Recognize and prevent real estate wire fraud before it’s too late
Wire fraud is real estate’s fastest-growing threat. Learn how to protect every deal with proactive strategies that actually work.
Tom Cronkright
11 minutes
Wire Fraud
Jul 19, 2021
Aug 14, 2025
Real estate wire fraud: Red flags, risks, and how to stay safe
Wire fraud isn’t slowing down. In 2023, business email compromise (BEC) alone caused over $2.7 billion in losses, according to the 2025 State of Wire Fraud Report. And real estate is a top target.
What was once a $50 million issue is now a $500 million+ crisis. Nearly 1 in 4 real estate transactions involve suspicious or potentially fraudulent activity.
Fraudsters understand how closings work and how to exploit their speed with fake emails and spoofed wire instructions.
Once the money is gone, recovery is difficult. That’s why understanding the risks (and how to get ahead of them) matters.
Let’s look at how wire fraud works, who’s at risk, and how to protect every transaction.
What is wire fraud in real estate?
Wire fraud in real estate happens when a fraudster tricks someone in a real estate transaction into sending funds to a fraudulent account, usually through a spoofed email, text, or call that looks legitimate.
In 2022, the FBI reported $446 million in real estate wire fraud losses, accounting for 17% of all business email compromise (BEC) cases.
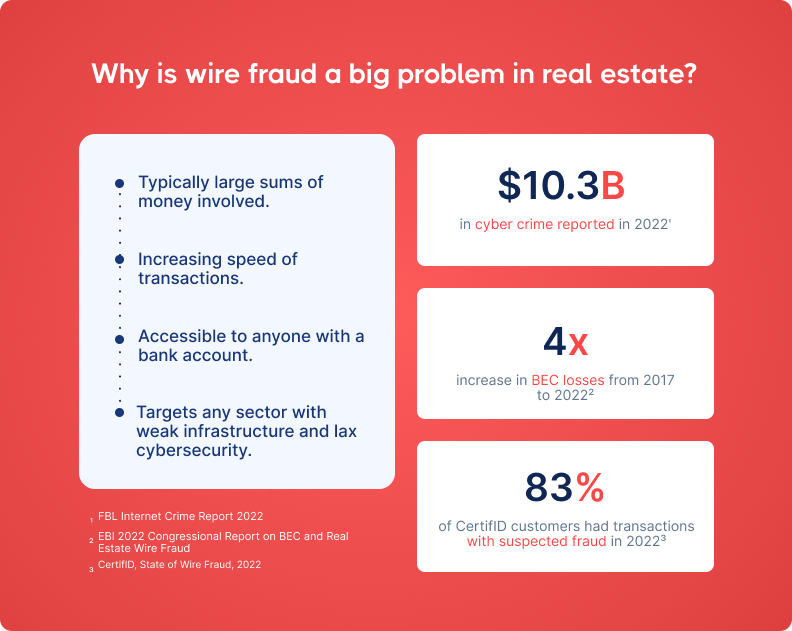
Why is real estate such a prime target? Big money, tight timelines, and lots of people communicating over email. Every step adds complexity and another chance for fraudsters to sneak in.
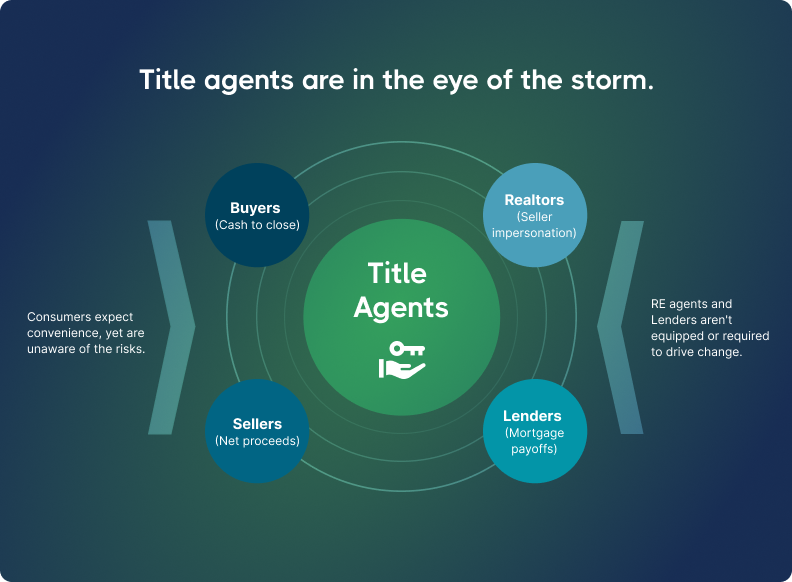
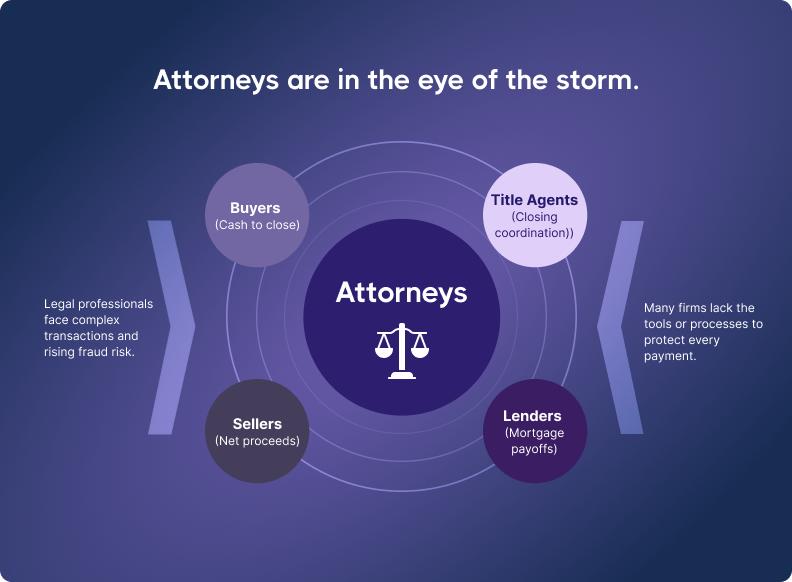
The biggest risk is during closings, earnest money transfers, or down payments.
A common scenario involves a buyer who is ready to send their down payment or closing funds. Suddenly, they get what looks like a legitimate email from their agent or title company with updated instructions. But the message is fake, and once the wire is sent, recovery is rare.
Fraudsters don’t just hit buyers. Sellers, attorneys, and title companies are all at risk. All it takes is a convincing impersonation and just enough urgency to override caution.
