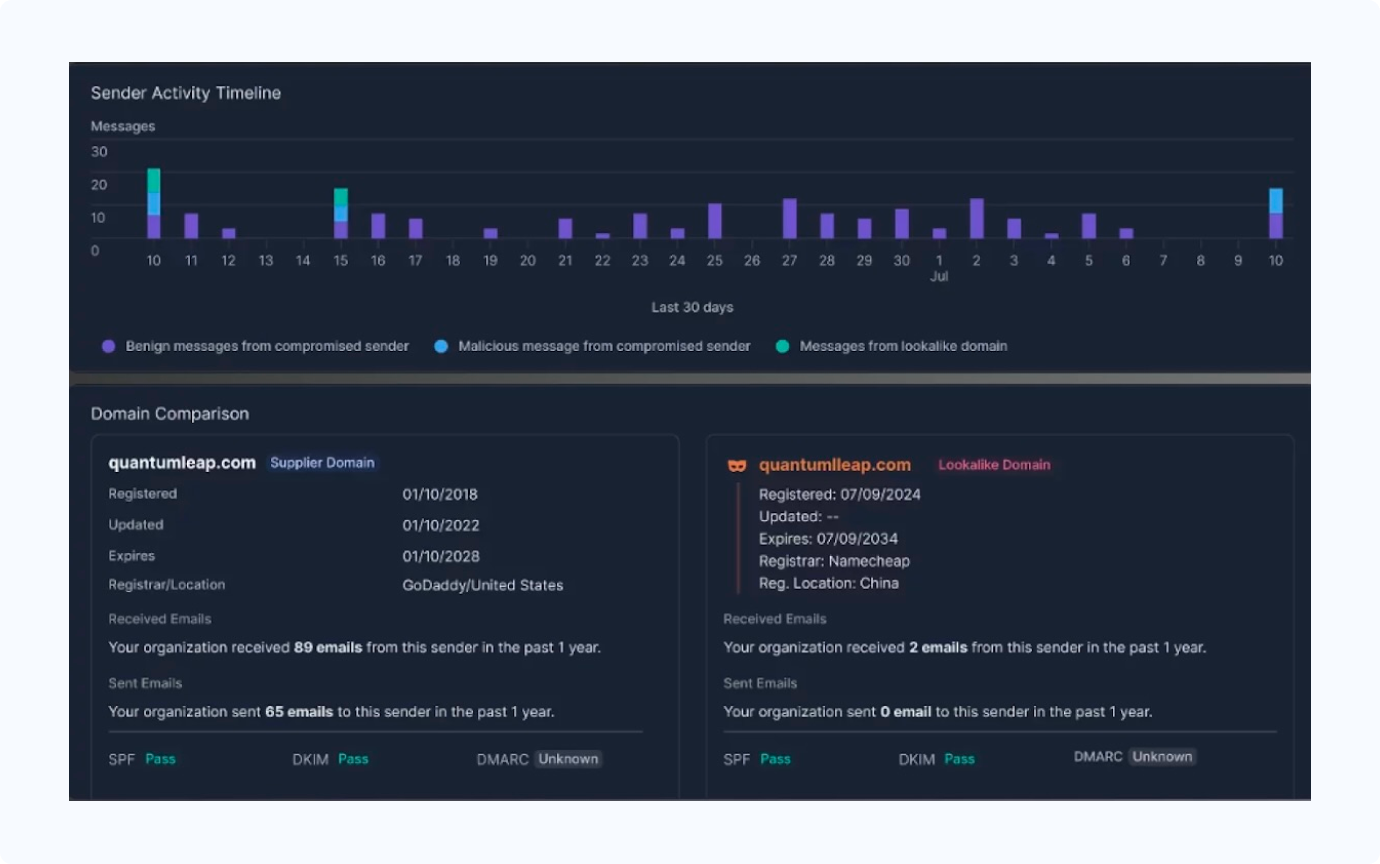
Best cybersecurity solution for title companies:
Proofpoint—Multi-layered filtering and encryption platform that blocks phishing, malware, and domain impersonation attempts targeting real estate transactions.
If your title agency operates in Microsoft or Google email environments, Proofpoint offers native integration with advanced threat protection and documented real estate-specific threat intelligence.
Why it's best: Offers domain impersonation protection and can detect spoofing attacks that target title companies with fake wiring instructions during closing periods.
Key features:
- Advanced threat detection that analyzes email behavior patterns
- Advanced domain impersonation protection (detects "firstamerican" vs "first-american")
- Encrypted email with automatic key management
- Safe link scanning and attachment sandboxing
- Real estate threat intelligence with published attack research
Integrations: Office 365, Exchange, Gmail, and most email platforms with API connectivity.
3. Identity and access management

