Email Phishing, Part 3: Examples, Real-Life Scams, and Caveats
Phishing attempts aren’t always so easy to catch: as technology becomes more advanced, so do scammers’ techniques.


Email Phishing, Part 3: Examples, Real-Life Scams, and Caveats
Phishing attempts aren’t always so easy to catch: as technology becomes more advanced, so do scammers’ techniques.




Tyler Adams
7 mins
Scams
Apr 3, 2024
Phishing attempts aren’t always so easy to catch: as technology becomes more advanced, so do scammers’ techniques. The once-obvious warning signs of typos, unofficial-looking documents, and even false URLs are easy for phishers to circumvent nowadays—and with new platforms and more targeted audiences, they can trick even the most vigilant of users.
In this post, we’ll analyze some real-life examples of successful phishing scams. By studying each carefully, you can train yourself to notice any schemes that might hit your inbox.
Document Delivery Platforms
Document-sharing has simultaneously expanded and simplified the business world, but it was only a matter of time before con artists wedged their way into it too. Networks like Dropbox, Google Docs, Docusign, and others have seen breaches of security in recent months that compromised users’ privacy, spread malware, and more.
Dropbox

- These phishing emails are sent from a generic-sounding name—or a real person the target actually knows, indicating the supposed sender also fell for the scam and had his or her account hacked, which then gave the scammers access to that person’s address book and contacts.
- Clicking on the link within, which claims the sender has a document to share with the target, will take users to a log-in page and ask for their credentials.
- Red Flags:
- URL displayed on the log-in page contains the word “dropbox” in address, but is not a Dropbox domain.
- Log-in page gives several options for your email provider, which Dropbox would not do. This is common for scams like these.
- When you click on your email provider, you are redirected to another log-in screen that looks fairly similar to the real ones Dropbox uses.
- After entering credentials, users see a “download” screen that claims the document is being opened; after that, an error message appears that states Dropbox is having difficulties. Users are then redirected to a real Dropbox page, which gives the illusion nothing out of the ordinary just occurred. In reality, the scammers can now access your Dropbox account and email, find your personal information, and spread the scam to your contacts (using you as the supposed sender).
Google Docs

- Like the Dropbox scam, this one starts with an email supposedly from someone you know. Unlike the Dropbox scam, however, clicking on the link takes you to a real Google Docs page, and asks the user to grant permission to a third-party application entitled “Google Docs,” despite the fact it is not associated with the platform (Note: since the attack, Google has placed stricter rules on third-party apps, including what words they can or cannot use in their name).
- Scammers then use your log-in credentials to obtain your personal information, including your contacts list to spread the attack.
- Red Flags:
- Hard to spot, but if you click the developer information, you can see it is not from the user you thought it was, after all.
DocuSign

- These emails’ subject lines announce alleged wire transfers, accounting invoices, and legal notices. They contain Word documents that ask users to activate the Word macro feature in order to view them; instead, users unknowingly install malware on their computer.
- Emails look quite real, and utilize social engineering—the practice of instilling fear, such as account suspension if the desired action is not taken, or the promise of rewards—like money from a wire transfer.
- Red Flags:
- Almost none. Users should be suspicious of invoices, transfers, etc. that they were not expecting (although hackers can use real domain names and references to sites like Zillow if they know you’re a realtor, or generic payment sites like Square or Paypal, which almost everyone uses at some point).
- The fact users are asked to enable a feature in Word, rather than being able to view the document immediately, is a subtle tip-off.
These are just a few of the newest scams to surface, but these—and others—could be replicated on any number of work-sharing platforms, including Airtable, Quip, SamePage, Highfive, and others. Users should exercise extreme caution when receiving documents. Hopefully, these platforms will continue to improve their security to prevent scams in the future—but don’t rely on that hope alone.
Online Banking Scams
With more and more banks turning to online services to better assist customers, scammers have even more avenues to use. By their very nature, bank-based phishing attacks utilize a powerful variation of social engineering: instilling fear in the user that they could lose their account—and access to his or her money—if they don’t comply.
Bank of America

- Users receive emails from a supposed Bank of America representative, claiming they’ve put limits on the user’s account—and the only way to fix it is for the user to click the link to confirm their account.
- Clicking the link takes the user to a very believable log-in page, which uses Bank of America’s real logo and color scheme. This page also has a log-in box with a “Secure Sign-In” heading and small lock logo, as well as a help link, enrollment link, and additional services menus—all of which might go unnoticed by the user, but subconsciously convince them the page is, in fact, real.
- Red Flags:
- After logging in, the user is required to entire a lot of personal information, including their credit card number and security code—something Bank of America will not ask for.
- The email that the user receives has poor grammar and does not address the person by name, but rather “User.”
Wells Fargo