And these scams aren’t rare. Roughly 1 in 20 real estate transactions is targeted by some form of wire fraud attempt. That’s a far higher risk than the things most people buy insurance for, like car accidents (1 in 200) or house fires (1 in 350).
This isn’t a one-off risk. It’s an everyday threat. That’s why real estate professionals need safeguards in place to protect every payment.
How does wire fraud in real estate work?
Wire fraud in real estate is rarely random. It’s a calculated scam that blends into the flow of a normal transaction.
Fraudsters start by collecting details from public records or hacked emails: names, dates, and dollar amounts. Then they impersonate someone in the deal, sending fake wire instructions that reroute funds to their own account.
By the time anyone notices, the money is usually gone, moved quickly through multiple accounts, sometimes overseas, making recovery difficult.
As security improves, so do their tactics. From business impersonation to down payment scams, fraudsters continue to evolve. Let’s get into what that looks like.
Business email compromise (BEC): The foundation of most fraud
Most real estate wire fraud starts with business email compromise (BEC). This isn’t just phishing. It’s full-blown access to someone’s email account.
Fraudsters break into email accounts of buyers, sellers, or professionals, then quietly watch for weeks or months. They study the timing, tone, and money involved, sometimes setting up forwarding rules to stay hidden.
By the time they send fake wire instructions, everything looks normal, right names, right amounts, and right tone. That’s what makes BEC so dangerous. It’s deliberate, patient, and designed to strike when everyone’s guard is down.
This short video breaks down how a typical scam unfolds and why it’s so easy to fall for.
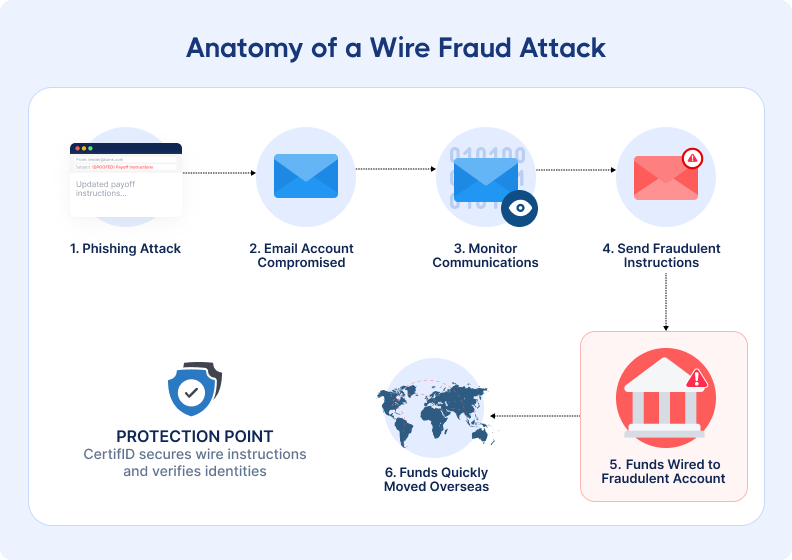
Fake banking instructions: The critical deception
Once fraudsters have the details, they send fake wire instructions (usually via email) that look legitimate. Names, signatures, and subject lines all check out, but the account details point to the fraudster.