Best cybersecurity solution for title companies:
Okta—Cloud-based identity platform providing encryption, multi-factor authentication, and role-based access management for distributed title operations. Scales across multiple offices while maintaining compliance.
Why it's best: Offers granular permissions that distinguish between processors, closers, and managers.
Key features:
- Multi-factor authentication: SMS, authenticator apps, hardware tokens
- Single sign-on reducing password fatigue across multiple systems
- Role-based access controls for different team members and locations
- Privileged access management for administrative accounts
- Automated user provisioning and offboarding
Integrations: SoftPro Hosted and 7,000+ pre-built app integrations verified through official Okta Integration Network.
4. Endpoint and network security

Best cybersecurity solution for title companies:
CrowdStrike Falcon—Cloud-native endpoint protection that safeguards laptops, desktops, servers, and mobile devices from ransomware and advanced threats.
Provides top-tier malware detection based on current 2024-2025 testing with automated response capabilities.
Why it's best: Designed for distributed organizations requiring real-time threat response without on-site IT infrastructure. Perfect for title companies with multiple offices and remote workers.
Key features:
- Behavioral analysis detecting unusual file access patterns using IOA (Indicators of Attack) methodology
- Zero-trust network access through ecosystem partnerships
- Automatic threat response isolating infected devices
- Single-agent deployment eliminating on-premises infrastructure
- Real-time threat hunting and incident response
Integrations: Windows, Mac, Linux systems, mobile devices, and network infrastructure with API connections to security orchestration platforms.
5. Security awareness training solutions
Best cybersecurity solution for title companies:
KnowBe4—Education platform with simulated attacks designed to change employee behavior and reduce human error risks.
Why it's best: Offers phishing simulation with AI-driven personalization that works for both tech-savvy and traditional employees, though without specialized real estate content modules.
Key features:
- Phishing simulations with extensive template library
- Social engineering awareness training for phone-based attacks
- Incident reporting tools encouraging employee participation
- Monthly knowledge checks with role-specific training modules
- Compliance tracking and detailed analytics
Integrations: Many integrations including Proofpoint and Okta.
6. Managed detection, response & backup
Best cybersecurity solution for title companies:
Veeam Backup & Replication—Enterprise data protection platform specifically designed for business continuity with 24/7 monitoring capabilities.
Provides backup, recovery, and replication solutions trusted by over 550,000 customers worldwide.
Why it's best: Industry-leading backup solution with verified 99.5% successful recovery rates and features tailored for sensitive financial data. Offers both on-premises and cloud deployment options with guaranteed recovery time objectives.
Key features:
- Immutable backup storage preventing ransomware encryption
- Instant Virtual Machine recovery with verified 15-minute recovery time objectives
- 3-2-1-1-0 backup rule implementation
- Automated backup verification and testing
- Cloud-native integrations with AWS, Azure, and Google Cloud
Integrations: VMware, Hyper-V, Microsoft 365, cloud platforms, and enterprise applications with comprehensive API support for title production software environments.
How to choose cybersecurity solutions for your title company
Selecting the right cybersecurity tools is about matching solutions to your firm’s size, workflows, and risk profile. CEOs can evaluate solutions and build a security stack that protects closings without slowing business down, guided by the following:
Assessment framework
Start by mapping your vulnerabilities based on transaction volume, geographic spread, and current security gaps. Review compliance requirements at both state and federal levels—your obligations vary based on location and business structure.
Consider integration with existing title software. Solutions that work with your current systems reduce training time and adoption friction. Plan for scalability so your systems support growth—for example, doubling from 200 to 400 closings monthly — without costly reconfiguration.
Vendor evaluation criteria
Demand proof of ROI with cost savings and risk reduction. Compare manual verification costs against automated solutions, factoring in liability reduction and insurance coverage.
Look for industry expertise through title company-specific features or proven integration with real estate workflows. Evaluate support and implementation quality including training, onboarding, and ongoing assistance.
Check for relevant certifications like SOC 2 compliance and insurance backing for financial protection. Also, request references from similar-sized companies in your market for realistic implementation expectations.
Common implementation pitfalls to avoid
Avoid over-investing in overlapping solutions that duplicate functionality without improving security. Equally, don't under-invest in employee training—technology alone won't protect against social engineering attacks. While humans are your best asset, they also create unexpected vulnerabilities.
Choose solutions that integrate with your current workflows rather than forcing process changes that create adoption resistance.
Best cybersecurity stack for title companies: Summary
The winning combination: CertifID for real estate fraud protection, Proofpoint for email security, Okta for identity management, CrowdStrike for endpoint protection, KnowBe4 for training, and Veeam for backup.
Together, these tools create a layered defense against attacks targeting title companies. If you’re in doubt whether to invest in security or not, consider that 79% of consumers will pay more to work with real estate businesses that prioritize security from wire fraud. In other words, security is a great differentiator that justifies premium pricing.
Start with CertifID's fraud protection platform.
With up to 97% instant verification rates, direct insurance coverage up to $5 million per file, and proven integration with major title production software, it provides the foundation for your cybersecurity defense.