- Source: Wells Fargo
- Using a fairly new technique known as “smishing” (SMS/text message phishing), scammers send users text messages telling them to click a link or call a number.
- Like email phishing, SMS messages use social engineering tactics to provoke panic and generate immediate response: messages say things like, “Account disabled. Call us now” or “Click the link to verify your account.” Users are afraid of losing access to their funds, and all too many will comply because of this fear.
- SMS message scams can be even more convincing than email ones, since users are unfamiliar with the risk of text phishing and might not realize it’s possible. It also eliminates the need for proper formatting and logos that emails require, since text messaging has a standard look. In short, it’s easier for scammers to craft a convincing message.
- Red Flags:
- Scammers send messages to random users, some of whom are not actually Wells Fargo members. Because it’s a large and popular bank, they hope they’ll catch enough real members before the scam is exposed.
- Sender is an email address that does not use a Wells Fargo server.
- For issues such as this, Wells Fargo and other banks will not text you—and even if they did, they would not ask for this much sensitive information.
PayPal

- Source: MalwareHelp
- Users receive an email that takes them to an account validation page. It looks very convincing, with a security verification symbol, as well as Paypal’s logo, fonts, and color scheme at the time (circa 2004). It assures the user their information will be encrypted, and links to fake privacy policy to make the user think the page is real.
- A more recent scam, however, uses similar techniques, but with updated logos, better word choices that sound more authentic (although highly vigilant users will still notice grammar errors), and even an SSL certificate on the phony pages.

Email Providers
The same tactics listed above are also used to obtain a target’s email credentials, which can give scammers access to the person’s contacts—and, potentially, their banking, shopping, or social media accounts.
Recently, various forms of “validate your account” Gmail messages have made their rounds, telling users to verify their information to avoid account suspension. They are taken to a real-looking log-in screen, and scammers use their information to access, among other things, the user’s contact list and spread malware or more validation emails. Users should take note of the URL—which is not actually a Google one—and the fact that, once they’ve entered their email address, their profile picture does not appear before they’re asked for their password.

This type of attack is especially troubling for real estate agents, who often—against the advice of brokerages and experts—use personal Google email accounts to communicate with clients. A scammer can simply find their email on a real estate site, Facebook, or LinkedIn, and tailor an attack based on that information. What’s more, it’s easy for them to then steal client details and possibly trick them into sending money and banking credentials, as well—all while pretending to be their agent.
Real Estate
While we’re on the subject of real estate scams, it’s especially important for agents to exercise caution when opening unknown/unverified emails: scammers love to target the real estate industry. A recent Zillow-based scam was sent to real estate agents, complete with authentic-looking logos, and congratulated the user on their new leads from ZillowAds, which had to be “unlocked” with their contact details and a fee of $5.00. At least one agent was tricked into providing their credit card information, and missed the only potentially obvious red flag: the fact the domain name was “Zillow.pro” instead of a .com address.
Virus Infection and Spy- or Malware Emails
Email phishers can be after more than just your password: some send viruses and malware through phony documents, usually in the hopes of infecting an entire company’s system and getting personal information for employees, partner organizations, and customers.
These viruses, once downloaded, become encrypted in several files across your computer—so that even when you do realize something’s up, it can be incredibly hard to remove the malware completely.
There’s a number of forms viruses can take, although they often look like .pdf files from within your own company or tech support departments, software updates for commonly used products like Adobe or Microsoft Office, and even—ironically—anti-virus software.
Emails with virus documents can be hard to distinguish from the real deal. They often contain a lot of “boiler plate” text such as confidentiality notices, generic liability paragraphs, etc. Like previous examples with help links and security logos, these elements are naturally ignored by most users, but still register with them on an unconscious level to make the email seem genuine.
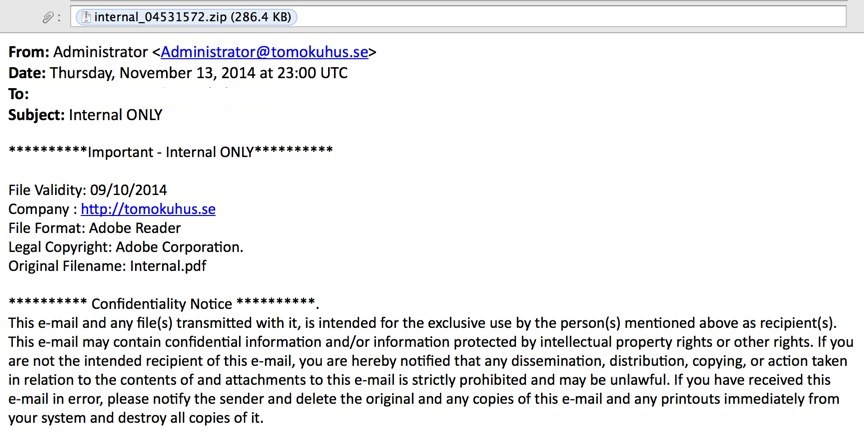
Additional Scam Types
Of course, phishing attacks can and do come in many other forms, as well: social media, shopping networks, and various providers are all valuable tools to a con artist.