They strike during the “kill zone,” just before closing, when urgency is high and scrutiny is low. A simple “There’s been a change” can trigger a transfer.
By the time anyone notices, the money is already gone, moved through layers of accounts and often overseas.
That’s why the only real defense is prevention. And today, prevention often comes down to the tools you use to protect sensitive information.
CertifID replaces risky emails and last-minute calls with a secure, guided process to verify wire instructions before funds are transferred.
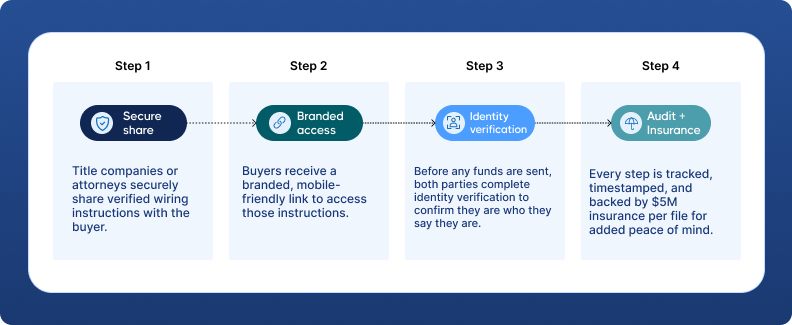
Instead of crossing your fingers and hoping everything goes smoothly, you get peace of mind backed by a secure system that protects everyone involved.
Business impersonation: Bypassing email compromise entirely
Some fraudsters skip hacking and simply impersonate entire businesses. They clone websites, mimic domains (like swapping a lowercase “l” for a capital “I”), and use official-looking branding to appear legitimate.
This tactic is on the rise, sometimes used on its own or alongside BEC scams. As one insider noted, “We’re seeing impersonation, either of a title agency or of a buyer or seller to the title agency.”
Because no actual account is compromised, these scams are even harder to detect. Fraudsters often target buyers directly, where trust is high and the fallout can be devastating.
Down payment fraud: Targeting buyers' largest funds
For buyers, wiring a down payment is often the biggest financial move of their lives.
That’s why fraudsters target them directly, posing as the buyer’s agent or title contact. They send fake wire instructions timed to hit just before closing. In the final rush, buyers may act fast without verifying. One click, and the money’s gone.
These scams are rising fast because they bypass usual safeguards, hitting buyers where they’re most vulnerable. That’s why slowing down to verify isn’t a hassle. It’s the difference between a successful closing and a financial disaster.
Emerging sophisticated real estate fraud techniques
Business email compromise and down payment scams aren’t the only risks. Fraudsters are evolving, with seller impersonation fraud quickly becoming one of the most damaging and hardest to catch.
Seller impersonation fraud
Fraudsters pose as property owners, often of vacant land or commercial properties, and push fake sales using forged documents, fake IDs, and remote notarizations to avoid in-person checks.
These properties attract less scrutiny, letting fraudsters slip further into the transaction before getting caught. It’s become a top concern for title companies and real estate attorneys.
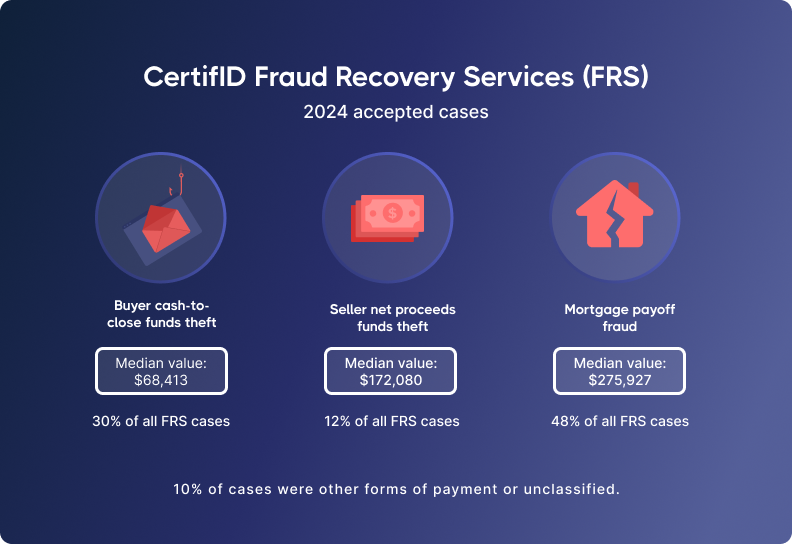
Mortgage payoff fraud
Mortgage payoff fraud hits at closing, when fraudsters send fake payoff instructions to the title company, diverting funds meant for the seller’s loan.