FAQ
VP of Sales
Matt has over a decade of experience bringing disruptive Software-as-a-Service (SaaS) solutions to market in the automotive, MarTech, and real estate industries. He excels in high-growth tech companies with a passion for building and leading sales teams that deliver a memorable, consultative experience to prospective clients.
Title companies have become a prime hunting ground for cybercriminals. And the bigger the business, the bigger the target.
An ALTA survey found that 73% of title companies handling over 250 closings a month saw a spike in attacks, nearly double the rate of smaller firms.
Here's the CEO dilemma: you can't afford to slow down operations, but you can't afford to be the next fraud victim either.
This guide cuts through the complexity to show you practical cybersecurity solutions that balance protection with operational efficiency. We'll cover the best security platforms and practices designed for real estate transactions, plus show you which solution handles which threat.
Why do title companies need specialized cybersecurity?
There are several reasons title companies need to invest in specialized cybersecurity. We divide these into three main categories that make them especially vulnerable targets.
Real estate environment: high-stakes, multi-party transactions

High-value targets make you attractive to fraudsters. With average house prices hitting $510,300, criminals get big gains from successful attacks.
Your complex transaction web means access to multiple parties' financial data in single transactions, creating numerous attack vectors for exploitation.
Time pressure vulnerabilities compound the risk. Tight closing deadlines create pressure to bypass security protocols when "urgent" requests arrive. Extended attack windows during 30-60 day closing processes give fraudsters opportunities for email thread hijacking.
Also, exploiting public information makes targeting easier. Fraudsters use publicly available property records for seller identity theft and deploy communication impersonation through realtor and lender spoofing via domain manipulation.
Business survival: protection against financial loss
Catastrophic loss can cripple your title company.
According to our data, average losses hit $68,413 for buyer fraud, $172,080 for seller fraud, and $275,927 for mortgage payoff fraud per incident.
And the worst part: even with losses this high, insurance coverage gaps leave you exposed—many cyber policies exclude social engineering losses exactly when you need protection most.