- Facebook attacks go through the platform’s PM (Private Message) system, and thus don’t require special formatting like emails.
- The message warns the user their account has violated policies “that are considered annoying or insulting [to] Facebook users.” It claims the system will disable their account within 24 hours without “reconfirmation” via a URL in the message, which leads the user to a site asking for personal information.
- Red Flags:
- Poor spelling and grammar.
- External URL rather than a Facebook one.
- Dropdown menu to select your email service (ex: Gmail, AOL, etc.), which Facebook would not do.
- Asks for your credit card number, even if you’ve never used it to pay for anything on Facebook before.
Xfinity (Comcast)
- Attackers send users an email with the Xfinity logo and layout. This message claims to be a confirmation to verify you’ve authorized a payment on a credit card; since it’s a fake number, it confuses the target and entices them to click on the “View Invoice” link in the hopes of understanding or fixing the error.
- This link leads to a fake domain that prompts the user to download a .php file they believe to be the invoice. Instead, it contains a virus that infects your computer. This malware can compromise secure information stored therein.
- Red flags:
- Does not use customer’s name or account number.
- Link in the email. Providers will ask customers to visit the actual, verified webpage for the company and log into their account to address any issues, rather than linking them directly via an email.
Amazon
- Users receive an email with an Amazon Prime header that claims they’ve won free shopping points as a valued customer (even if they do not use the Prime service, or Amazon at all).
- User has to click on a link to claim the points, which takes them to a page asking for personal details.
- Red flags:
- Despite the email’s header, the address itself is not from Amazon—it just contains the word Amazon in the first portion.
- Does not use customer’s name or account details, but addresses email to simply “Shopper” and your email address.
- Poor formatting and typos, particularly unnecessary hyphens.
- Uses both aspects of social engineering: fear, and a reward. The user could allegedly receive $100 in shopping points…but only if they click the link before its expiration date and enter the required information, or the reward could be lost forever.
Stay Vigilant: Scammers Have an Unending Arsenal
This list is not exhaustive by any means; there are countless more examples of real-life phishing attacks—and, sadly, there will always be new ones surfacing, especially as new platforms come into existence. Technologies evolve rapidly, and scammers adapt just as quickly. We will, however, provide our readers with information on new tricks and tactics as they surface, so you can learn what to watch out for and how to protect yourself.
Sources:
“Beware: Another Fake Dropbox Phishing Scam.” Published by Mailguard, February 4, 2016. Accessed July 31, 2017. (Link)
Robertson, Adi. “Google Docs users hit with sophisticated phishing attack.” Published by Verge.com on May 3, 2017. Accessed July 31, 2017. (Link)
Sjouwerman, Stu. “Scam of the Week: Massive DocuSign Phishing Attacks.” Published by KnowBe4.com’s Security Awareness Training Blog, May 20, 2017. Accessed July 31, 2017. (Link)
“Beware: New Bank of America Phishing Scam Stealing Card Data.” Published by HackRead.com on July 21, 2017. Accessed July 31, 2017. (Link)
“Scam alert issued for fake Wells Fargo text.” Published by ABC-7.com, July 30, 2017. Accessed July 31, 2017. (Link)
“Screenshots of Phishing Email Messages.” Published by MalwareHelp.org. Accessed July 31, 2017.
Camp, Cameron. “PayPal users targeted in sophisticated new phishing campaign.” Published by WeLiveSecurity.com on January 27, 2017. Accessed July 31, 2017. (Link)
Sen, Abanti. “Email Scams: How to Avoid the Latest Forms of It!” Published by TechYuga on January 18, 2017. Accessed July 31, 2017. (Link)
“Email scam hawks fake Zillow leads to agents.” Published by WFG News on April 7, 2017. Accessed July 31, 2017.
“Phishing Email Causes Cryptowall 2.0 Infection.” Published by MalwareTrafficAnalysis.net on November 14, 2014. Accessed July 31, 2017. (Link)
“Phishing Scam Spreads via Facebook PM.” Published by ThreatTrack Security Labs on January 23, 2013. Accessed July 31, 2017. (Link)
“Comcast’ Phishing Email.” Published by Clicking Mad Limited. Accessed July 31, 2017.
Published by TCCPro.net, May 2015. Accessed July 31, 2017. (Link)
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.

Sign up for The Wire to join the conversation.