It often goes unnoticed until weeks later, when the real lender reports the mortgage hasn’t been paid. By then, the money is gone, leaving title companies, sellers, and buyers scrambling to recover.
Some scams go even further, using fake identities that look legitimate, adding another layer of deception to an already high-risk moment.

Synthetic identity fraud
Unlike impersonation, synthetic identity fraud mixes real data, like partial records or common names, with fake documents to create entirely new identities. Fraudsters use this hybrid approach to pose as property owners.
It’s especially dangerous in vacant land or commercial deals, where face-to-face contact is rare. Without layered verification, synthetic identities can slip through standard checks. As the tactic grows, real estate professionals are rethinking how they confirm who’s really behind each transaction.
Who does wire fraud affect in real estate?
No one’s off-limits: buyers, sellers, attorneys, and lenders are all targets. But title and escrow companies face the highest risk.
Title and escrow companies
At the center of every closing, title and escrow teams handle large sums of money and sensitive data. That responsibility comes with major exposure. If a wire is misdirected, they may still be held liable for the loss, even if they weren’t at fault.
With high-dollar transactions moving daily, basic checks aren’t enough. That’s why title and escrow firms can benefit from:
- Strong identity and wire verification tools
- Insurance coverage tailored to wire fraud risks
The goal is to minimize risk, protect client trust, and keep deals on track.
Law firms
In real estate deals, especially commercial deals, law firms sit at the center, managing escrow accounts and overseeing large transfers of money.
Fraudsters see attorneys as trusted parties, but long email threads and complex closings give scams room to operate. In states like South Carolina, where lawyers handle mortgage payoffs, funds may pass through multiple hands, each step adding risk.
Good intentions aren’t enough. Law firms need secure tools to verify wire details, protect communication, and prevent costly mistakes. Because once funds are gone, trust won’t bring them back.
Real estate agents and brokers
Real estate agents and brokers are the glue in most transactions, managing daily details, keeping everyone informed, and serving as the main point of contact for buyers and sellers. That central role makes them both trusted and exposed.
If an agent’s email is hacked or spoofed, fraudsters can send convincing wire instructions that derail the entire deal. When funds go missing, agents may lose commissions, face reputational damage, or even end up in court.
Staying alert helps, but it isn’t enough. Agents should work with title and legal partners who use secure platforms for wire transfers, keeping financial details out of email and everyone protected.
Buyers and sellers
Buyers and sellers often suffer the greatest losses in a wire fraud scam, and the impact can be life-changing.
More than 1 in 20 buyers fall victim to fraud, and over 1 in 10 are targeted. Yet over half of consumers say they’re only “somewhat” or “not aware” of the risk. That lack of awareness, paired with the pressure of closing, leaves buyers especially vulnerable. A single misstep, like wiring funds to a fake account, can wipe out a life’s savings.
Sellers aren’t spared either. If payoff funds are stolen or delayed, deals collapse, legal risks rise, and ripple effects can impact multiple transactions.
That’s why early education and secure verification matter, so both sides are protected when it matters most.
How to identify wire fraud in real estate
Wire fraud often hides in plain sight, in small changes, odd requests, or instructions that feel off. Watch for subtle signs like email address tweaks, last-minute updates, or anything that breaks the normal process.
Wire fraud red flags for title companies
With hundreds of wires and tasks moving quickly, title and escrow companies are prime targets. Fraudsters exploit the speed and volume, so staying alert to these red flags is essential to protect your team and clients.
- Mismatched account info: Routing or account numbers don’t align with known records
- Communication changes: Parties stop answering calls but still reply by email
- Unusual amounts: Payoff totals don’t match the loan balance
- Name mismatches: Account names don’t match the lender or institution
- Repeated adjustments: Multiple last-minute updates to wiring details
- Confidentiality pressure: Requests to keep wire changes secret
Even one red flag is worth slowing down for. Speed is what scammers count on. And it’s not just title companies at risk. Law firms managing closings face the threats and responsibility to protect client funds.
Wire fraud red flags for law firms
Wire fraud is a growing threat to law firms, putting client trust, reputation, and large sums of money at risk. Attorneys handling complex, high-value deals are prime targets. Watch for these warning signs:
- Skipping protocol: Requests to avoid escrow or normal fund handling
- Avoided calls: Refusal to talk by phone; insists on email only
- Rushed closings: Unusual pressure to close quickly
- Odd statements: Errors or odd formatting in settlement paperwork
- Email lookalikes: Slight changes in familiar addresses
- Off-brand files: Unfamiliar layouts, language, or logos in attachments
Watch for deals that don’t add up, like underpriced properties or sellers without a referral. Even routine closings can hide risks, so staying alert protects your clients and your firm.