Reputation and client trust also hang in the balance. A single fraud incident can destroy decades of relationship building and put your firm's future at risk.
Regulatory compliance and industry standards: expanding requirements
Federal rules such as GLBA mandate financial privacy protections, with new wire fraud reporting requirements adding further complexity.
At the same time, industry standards like ALTA Best Practices now embed cybersecurity as part of the expected standard of care. Meeting that standard is not optional: professional liability depends on it, and firms that fall short face both regulatory penalties and malpractice claims.
6 best practices for title companies
Several practices form the foundation of effective cybersecurity for title companies, addressing vulnerabilities that fraudsters exploit in real estate transactions. The following six should be at the top of every firm’s list:
1. Organize regular employee training
Real estate scenario training using industry-specific examples works best.
An attorney shared with us: “We've had several newsletters from Investors Title talking about seller identity fraud and it just scared us"—this targeted education shows real consequences.
Another good idea is to share quarterly fraud case studies featuring actual Business Email Compromise (BEC) attempts targeting your region or similar firms.
If you want to get even more practical, organize a role-playing exercise where staff practice handling "urgent" wire change requests and suspicious seller communications. Train your team to slow down and verify when pressure mounts during closing deadlines.
2. Use strong authentication
Implement a layered multi-factor authentication (MFA) approach with SMS (or another method) for general access and authenticator apps for email systems. Create title-specific implementation with separate authentication levels for processors, closers, and executives based on transaction authority.
Check authentication requirements across all your offices to ensure consistency. Implement device trust management by registering and monitoring all devices accessing client financial data.
3. Implement real estate fraud protection tool
Instead of running through manual verification callbacks that take 15-20 minutes each and leave liability on your team, verify payoff instructions automatically via secure platform
Automated verification systems like CertifID validate payoff instructions against extensive lender databases with up to 97% instant verification rates. The platform provides device analysis to detect overseas access attempts and compromised devices before fraud occurs.
Choose solutions that include device analysis and insurance-backed protection of up to $5M per file.
4. Keep software up to date
Prioritize patching for title production software such as SoftPro, RamQuest, Resware, and Qualia, given their access to sensitive transaction data. Use automated patch management to deploy updates during non-closing hours to avoid workflow disruption.
Apply security updates for email systems such as Exchange and Office 365 within 24 hours of release, again using automated patching outside business hours to avoid interruptions.
5. Restrict data access
Implement granular role permissions based on specific job functions.
In large operations with 250+ monthly closings, limit access so processors see different data than closers. Multi-office firms should implement geographic restrictions with location-based access controls.
Use session management with automatic 15-minute timeouts for financial systems and instant locking when staff step away. Run quarterly access audits to confirm who has access to what, especially after staff changes.
Authentication and user-management tools can streamline these controls, providing the building blocks without requiring your team to design security from scratch.
6. Develop and test an incident response plan
Establish a 15-minute response protocol with immediate wire recall procedures and account freezing contacts ready to act. Prepare communication templates with notifications for clients, underwriters, and regulators before you need them.
Run monthly tabletop exercises to keep your team prepared. Build recovery partnerships with specialists such as CertifID’s Fraud Recovery Services, which works with the Secret Service—a collaboration that has recovered over $100 million to date.
With the practices defined, the next step is the tools that make them work in real operations.
6 categories of best cybersecurity solutions for title companies
1. Real estate fraud protection solutions

Best cybersecurity solution for title companies:
CertifID—Real-time verification of wire details, payoffs and identity verification for escrow and closing transactions.
Prevents wire fraud losses by securely verifying identities and wiring instructions with direct insurance backing up to $5 million per file. The platform’s newest addition is a safe way to send digital payments, focused on earnest money deposits.
Why it's best: Purpose-built for real estate workflows with verified partnerships across major title production software systems. Our platform eliminates manual callback processes and provides first-party insurance coverage that protects your firm from liability.
Key features:
- Send, collect and request wiring instructions
- Verify business legitimacy before sending funds
- Payoff verification against comprehensive lender databases
- Identity verification using DMV databases and biometric matching
- Device fingerprinting to detect overseas access attempts
- Direct insurance coverage up to $5 million per file
- Fraud recovery services with documented Secret Service partnership
Integrations: SoftPro, AtClose, Settlor, RamQuest
2. Email security platforms

Best cybersecurity solution for title companies:
Proofpoint—Multi-layered filtering and encryption platform that blocks phishing, malware, and domain impersonation attempts targeting real estate transactions.
If your title agency operates in Microsoft or Google email environments, Proofpoint offers native integration with advanced threat protection and documented real estate-specific threat intelligence.
Why it's best: Offers domain impersonation protection and can detect spoofing attacks that target title companies with fake wiring instructions during closing periods.
Key features:
- Advanced threat detection that analyzes email behavior patterns
- Advanced domain impersonation protection (detects "firstamerican" vs "first-american")
- Encrypted email with automatic key management
- Safe link scanning and attachment sandboxing
- Real estate threat intelligence with published attack research
Integrations: Office 365, Exchange, Gmail, and most email platforms with API connectivity.
3. Identity and access management

Best cybersecurity solution for title companies:
Okta—Cloud-based identity platform providing encryption, multi-factor authentication, and role-based access management for distributed title operations. Scales across multiple offices while maintaining compliance.
Why it's best: Offers granular permissions that distinguish between processors, closers, and managers.
Key features:
- Multi-factor authentication: SMS, authenticator apps, hardware tokens
- Single sign-on reducing password fatigue across multiple systems
- Role-based access controls for different team members and locations
- Privileged access management for administrative accounts
- Automated user provisioning and offboarding
Integrations: SoftPro Hosted and 7,000+ pre-built app integrations verified through official Okta Integration Network.
4. Endpoint and network security