Advanced warning signs of wire fraud in real estate for businesses
Basic red flags, like mismatched names or odd amounts, are important, but busy businesses need to watch for more subtle signs that can easily slip by:
- Fake portals: Spoofed logins to steal credentials
- Deceptive domains: Slight letter swaps or added punctuation
- Tone changes: Shifts from formal to overly casual or urgent
- Verification skips: Attempts to bypass security checks
- False urgency: Emergency requests with fake deadlines
- Off-hours edits: Files created at odd times, suggesting tampering
These signs demand close attention and technical know-how, and the risk extends far beyond just businesses.
Warning signs of wire fraud for buyers and sellers
Wire fraud can feel overwhelming, especially for those unfamiliar with real estate deals. But clear warning signs often appear, if you know what to look for:
- Last-minute changes: Updates to wire instructions just before closing
- Email-only directives: Wire details sent without prior notice or phone confirmation
- Urgent requests: High-pressure push to send funds immediately
- Conflicting information: Details that don’t match earlier communications
- Language issues: Messages with odd phrasing, grammar, or spelling errors
- Unusual timing: Emails or texts sent at unusual hours
- Recipient red flags: Wire directed to a personal instead of business or escrow account
Even the most cautious buyers and sellers can be misled, especially when manual verification breaks down.
How to avoid wire fraud in real estate
Wire fraud prevention takes more than phone calls and paper checks. The most effective strategies combine technology, team training, and clear communication at every step of the transaction.
Wire fraud prevention strategies
Real estate fraud has moved beyond simple email hacks. Staying protected means layering secure tools with strong, consistent processes.
Use secure, digital platforms to verify wiring details and catch what human checks can miss.
Be sure to establish clear protocols. Set expectations early with clients. And follow the same process every time, so there’s no guesswork when it matters most.
Best practices for title companies
For title teams, strong fraud prevention comes down to process and people.
Require dual approval for wires over a set amount. Build in mandatory wait periods for any changes to wire instructions. Train staff on role-specific red flags they might face, and keep a verified list of trusted payees so you’re not starting from scratch each time.
And don’t overlook coverage. Make sure your insurance includes social engineering and wire fraud protection.
Best practices for law firms
Law firms must balance client confidentiality with strong fraud protection.
Set up client-specific verification methods instead of blanket rules. Require attorney review before any wire changes. Replace email attachments with encrypted portals, and clearly define approval authority to avoid confusion.
Above all, build processes that secure transactions without compromising privacy.
What to do if you become a victim of wire fraud
Even with strong safeguards in place, no system is foolproof. If fraud happens, knowing how to respond quickly and decisively can make all the difference.
If fraud occurs in real estate
Act immediately. Contact your bank or financial institution immediately, within minutes if possible. The sooner you alert them, the better your chances of freezing or recovering funds before they move out of reach.
Document everything. Save all emails, call logs, wire instructions, and verification steps. This record is critical for law enforcement, your insurer, and any legal follow-up.
Report properly. File a report with the FBI’s Internet Crime Complaint Center (IC3) right away. Timely reporting helps federal agencies investigate and track down fraudulent activity.
Get expert assistance. Wire fraud recovery can be complex. Consider working with professionals who specialize in fund recovery and regulatory response. Their expertise can speed the process and improve your chances of a positive outcome.
Wire fraud in real estate can be stopped
Wire fraud is one of the most damaging threats in real estate today, but it’s one you can get ahead of. With the right protections in place, you can defend your transactions, your clients, and your business from costly losses. CertifID gives you the confidence to move securely, with verified identities and insured wire transfers backed by up to $5M in direct coverage.
Want to stay informed? Subscribe to The Wire, our weekly newsletter, for real-world fraud updates, prevention tips, and expert insights.
FAQ
Co-founder & Executive Chairman
Tom Cronkright is the Executive Chairman of CertifID, a technology platform designed to safeguard electronic payments from fraud. He co-founded the company in response to a wire fraud he experienced and the rising instances of real estate wire fraud. He also serves as the CEO of Sun Title, a leading title agency in Michigan. Tom is a licensed attorney, real estate broker, title insurance producer and nationally recognized expert on cybersecurity and wire fraud.
Real estate wire fraud: Red flags, risks, and how to stay safe
Wire fraud isn’t slowing down. In 2023, business email compromise (BEC) alone caused over $2.7 billion in losses, according to the 2025 State of Wire Fraud Report. And real estate is a top target.
What was once a $50 million issue is now a $500 million+ crisis. Nearly 1 in 4 real estate transactions involve suspicious or potentially fraudulent activity.
Fraudsters understand how closings work and how to exploit their speed with fake emails and spoofed wire instructions.
Once the money is gone, recovery is difficult. That’s why understanding the risks (and how to get ahead of them) matters.
Let’s look at how wire fraud works, who’s at risk, and how to protect every transaction.
What is wire fraud in real estate?
Wire fraud in real estate happens when a fraudster tricks someone in a real estate transaction into sending funds to a fraudulent account, usually through a spoofed email, text, or call that looks legitimate.
In 2022, the FBI reported $446 million in real estate wire fraud losses, accounting for 17% of all business email compromise (BEC) cases.

Why is real estate such a prime target? Big money, tight timelines, and lots of people communicating over email. Every step adds complexity and another chance for fraudsters to sneak in.


The biggest risk is during closings, earnest money transfers, or down payments.
A common scenario involves a buyer who is ready to send their down payment or closing funds. Suddenly, they get what looks like a legitimate email from their agent or title company with updated instructions. But the message is fake, and once the wire is sent, recovery is rare.
Fraudsters don’t just hit buyers. Sellers, attorneys, and title companies are all at risk. All it takes is a convincing impersonation and just enough urgency to override caution.

And these scams aren’t rare. Roughly 1 in 20 real estate transactions is targeted by some form of wire fraud attempt. That’s a far higher risk than the things most people buy insurance for, like car accidents (1 in 200) or house fires (1 in 350).
This isn’t a one-off risk. It’s an everyday threat. That’s why real estate professionals need safeguards in place to protect every payment.
How does wire fraud in real estate work?
Wire fraud in real estate is rarely random. It’s a calculated scam that blends into the flow of a normal transaction.
Fraudsters start by collecting details from public records or hacked emails: names, dates, and dollar amounts. Then they impersonate someone in the deal, sending fake wire instructions that reroute funds to their own account.
By the time anyone notices, the money is usually gone, moved quickly through multiple accounts, sometimes overseas, making recovery difficult.
As security improves, so do their tactics. From business impersonation to down payment scams, fraudsters continue to evolve. Let’s get into what that looks like.
Business email compromise (BEC): The foundation of most fraud
Most real estate wire fraud starts with business email compromise (BEC). This isn’t just phishing. It’s full-blown access to someone’s email account.
Fraudsters break into email accounts of buyers, sellers, or professionals, then quietly watch for weeks or months. They study the timing, tone, and money involved, sometimes setting up forwarding rules to stay hidden.
By the time they send fake wire instructions, everything looks normal, right names, right amounts, and right tone. That’s what makes BEC so dangerous. It’s deliberate, patient, and designed to strike when everyone’s guard is down.
This short video breaks down how a typical scam unfolds and why it’s so easy to fall for.
Fake banking instructions: The critical deception
Once fraudsters have the details, they send fake wire instructions (usually via email) that look legitimate. Names, signatures, and subject lines all check out, but the account details point to the fraudster.
They strike during the “kill zone,” just before closing, when urgency is high and scrutiny is low. A simple “There’s been a change” can trigger a transfer.
By the time anyone notices, the money is already gone, moved through layers of accounts and often overseas.

That’s why the only real defense is prevention. And today, prevention often comes down to the tools you use to protect sensitive information.
CertifID replaces risky emails and last-minute calls with a secure, guided process to verify wire instructions before funds are transferred.

Instead of crossing your fingers and hoping everything goes smoothly, you get peace of mind backed by a secure system that protects everyone involved.
Business impersonation: Bypassing email compromise entirely
Some fraudsters skip hacking and simply impersonate entire businesses. They clone websites, mimic domains (like swapping a lowercase “l” for a capital “I”), and use official-looking branding to appear legitimate.
This tactic is on the rise, sometimes used on its own or alongside BEC scams. As one insider noted, “We’re seeing impersonation, either of a title agency or of a buyer or seller to the title agency.”
Because no actual account is compromised, these scams are even harder to detect. Fraudsters often target buyers directly, where trust is high and the fallout can be devastating.
Down payment fraud: Targeting buyers' largest funds
For buyers, wiring a down payment is often the biggest financial move of their lives.
That’s why fraudsters target them directly, posing as the buyer’s agent or title contact. They send fake wire instructions timed to hit just before closing. In the final rush, buyers may act fast without verifying. One click, and the money’s gone.
These scams are rising fast because they bypass usual safeguards, hitting buyers where they’re most vulnerable. That’s why slowing down to verify isn’t a hassle. It’s the difference between a successful closing and a financial disaster.
Emerging sophisticated real estate fraud techniques
Business email compromise and down payment scams aren’t the only risks. Fraudsters are evolving, with seller impersonation fraud quickly becoming one of the most damaging and hardest to catch.