Best cybersecurity solution for title companies:
CrowdStrike Falcon—Cloud-native endpoint protection that safeguards laptops, desktops, servers, and mobile devices from ransomware and advanced threats.
Provides top-tier malware detection based on current 2024-2025 testing with automated response capabilities.
Why it's best: Designed for distributed organizations requiring real-time threat response without on-site IT infrastructure. Perfect for title companies with multiple offices and remote workers.
Key features:
- Behavioral analysis detecting unusual file access patterns using IOA (Indicators of Attack) methodology
- Zero-trust network access through ecosystem partnerships
- Automatic threat response isolating infected devices
- Single-agent deployment eliminating on-premises infrastructure
- Real-time threat hunting and incident response
Integrations: Windows, Mac, Linux systems, mobile devices, and network infrastructure with API connections to security orchestration platforms.
5. Security awareness training solutions
Best cybersecurity solution for title companies:
KnowBe4—Education platform with simulated attacks designed to change employee behavior and reduce human error risks.
Why it's best: Offers phishing simulation with AI-driven personalization that works for both tech-savvy and traditional employees, though without specialized real estate content modules.
Key features:
- Phishing simulations with extensive template library
- Social engineering awareness training for phone-based attacks
- Incident reporting tools encouraging employee participation
- Monthly knowledge checks with role-specific training modules
- Compliance tracking and detailed analytics
Integrations: Many integrations including Proofpoint and Okta.
6. Managed detection, response & backup
Best cybersecurity solution for title companies:
Veeam Backup & Replication—Enterprise data protection platform specifically designed for business continuity with 24/7 monitoring capabilities.
Provides backup, recovery, and replication solutions trusted by over 550,000 customers worldwide.
Why it's best: Industry-leading backup solution with verified 99.5% successful recovery rates and features tailored for sensitive financial data. Offers both on-premises and cloud deployment options with guaranteed recovery time objectives.
Key features:
- Immutable backup storage preventing ransomware encryption
- Instant Virtual Machine recovery with verified 15-minute recovery time objectives
- 3-2-1-1-0 backup rule implementation
- Automated backup verification and testing
- Cloud-native integrations with AWS, Azure, and Google Cloud
Integrations: VMware, Hyper-V, Microsoft 365, cloud platforms, and enterprise applications with comprehensive API support for title production software environments.
How to choose cybersecurity solutions for your title company
Selecting the right cybersecurity tools is about matching solutions to your firm’s size, workflows, and risk profile. CEOs can evaluate solutions and build a security stack that protects closings without slowing business down, guided by the following:
Assessment framework
Start by mapping your vulnerabilities based on transaction volume, geographic spread, and current security gaps. Review compliance requirements at both state and federal levels—your obligations vary based on location and business structure.
Consider integration with existing title software. Solutions that work with your current systems reduce training time and adoption friction. Plan for scalability so your systems support growth—for example, doubling from 200 to 400 closings monthly — without costly reconfiguration.
Vendor evaluation criteria
Demand proof of ROI with cost savings and risk reduction. Compare manual verification costs against automated solutions, factoring in liability reduction and insurance coverage.
Look for industry expertise through title company-specific features or proven integration with real estate workflows. Evaluate support and implementation quality including training, onboarding, and ongoing assistance.
Check for relevant certifications like SOC 2 compliance and insurance backing for financial protection. Also, request references from similar-sized companies in your market for realistic implementation expectations.
Common implementation pitfalls to avoid
Avoid over-investing in overlapping solutions that duplicate functionality without improving security. Equally, don't under-invest in employee training—technology alone won't protect against social engineering attacks. While humans are your best asset, they also create unexpected vulnerabilities.
Choose solutions that integrate with your current workflows rather than forcing process changes that create adoption resistance.
Best cybersecurity stack for title companies: Summary
The winning combination: CertifID for real estate fraud protection, Proofpoint for email security, Okta for identity management, CrowdStrike for endpoint protection, KnowBe4 for training, and Veeam for backup.
Together, these tools create a layered defense against attacks targeting title companies. If you’re in doubt whether to invest in security or not, consider that 79% of consumers will pay more to work with real estate businesses that prioritize security from wire fraud. In other words, security is a great differentiator that justifies premium pricing.
Start with CertifID's fraud protection platform.
With up to 97% instant verification rates, direct insurance coverage up to $5 million per file, and proven integration with major title production software, it provides the foundation for your cybersecurity defense.

VP of Sales
Matt has over a decade of experience bringing disruptive Software-as-a-Service (SaaS) solutions to market in the automotive, MarTech, and real estate industries. He excels in high-growth tech companies with a passion for building and leading sales teams that deliver a memorable, consultative experience to prospective clients.
Sign up for The Wire to join the conversation.



.png)
.png)