Seller impersonation fraud
Fraudsters pose as property owners, often of vacant land or commercial properties, and push fake sales using forged documents, fake IDs, and remote notarizations to avoid in-person checks.
These properties attract less scrutiny, letting fraudsters slip further into the transaction before getting caught. It’s become a top concern for title companies and real estate attorneys.
Mortgage payoff fraud
Mortgage payoff fraud hits at closing, when fraudsters send fake payoff instructions to the title company, diverting funds meant for the seller’s loan.
It often goes unnoticed until weeks later, when the real lender reports the mortgage hasn’t been paid. By then, the money is gone, leaving title companies, sellers, and buyers scrambling to recover.
Some scams go even further, using fake identities that look legitimate, adding another layer of deception to an already high-risk moment.

Synthetic identity fraud
Unlike impersonation, synthetic identity fraud mixes real data, like partial records or common names, with fake documents to create entirely new identities. Fraudsters use this hybrid approach to pose as property owners.
It’s especially dangerous in vacant land or commercial deals, where face-to-face contact is rare. Without layered verification, synthetic identities can slip through standard checks. As the tactic grows, real estate professionals are rethinking how they confirm who’s really behind each transaction.
Who does wire fraud affect in real estate?
No one’s off-limits: buyers, sellers, attorneys, and lenders are all targets. But title and escrow companies face the highest risk.
Title and escrow companies
At the center of every closing, title and escrow teams handle large sums of money and sensitive data. That responsibility comes with major exposure. If a wire is misdirected, they may still be held liable for the loss, even if they weren’t at fault.
With high-dollar transactions moving daily, basic checks aren’t enough. That’s why title and escrow firms can benefit from:
- Strong identity and wire verification tools
- Insurance coverage tailored to wire fraud risks
The goal is to minimize risk, protect client trust, and keep deals on track.
Law firms
In real estate deals, especially commercial deals, law firms sit at the center, managing escrow accounts and overseeing large transfers of money.
Fraudsters see attorneys as trusted parties, but long email threads and complex closings give scams room to operate. In states like South Carolina, where lawyers handle mortgage payoffs, funds may pass through multiple hands, each step adding risk.
Good intentions aren’t enough. Law firms need secure tools to verify wire details, protect communication, and prevent costly mistakes. Because once funds are gone, trust won’t bring them back.
Real estate agents and brokers
Real estate agents and brokers are the glue in most transactions, managing daily details, keeping everyone informed, and serving as the main point of contact for buyers and sellers. That central role makes them both trusted and exposed.
If an agent’s email is hacked or spoofed, fraudsters can send convincing wire instructions that derail the entire deal. When funds go missing, agents may lose commissions, face reputational damage, or even end up in court.
Staying alert helps, but it isn’t enough. Agents should work with title and legal partners who use secure platforms for wire transfers, keeping financial details out of email and everyone protected.
Buyers and sellers
Buyers and sellers often suffer the greatest losses in a wire fraud scam, and the impact can be life-changing.
More than 1 in 20 buyers fall victim to fraud, and over 1 in 10 are targeted. Yet over half of consumers say they’re only “somewhat” or “not aware” of the risk. That lack of awareness, paired with the pressure of closing, leaves buyers especially vulnerable. A single misstep, like wiring funds to a fake account, can wipe out a life’s savings.
Sellers aren’t spared either. If payoff funds are stolen or delayed, deals collapse, legal risks rise, and ripple effects can impact multiple transactions.
That’s why early education and secure verification matter, so both sides are protected when it matters most.
How to identify wire fraud in real estate
Wire fraud often hides in plain sight, in small changes, odd requests, or instructions that feel off. Watch for subtle signs like email address tweaks, last-minute updates, or anything that breaks the normal process.
Wire fraud red flags for title companies
With hundreds of wires and tasks moving quickly, title and escrow companies are prime targets. Fraudsters exploit the speed and volume, so staying alert to these red flags is essential to protect your team and clients.
- Mismatched account info: Routing or account numbers don’t align with known records
- Communication changes: Parties stop answering calls but still reply by email
- Unusual amounts: Payoff totals don’t match the loan balance
- Name mismatches: Account names don’t match the lender or institution
- Repeated adjustments: Multiple last-minute updates to wiring details
- Confidentiality pressure: Requests to keep wire changes secret
Even one red flag is worth slowing down for. Speed is what scammers count on. And it’s not just title companies at risk. Law firms managing closings face the threats and responsibility to protect client funds.
Wire fraud red flags for law firms
Wire fraud is a growing threat to law firms, putting client trust, reputation, and large sums of money at risk. Attorneys handling complex, high-value deals are prime targets. Watch for these warning signs:
- Skipping protocol: Requests to avoid escrow or normal fund handling
- Avoided calls: Refusal to talk by phone; insists on email only
- Rushed closings: Unusual pressure to close quickly
- Odd statements: Errors or odd formatting in settlement paperwork
- Email lookalikes: Slight changes in familiar addresses
- Off-brand files: Unfamiliar layouts, language, or logos in attachments
Watch for deals that don’t add up, like underpriced properties or sellers without a referral. Even routine closings can hide risks, so staying alert protects your clients and your firm.
Advanced warning signs of wire fraud in real estate for businesses
Basic red flags, like mismatched names or odd amounts, are important, but busy businesses need to watch for more subtle signs that can easily slip by:
- Fake portals: Spoofed logins to steal credentials
- Deceptive domains: Slight letter swaps or added punctuation
- Tone changes: Shifts from formal to overly casual or urgent
- Verification skips: Attempts to bypass security checks
- False urgency: Emergency requests with fake deadlines
- Off-hours edits: Files created at odd times, suggesting tampering
These signs demand close attention and technical know-how, and the risk extends far beyond just businesses.
Warning signs of wire fraud for buyers and sellers
Wire fraud can feel overwhelming, especially for those unfamiliar with real estate deals. But clear warning signs often appear, if you know what to look for:
- Last-minute changes: Updates to wire instructions just before closing
- Email-only directives: Wire details sent without prior notice or phone confirmation
- Urgent requests: High-pressure push to send funds immediately
- Conflicting information: Details that don’t match earlier communications
- Language issues: Messages with odd phrasing, grammar, or spelling errors
- Unusual timing: Emails or texts sent at unusual hours
- Recipient red flags: Wire directed to a personal instead of business or escrow account
Even the most cautious buyers and sellers can be misled, especially when manual verification breaks down.
How to avoid wire fraud in real estate
Wire fraud prevention takes more than phone calls and paper checks. The most effective strategies combine technology, team training, and clear communication at every step of the transaction.
Wire fraud prevention strategies
Real estate fraud has moved beyond simple email hacks. Staying protected means layering secure tools with strong, consistent processes.
Use secure, digital platforms to verify wiring details and catch what human checks can miss.
Be sure to establish clear protocols. Set expectations early with clients. And follow the same process every time, so there’s no guesswork when it matters most.
Best practices for title companies
For title teams, strong fraud prevention comes down to process and people.
Require dual approval for wires over a set amount. Build in mandatory wait periods for any changes to wire instructions. Train staff on role-specific red flags they might face, and keep a verified list of trusted payees so you’re not starting from scratch each time.
And don’t overlook coverage. Make sure your insurance includes social engineering and wire fraud protection.
Best practices for law firms
Law firms must balance client confidentiality with strong fraud protection.
Set up client-specific verification methods instead of blanket rules. Require attorney review before any wire changes. Replace email attachments with encrypted portals, and clearly define approval authority to avoid confusion.
Above all, build processes that secure transactions without compromising privacy.
What to do if you become a victim of wire fraud
Even with strong safeguards in place, no system is foolproof. If fraud happens, knowing how to respond quickly and decisively can make all the difference.
If fraud occurs in real estate
Act immediately. Contact your bank or financial institution immediately, within minutes if possible. The sooner you alert them, the better your chances of freezing or recovering funds before they move out of reach.
Document everything. Save all emails, call logs, wire instructions, and verification steps. This record is critical for law enforcement, your insurer, and any legal follow-up.
Report properly. File a report with the FBI’s Internet Crime Complaint Center (IC3) right away. Timely reporting helps federal agencies investigate and track down fraudulent activity.
Get expert assistance. Wire fraud recovery can be complex. Consider working with professionals who specialize in fund recovery and regulatory response. Their expertise can speed the process and improve your chances of a positive outcome.
Wire fraud in real estate can be stopped
Wire fraud is one of the most damaging threats in real estate today, but it’s one you can get ahead of. With the right protections in place, you can defend your transactions, your clients, and your business from costly losses. CertifID gives you the confidence to move securely, with verified identities and insured wire transfers backed by up to $5M in direct coverage.
Want to stay informed? Subscribe to The Wire, our weekly newsletter, for real-world fraud updates, prevention tips, and expert insights.

Co-founder & Executive Chairman
Tom Cronkright is the Executive Chairman of CertifID, a technology platform designed to safeguard electronic payments from fraud. He co-founded the company in response to a wire fraud he experienced and the rising instances of real estate wire fraud. He also serves as the CEO of Sun Title, a leading title agency in Michigan. Tom is a licensed attorney, real estate broker, title insurance producer and nationally recognized expert on cybersecurity and wire fraud.
Sign up for The Wire to join the conversation.




.png)




